TI AM62X Secure Boot 流程简述
By Toradex秦海
1). 简介
嵌入式设备对于网络安全的要求越来越高,而 Secure boot就是其中重要的一部分。 TI AM62X 处理器基于行业标准 X.509 认证来提供 Secure boot 启动过程中的 Chain of Trust; X.509 认证是基于公共密钥加密 (Public Key Cryptography) 和数字签名 (Digital Signature) 技术来实现 Secure boot 的。AM62X 处理器涉及 Security 的架构框图如下。
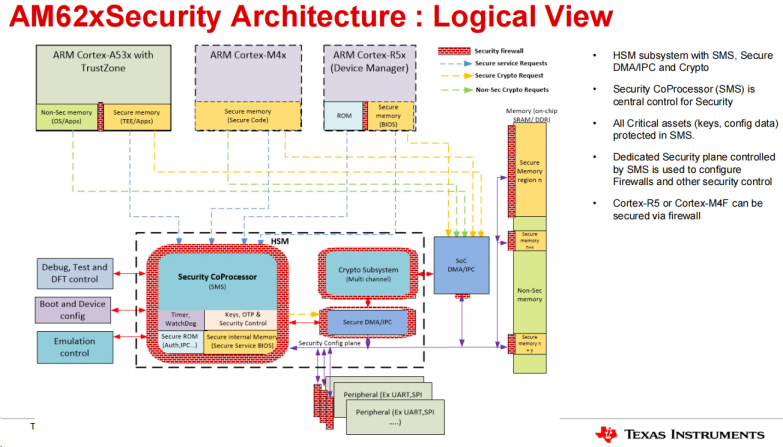
AM62X 处理器启动流程图参考如下。本文就基于 TI AM625 处理器平台简单介绍其 Secure Boot 的部署流程。
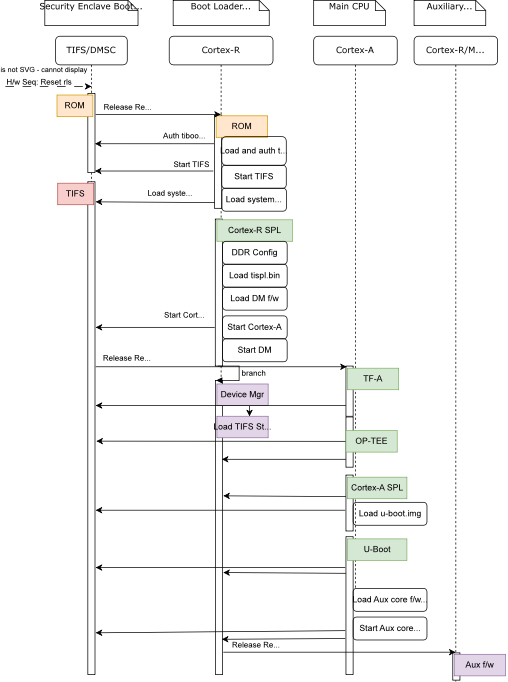
本文所演示的平台来自于 Toradex Verdin AM62 嵌入式平台,主要介绍基本的 Chain of Trust,也就是 U-boot和Linux Kernel/DTB 两个层级的加密和验证启动,后面 Rootfs 以及 Application 层面暂不涉及。
2. 准备
a). Verdin AM62 ARM核心版配合Dahlia 载板,并连接调试串口用于测试。
b). 参考这里下载 Toradex Yocto Linux BSP6 Reference Image 用于后续测试,目前最新的是 6.7.0 版本。
3). 生成 Customer Key Set 文件
a). TI AM62 处理器有如下三种设备类型,其中 GP (General Purpose) 类型的处理器是不具备支持 Secure Boot 功能的,只有 HS (High Security) 类型的处理器是支持的,然后其还细分为两个状态,HS-FS (Field Securable) 和 HS-SE (Security Enforced),具体的说明请见如下。TI AM62X HS 类型处理器出厂配置为 HS-FS 状态,且都已经预先写入了 TI Dummy Key 在设备中。
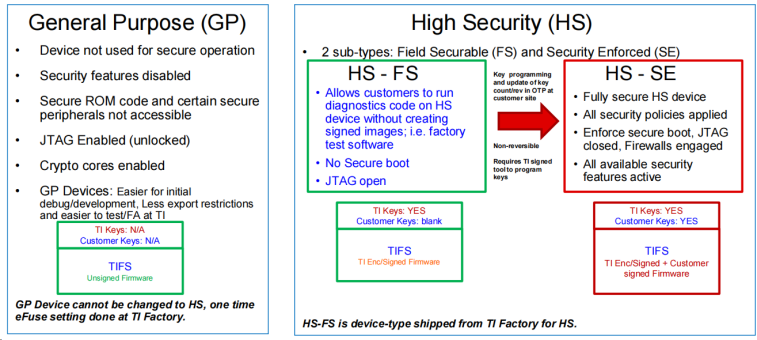
b). 由于将 HS 设备从 HS-FS 状态配置为 HS-SE 状态是不可逆的,因此本文为了方便演示流程仅仅使用 TI 预置的 Dummy Key 在 HS-FS 状态下进行 Signed Image Authentication 流程演示,但会将 Customer key 的生成和烧录流程进行说明。
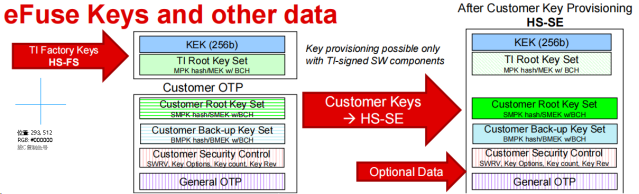
c). 通过下面命令生成 Customer Root Key Set (SMPK) 和 Customer Back-up Key Set (BMPK)文件,用于后续的 Boot Image 签名以及烧录 Image 生成。
--------------------------------
### key name should not be changed ###
$ export Customer_KEYS_DIR=<DIR to store keys>
$ export SMPK_NAME=custMpk
$ export BMPK_NAME=backMpk
### Create the SMPK key pair and certificate using RSA 4096 ###
$ cd $Customer_KEYS_DIR
$ openssl genrsa -F4 -out ${SMPK_NAME}.key 4096
$ cp ${SMPK_NAME}.key ${SMPK_NAME}.pem
$ openssl req -batch -new -x509 -key ${SMPK_NAME}.key -out ${SMPK_NAME}.crt
### Create the BMPK key pair and certificate using RSA 4096 ###
$ openssl genrsa -F4 -out ${BMPK_NAME}.key 4096
$ cp ${BMPK_NAME}.key ${BMPK_NAME}.pem
$ openssl req -batch -new -x509 -key ${BMPK_NAME}.key -out ${BMPK_NAME}.crt
### Remove write access to the keys and certificates ###
$ chmod a-w *
--------------------------------
4). Boot Image 编译和签名
