To enable Secure Boots and Flash Encryption using the ESP Flash download tool
To enable secure boot and Flash encryption using the “Flash download tool” , perform the following steps:
1. Software Config
In the software “menuconfig" , disable any secure boot and Flash encryption configuration, directly compiled to generate plaintext firmware. Since Flash encryption will increases the size of the bootloader .bin firmware, the offset of the default partition table needs to be adjusted, which is 0x8000, can be adjusted to 0xa000. You can modify the settings for partition table in menuconfig. As follows:
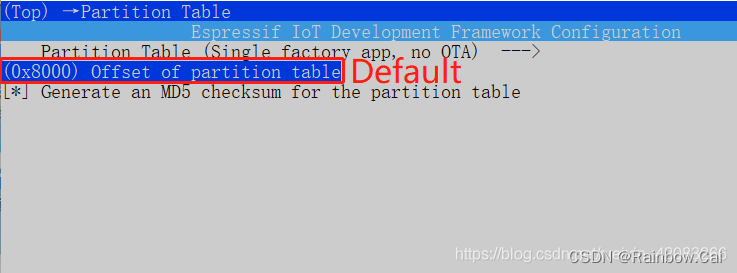
Then compile the project and check the firmware download address corresponding to the compiled firmware. You can find that the download address of the hello-world.bin becomes 0x20000
Project build complete. To flash, run this command:
E:.espressif\python_env\idf4.3_py3.8_env\Scripts\python.exe …\components\esptool_py\esptool\esptool.py -p (PORT) -b 460800 --before default_reset --after no_reset --chip esp32c3 write_flash --flash_mode dio --flash_size detect --flash_freq 80m 0x0 build\bootloader\bootloader.bin 0xa000 build\partition_table\partition-table.bin 0x20000 build\hello-world.bin
or run ‘idf.py -p (PORT) flash’
2. “Flash download tool” config
In the configuration file of the “Flash download tool” , enable the following configuration and save the file.
[SECURE BOOT]
secure_boot_en = True
[FLASH ENCRYPTION]
flash_encryption_en = True
reserved_burn_times = 3
[ENCRYPTION KEYS SAVE]
keys_save_enable = True
encrypt_keys_enable = False
encrypt_keys_aeskey_path =
[DISABLE FUNC]
jtag_disable = False
dl_encrypt_disable = False
dl_decrypt_disable = False
dl_cache_disable = False
3. Restart the “Flash download tool”
Restart the “Flash download tool” , and the following message is displayed:
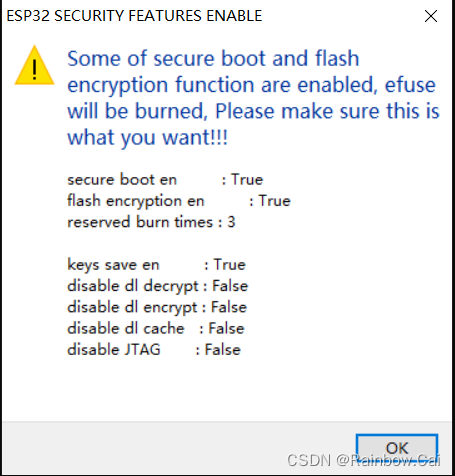
4. Download the plaintext firmware by the “Flash download tool” directly
Then, add your plaintext firmware to the “Flash download tool” and set the corresponding offset address.
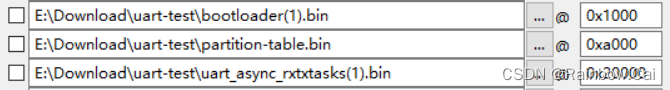
5. The plaintext firmware will be encrypted
Finally, your plaintext firmware will be encrypted directly into ciphertext firmware by using the “Flash download tool” .
test offset : 0 0x0
case ok
test offset : 0 0x0
case ok
..
Uploading stub...
Running stub...
Stub running...
Changing baud rate to 921600
Changed.