a). 参考这里说明下载 Toradex Yocto Linux BSP 6.x.y 版本包含 U-boot在内的编译 Boot Images 所需要的全部源代码
--------------------------------
### Get the U-Boot source code for Yocto Linux BSP 6.x.y ###
$ git clone -b toradex_ti-u-boot-2023.04 https://git.toradex.cn/u-boot-toradex.git
$ export UBOOT_DIR=$(pwd)/u-boot-toradex
### Get the binary-only System Firmware (SYSFW) ###
$ git clone git://git.ti.com/k3-image-gen/k3-image-gen.git
$ export K3_DIR=$(pwd)/k3-image-gen
### Get the TI Linux Firmware ###
$ git clone -b ti-linux-firmware git://git.ti.com/processor-firmware/ti-linux-firmware.git
$ export TI_LINUX_FW_DIR=$(pwd)/ti-linux-firmware
### Get the ARM Trusted Firmware (ATF/TF-A) ###
$ git clone https://github.com/ARM-software/arm-trusted-firmware.git
$ export TFA_DIR=$(pwd)/arm-trusted-firmware
### Get the OP-TEE image source code ###
$ git clone https://github.com/OP-TEE/optee_os.git
$ export OPTEE_DIR=$(pwd)/optee_os
### Get the K3 Security development package:###
$ git clone https://git.ti.com/git/security-development-tools/core-secdev-k3.git -b master
$ export CORE_SECDEV_K3_DIR=$(pwd)/core-secdev-k3
--------------------------------
b). Customer Key Set 需要部署在 K3 Security development package 和 U-Boot source code 如下位置,默认部署的是 TI Dummy Key,本文因为都是基于 TI Dummy Key 进行测试,因此不做替换修改。
./ K3 Security development package
--------------------------------
$ cd $CORE_SECDEV_K3_DIR/keys
$ ls
custMpk.crt custMpk.key custMpk.pem swrv.txt ti-degenerate-key.pem
$ md5sum custMpk.key
bd90ee9fe69667315eeee32bc7a01b39 custMpk.key
$ md5sum custMpk.pem
bd90ee9fe69667315eeee32bc7a01b39 custMpk.pem
$ md5sum custMpk.crt
f2a1562c002fc38319bf82471b0661a3 custMpk.crt
### replace TI Dummy Key with Customer Key if needed ###
$ cp $Customer_KEYS_DIR/* $CORE_SECDEV_K3_DIR/keys
--------------------------------
./ U-Boot source code
--------------------------------
$ cd $UBOOT_DIR/board/ti/keys/
$ ls
custMpk.crt custMpk.key custMpk.pem swrv.txt ti-degenerate-key.pem
$ md5sum custMpk.key
bd90ee9fe69667315eeee32bc7a01b39 custMpk.key
$ md5sum custMpk.pem
bd90ee9fe69667315eeee32bc7a01b39 custMpk.pem
$ md5sum custMpk.crt
f2a1562c002fc38319bf82471b0661a3 custMpk.crt
### replace TI Dummy Key with Customer Key if needed ###
$ cp $Customer_KEYS_DIR/* $CORE_SECDEV_K3_DIR/keys
--------------------------------
c). 参考这里配置交叉编译 toolchain,注意由于不同的固件需要对应 32bit 或者 64bit toolchain 编译器,因此这里两种 toolchain 都需要配置,配置完成后参考如下命令 export 32bit/64bit toolchain 相应的环境变量。
--------------------------------
### 64bit toolchain env ###
$ export ARCH=arm64
$ export DTC_FLAGS="-@"
$ export PATH=~/gcc-linaro-aarch64/bin/:$PATH
$ export CROSS_COMPILE=aarch64-none-linux-gnu-
### 32bit toolchain env ###
$ export PATH=~/gcc-linaro-arm/bin/:$PATH
--------------------------------
d). 参考这里对 Boot Images 进行编译
./ Build ARM Trusted Firmware (ATF/TF-A)
--------------------------------
$ cd $TFA_DIR
$ export ARCH=arm64 CROSS_COMPILE=aarch64-none-linux-gnu-
$ unset TFA_EXTRA_ARGS
$ make PLAT=k3 SPD=opteed $TFA_EXTRA_ARGS TARGET_BOARD=lite
--------------------------------
./ Build OP-TEE Image
--------------------------------
$ cd $OPTEE_DIR
$ export OPTEE_EXTRA_ARGS="CFG_WITH_SOFTWARE_PRNG=y"
$ export ARCH=arm
$ export CROSS_COMPILE=arm-none-linux-gnueabihf-
$ export CROSS_COMPILE64=aarch64-none-linux-gnu-
$ make PLATFORM=k3-am62x CFG_ARM64_core=y $OPTEE_EXTRA_ARGS
--------------------------------
./ Build U-Boot for R5
--------------------------------
### Step-1 under U-boot directory ###
$ cd $UBOOT_DIR
$ make ARCH=arm CROSS_COMPILE=arm-none-linux-gnueabihf- verdin-am62_r5_defconfig
$ make ARCH=arm CROSS_COMPILE=arm-none-linux-gnueabihf- BINMAN_INDIRS=$TI_LINUX_FW_DIR
### Step-2 under System Firmware directory ###
$ cd $K3_DIR
$ make SOC=am62x SOC_TYPE="hs-fs" TI_SECURE_DEV_PKG=$CORE_SECDEV_K3_DIR SBL=$UBOOT_DIR/spl/u-boot-spl.bin SYSFW_DIR=$TI_LINUX_FW_DIR/ti-sysfw
$ cp tiboot3-am62x-hs-fs-evm.bin ../tiboot3-am62x-hs-fs-verdin.bin
--------------------------------
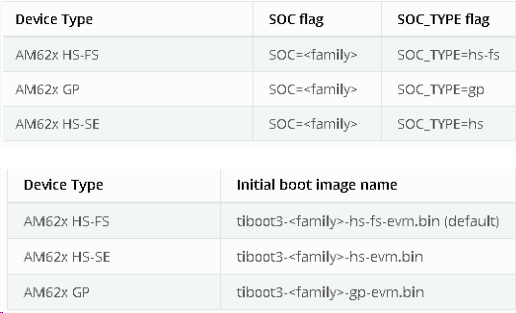
// 对应不同的 SOC_TYPE 选项,会生成不同的 Binary Image,其对应关系参考如下两个表格,在出厂默认的 HS-FS SoC Type 下,需要编译HS-FS 对应的固件;而一旦通过 TI OTP Keywriter 工具将 Customer Key 写入 eFUSE 并将设备配置为 HS-SE 状态后,就需要编译 HS-SE SOC Type 对应的固件才能正常启动了。
./ Build U-Boot for A53
--------------------------------