FLASH_CRYPT_CNT 0
ABS_DONE_0 False
CODING_SCHEME 0
ECDSA NIST256p private key in PEM format written to ./secure\secure_boot_key_1.pem
CODING_SCHEME 0
ECDSA NIST256p private key in PEM format written to ./secure\flash_encrypt_key_1.pem
CODING_SCHEME 0
SHA-256 digest of private key ./secure\secure_boot_key_1.pem written to ./secure\secure_boot_key_1.bin
CODING_SCHEME 0
SHA-256 digest of private key ./secure\flash_encrypt_key_1.pem written to ./secure\flash_encrypt_key_1.bin
burn secure key ...
Burn keys to blocks:
- BLOCK2 -> [4a 2a 7e e2 1b 08 27 70 a1 ee 57 cb 69 9a 7a bc 36 39 2b ed 2b a0 ab 3a e8 11 2e ec 48 c5 90 61]
Reversing the byte order
Disabling read to key block
Disabling write to key block
- BLOCK1 -> [d1 7f 51 78 e2 4b 50 5b d3 b2 b5 73 a3 c0 91 be c1 e0 b5 32 f6 84 d8 a6 f4 98 2a 86 ad fc d9 38]
Reversing the byte order
Disabling read to key block
Disabling write to key block
Burn keys in efuse blocks.
The key block will be read and write protected (no further changes or readback)
Check all blocks for burn...
idx, BLOCK_NAME, Conclusion
[00] BLOCK0 is not empty
(written ): 0x0000000400100000000018360000a200001394b555a584a800000000
(to write): 0x00000000000000000000000000000000000000000000000000030180
(coding scheme = NONE)
[01] BLOCK1 is empty, will burn the new value
[02] BLOCK2 is empty, will burn the new value
.
This is an irreversible operation!
BURN BLOCK2 - OK (write block == read block)
BURN BLOCK1 - OK (write block == read block)
BURN BLOCK0 - OK (all write block bits are set)
Reading updated efuses...
Successful
FLASH_CRYPT_CNT 0
FLASH_CRYPT_CONFIG 0
The efuses to burn:
from BLOCK0
- ABS_DONE_0
- FLASH_CRYPT_CNT
- FLASH_CRYPT_CONFIG
Burning efuses:
- 'ABS_DONE_0' (Secure boot V1 is enabled for bootloader image) 0b0 -> 0b1
- 'FLASH_CRYPT_CNT' (Flash encryption mode counter) 0b0000000 -> 0b0000001
- 'FLASH_CRYPT_CONFIG' (Flash encryption config (key tweak bits)) 0x0 -> 0xf
Check all blocks for burn...
idx, BLOCK_NAME, Conclusion
[00] BLOCK0 is not empty
(written ): 0x0000000400100000000018360000a200001394b555a584a800030180
(to write): 0x00000010f00000000000000000000000000000000000000000100000
(coding scheme = NONE)
.
This is an irreversible operation!
BURN BLOCK0 - OK (all write block bits are set)
Reading updated efuses...
Checking efuses...
Successful
WARNING: - compress and encrypt options are mutually exclusive
Will flash uncompressed
is stub and send flash finish
The efuses to burn:
Burning efuses:
Check all blocks for burn...
idx, BLOCK_NAME, Conclusion
Nothing to burn, see messages above.
Checking efuses...
Successful
6. The encryption key will saved in locally.
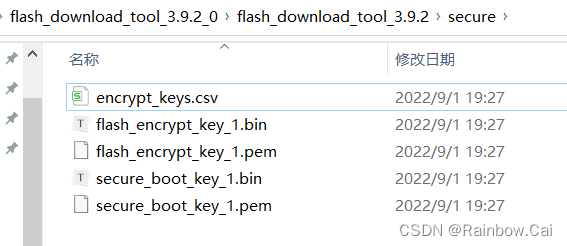
Note
-
After this operation, you can read the Flash firmware by using esptool, but read the firmware is ciphertext firmware and cannot be used properly.
-
After this operation, the module will not support re-download the firmware by the “Flash download tool”.