### Default configuration ###
$ cd $UBOOT_DIR
$ export ARCH=arm64 CROSS_COMPILE=aarch64-none-linux-gnu-
$ make verdin-am62_a53_defconfig
### Customized configuration to force FIT image to be authenticated ###
$ make menuconfig
CONFIG_FIT_SIGNATURE_ENFORCE=y
### Compile ###
$ make BINMAN_INDIRS=$TI_LINUX_FW_DIR \
BL31=$TFA_DIR/build/k3/lite/release/bl31.bin \
TEE=$OPTEE_DIR/out/arm-plat-k3/core/tee-raw.bin
$ cp tispl.bin ../
$ cp u-boot.img ../
--------------------------------
5). 签名Linux kernel FIT Image
a). 此步骤为可选步骤,如果不需要强制 FIT Image Authentication 则在上面 4.d Build U-Boot for A53 步骤中可以不使能 CONFIG_FIT_SIGNATURE_ENFORCE 配置,然后跳过此章节直接进行 BSP Image 修改部署章节即可。
b). 解压 Toradex Ycoto Linux BSP6 Image,获得 LInux Kernel/DTB/DTBO 等文件
--------------------------------
### uncompress BSP Image package ###
$ tar xvf Verdin-AM62_Reference-Minimal-Image-Tezi_6.7.0+build.13.tar
$ cd Verdin-AM62_Reference-Minimal-Image-Tezi_6.7.0+build.13/
### uncompress boot filesystem ###
$ mkdir bootfs/
$ tar Jxf Reference-Minimal-Image-verdin-am62.bootfs.tar.xz -C bootfs/
### copy kernel/dtb/dtbo image fit image work folder ###
$ export FIT_IMAGE_DIR=<fit_image_work_folder>
$ cd bootfs/
$ cp -r * $FIT_IMAGE_DIR
--------------------------------
c). 修改 FIT Image 描述文件,一个示例说明部分如下,需要根据你实际存放 Linux Kernel/DTB/DTBO 文件的位置来修改文件 “data” 参数本文使用的完整描述文件模板请从这里下载。
./ fitImage-its--6.1.83+git0+0a32d33d5f-r0-verdin-am62-20240701094251.its
--------------------------------
/dts-v1/;
/ {
description = "Kernel fitImage for TDX Wayland with XWayland/6.1.83+gitAUTOINC+0a32d33d5f/verdin-am62";
#address-cells = <1>;
images {
kernel-1 {
description = "Linux kernel";
data = /incbin/("$FIT_IMAGE_DIR/Image.gz");
type = "kernel";
arch = "arm64";
os = "linux";
compression = "gzip";
load = <0x80200000>;
entry = <0x80200000>;
hash-1 {
algo = "sha512";
};
};
fdt-ti_k3-am625-verdin-nonwifi-dahlia.dtb {
description = "Flattened Device Tree blob";
data = /incbin/("$FIT_IMAGE_DIR/k3-am625-verdin-nonwifi-dahlia.dtb");
type = "flat_dt";
arch = "arm64";
compression = "none";
load = <0x83000000>;
hash-1 {
algo = "sha512";
};
};
...
...
--------------------------------
d). 生成 FIT Image
./ 由于在生成 FIT Image 的时候需要同时将 Public Key 信息嵌入到 u-boot.dtb,因此这里需要找到 U-Boot 默认的 dtb 文件。根据 U-Boot 编译 default configuration 来确认默认的 dtb 文件即为 "arch/arm/dts/k3-am625-verdin-wifi-dev.dtb"
--------------------------------
$ vi $UBOOT_DIR/configs/verdin-am62_a53_defconfig
...
CONFIG_DEFAULT_DEVICE_TREE="k3-am625-verdin-wifi-dev"
...
--------------------------------
./ 在 FIT Image work folder 通过下面命令生成签名的 FIT Image
--------------------------------
$ mkimage -f fitImage-its--6.1.83+git0+0a32d33d5f-r0-verdin-am62-20240701094251.its -k $UBOOT_DIR/board/ti/keys -K $UBOOT_DIR/arch/arm/dts/k3-am625-verdin-wifi-dev.dtb -r fitImage
--------------------------------
e). 根据 4.d Build U-Boot for A53 步骤,不修改任何 configuration的情况下,重新编译 U-Boot Image
--------------------------------
$ cd $UBOOT_DIR
### Compile ###
$ make BINMAN_INDIRS=$TI_LINUX_FW_DIR \
BL31=$TFA_DIR/build/k3/lite/release/bl31.bin \
TEE=$OPTEE_DIR/out/arm-plat-k3/core/tee-raw.bin
$ cp tispl.bin ../
$ cp u-boot.img ../
--------------------------------
6). 修改和部署 Yocto Linux BSP
a). 使用 4.d Build U-Boot for R5 步骤生成的 “tiboot3-am62x-hs-fs-verdin.bin” 文件和 5.e 步骤重新编译生成的 “tispl.bin” 和 “u-boot.img” 文件修改 Yocto Linux BSP 对应的 Boot Images 文件
--------------------------------
$ cd Verdin-AM62_Reference-Minimal-Image-Tezi_6.7.0+build.13/
$ rm tiboot3-am62x-hs-fs-verdin.bin tispl.bin u-boot.img
$ cp .../tiboot3-am62x-hs-fs-verdin.bin .
$ cp .../tispl.bin .
$ cp .../u-boot.img .
--------------------------------
b). 将 5.d 步骤生成的 FIT Image 部署到刚才解压的Ycoto Linux BSP6 bootfs中,并重新创建bootfs 压缩包
--------------------------------
### copy FIT image to bsp rootfs folder ###
$ cp $$FIT_IMAGE_DIR/fitImage .../Verdin-AM62_Reference-Minimal-Image-Tezi_6.7.0+build.13/bootfs/
### remove default Linux kernel/dtb/dtbo files ###
$ cd .../Verdin-AM62_Reference-Minimal-Image-Tezi_6.7.0+build.13/bootfs/
$ rm -rf Image.gz k3-am625-verdin-* overlays
### check bootfs files ###
$ tree -L 1
.
├── boot.scr
├── fitImage
└── overlays.txt
### compress new bootfs package ###
$ tar Jcf ../Reference-Minimal-Image-verdin-am62.bootfs.tar.xz *
### clear bootfs
$ cd ..
$ rm -rf bootfs/
--------------------------------
c). 修改BSP package中的 “u-boot-initial-env-sd” 文件,增加如下环境变量用于使能 U-Boot 加载 FIT Image 来启动
--------------------------------
--- a/u-boot-initial-env-sd 2024-07-01 18:00:22.000000000 +0800
+++ b/u-boot-initial-env-sd 2024-09-12 16:35:02.000000000 +0800
@@ -30,6 +30,7 @@
kernel_addr_r=0x88200000
kernel_comp_addr_r=0x80200000
kernel_comp_size=0x08000000
+kernel_image=fitImage
load_efi_dtb=load ${devtype} ${devnum}:${distro_bootpart} ${fdt_addr_r} ${prefix}${efi_fdtfile}
loadaddr=0x88200000
mmc_boot=if mmc dev ${devnum}; then devtype=mmc; run scan_dev_for_boot_part; fi
--------------------------------
d). 需要注意的是由于Kernel阶段的Secure Boot相关认证和加载都是基于U-Boot 环境变量来实现的, 因此如果要让这个启动机制更加安全可靠,则要让U-Boot保持在上述安全启动路径,而不能通过其他启动介质或者脚本来启动而绕开 Secure Boot,比如 Toradex U-Boot默认是使能 Distro Boot 功能的,可以自动扫描外设介质的启动脚本,那么这个功能就需要关闭掉,类似这样的 U-Boot 定制化和启动路径固化可以参考如下文章,本文不做进一步介绍。
Security Hardening of U-Boot | Toradex Developer Center
e). 如果你的 Linux BSP Image 是通过 Yocto Project 编译生成,那么如下是一个 Toradex Security Meta Layer,你可以直接将其集成到你的 Yocto Project 编译环境中,然后按照说明配置后直接生成签名甚至加密好的 BSP Image。
GitHub - toradex/meta-toradex-security
7). 部署测试
a). 参考这里将上述制作完成数字签名的 BSP Image通过 Toradex Easy Installer 更新到 Verdin AM62 模块。因为本文测试基于 TI 已经预先烧写到 SoC 的 dummy key,所以可以直接启动测试,如果是使用 Customized Key,则还需要参考后续 eFuse 烧写操作将 Customized Key 烧写到 SoC 才能正确验证并启动。
./ 启动后查看启动log,可以看到 Boot Images 和 Linux FIT Image (Kernel Image/DTB/DTBO) Secure Boot验证签名成功并最终完整启动
--------------------------------
U-Boot SPL 2023.04-28170-gc997b1b09fb (Sep 10 2024 - 17:41:33 +0800)
SYSFW ABI: 4.0 (firmware rev 0x000a '10.0.8--v10.00.08 (Fiery Fox)')
Changed A53 CPU frequency to 1250000000Hz (T grade) in DT
SPL initial stack usage: 13472 bytes
Trying to boot from MMC1
Authentication passed // ATF authentication
Authentication passed // TEE authentication
Authentication passed // DM-FW authentication
Loading Environment from nowhere... OK
init_env from device 9 not supported!
Authentication passed // A53 SPL authentication
Authentication passed // A53 SPL DTB authentication
Starting ATF on ARM64 core...
NOTICE: BL31: v2.11.0(release):v2.10.0-1555-g8e9bdc5b1
NOTICE: BL31: Built : 17:04:05, Aug 30 2024
...
U-Boot SPL 2023.04-28170-gc997b1b09fb (Sep 12 2024 - 16:56:27 +0800)
SYSFW ABI: 4.0 (firmware rev 0x000a '10.0.8--v10.00.08 (Fiery Fox)')
SPL initial stack usage: 1904 bytes
Trying to boot from MMC1
Authentication passed // A53 u-boot authentication
Authentication passed // A53 u-boot DTB authentication
U-Boot 2023.04-28170-gc997b1b09fb (Sep 12 2024 - 16:56:27 +0800)
SoC: AM62X SR1.0 HS-FS
DRAM: 1 GiB
Core: 143 devices, 31 uclasses, devicetree: separate
...
Found U-Boot script /boot.scr
6003 bytes read in 10 ms (585.9 KiB/s)
## Executing script at 90280000
82 bytes read in 9 ms (8.8 KiB/s)
8918270 bytes read in 78 ms (109 MiB/s)
Bootargs: root=PARTUUID=33e36968-02 ro rootwait console=tty1 console=ttyS2,115200 consol0
## Loading kernel from FIT Image at 90300000 ...
Using 'conf-ti_k3-am625-verdin-wifi-dev.dtb' configuration
Verifying Hash Integrity ... sha512,rsa4096:custMpk+ OK // Kernel Image authentication
Trying 'kernel-1' kernel subimage
Description: Linux kernel
Type: Kernel Image
Compression: gzip compressed
Data Start: 0x90300108
Data Size: 8305029 Bytes = 7.9 MiB
Architecture: AArch64
OS: Linux
Load Address: 0x80200000
Entry Point: 0x80200000
Hash algo: sha512
Hash value: 1eae3ec7c7d250d709d07f8af174e8de9c2293a9a61683f1f1a4f5981e96dc9ab090cc
Verifying Hash Integrity ... sha512+ OK
## Loading fdt from FIT Image at 90300000 ...
Using 'conf-ti_k3-am625-verdin-wifi-dev.dtb' configuration
Verifying Hash Integrity ... sha512,rsa4096:custMpk+ OK // Kernel DTB authentication
Trying 'fdt-ti_k3-am625-verdin-wifi-dev.dtb' fdt subimage
...
Verifying Hash Integrity ... sha512+ OK
Loading fdt from 0x90b40bd0 to 0x83000000
## Loading fdt from FIT Image at 90300000 ...
Using 'conf-verdin-am62_dsi-to-hdmi_overlay.dtbo' configuration
Verifying Hash Integrity ... sha512,rsa4096:custMpk+ OK // DTBO authentication
Trying 'fdt-verdin-am62_dsi-to-hdmi_overlay.dtbo' fdt subimage
...
Verifying Hash Integrity ... sha512+ OK
## Loading fdt from FIT Image at 90300000 ...
Using 'conf-verdin-am62_spidev_overlay.dtbo' configuration
Verifying Hash Integrity ... sha512,rsa4096:custMpk+ OK // DTBO authentication
Trying 'fdt-verdin-am62_spidev_overlay.dtbo' fdt subimage
...
Verifying Hash Integrity ... sha512+ OK
Booting using the fdt blob at 0x83000000
Working FDT set to 83000000
Uncompressing Kernel Image
Loading Device Tree to 0000000098ec8000, end 0000000098edc6b5 ... OK
Working FDT set to 98ec8000
Starting kernel ...
[ 0.000000] Booting Linux on physical CPU 0x0000000000 [0x410fd034]
[ 0.000000] Linux version 6.1.83-6.7.0+git.0a32d33d5fb7 (oe-user@oe-host) (aarch64-td4
[ 0.000000] Machine model: Toradex Verdin AM62 WB on Verdin Development Board
...
--------------------------------
b). AM62x SoC eFuse 烧写以及将设备从 HS-FS 转换为 HS-SE 状态
./ eFuse 烧写流程详细烧写流程可以参考这里。
./ 首先下载安装最新 TI MCU+ SDK,以及对应版本的 CCS 和 sysconfig 工具到 Linux 开发主机 <MCU_PLUS_SDK_INSTALL_DIR> (推荐为 ${HOME}/ti/ ) 目录,详细过程参考上面的文章链接。
./ 安装 TI OTP Keywriter 工具软件和使用指南,这些是 secure 资料,需要在 TI 网站上面注册申请通过后才能获取。安装路径为 <MCU_PLUS_SDK_INSTALL_DIR>/mcu_plus_sdk_am62x_10_00_00_14/source/security。OTP Keywriter 的详细使用指南文档是 AM62X_OTP_Keywriter_User_Guide。
--------------------------------
$ tree -L 2 ~/ti/mcu_plus_sdk_am62x_10_00_00_14/source/security/
/home/simon/ti/mcu_plus_sdk_am62x_10_00_00_14/source/security/
├── sbl_keywriter
│ ├── am62x-sk
│ ├── boardcfgs
│ ├── keywr_bin
│ ├── manifest
│ ├── scripts
│ └── tools
├── uninstall
└── uninstall.dat
--------------------------------
./ 生成 X.509 Certificate
// Keywriter 预置 TI dummy key,因此如果是基于 TI dummy key set 进行生成,则命令如下。注意 “--keyrev” 参数,只要这个参数被烧写到了 eFuse 上面,那么这个设备就立即转化为 HS-SE 状态,所有 secure boot 限制将都生效,设备也无法再次刷写其他 key 信息,因此此过程可以分步或者一次进行,前期测试阶段建议分步,先烧写 key,进行验证通过后,再进行 keyrev 烧写,将设备变更为 HS-SE 状态。
--------------------------------
### Generate X.509 certificate ###
### Option-1, step by step
$ cd <MCU_PLUS_SDK_INSTALL_DIR>/mcu_plus_sdk_am62x_10_00_00_14/source/security/sbl_keywriter/scripts/cert_gen/am62x
## Generate certificate for programming MSV(Model Specific Value) and TI dummy key sets, but not turn device into HS-SE
$ ./gen_keywr_cert.sh -t tifek/ti_fek_public.pem --msv 0xC0FFE -b-def --bmek-def -s-def --smek-def --keycnt 2
## Generates certificate for setting the program key revision to 1
./gen_keywr_cert.sh -t tifek/ti_fek_public.pem --keyrev 1
### Option-2, one-shot
## programming MSV, key sets, and turn device into HS-SE in one shot command
$ ./gen_keywr_cert.sh -t tifek/ti_fek_public.pem --msv 0xC0FFE -b-def --bmek-def -s-def --smek-def --keycnt 2 --keyrev 1
### Convert certificate binary to .h format ###
$ cd <MCU_PLUS_SDK_INSTALL_DIR>/mcu_plus_sdk_am62x_10_00_00_14/source/security/sbl_keywriter/scripts/x509cert
$ python3 ../../../../../tools/bin2c/bin2c.py final_certificate.bin keycert.h KEYCERT 2024
--------------------------------
// 如果是基于 customized key set,则要将相关命令修改如下:
--------------------------------
### Copy customized key set for keywriter ###
$ cd <MCU_PLUS_SDK_INSTALL_DIR>/mcu_plus_sdk_am62x_10_00_00_14/source/security/sbl_keywriter/scripts/cert_gen/am62x
$ cp $Customer_KEYS_DIR/custMpk.key keys_devel/smek.key
$ cp $Customer_KEYS_DIR/custMpk.pem keys_devel/smpk.pem
$ cp $Customer_KEYS_DIR/backMpk.key keys_devel/bmek.key
$ cp $Customer_KEYS_DIR/backMpk.pem keys_devel/bmpk.pem
### Generate X.509 certificate ###
### Option-1, step by step
$ cd <MCU_PLUS_SDK_INSTALL_DIR>/mcu_plus_sdk_am62x_10_00_00_14/source/security/sbl_keywriter/scripts/cert_gen/am62x
## Generate certificate for programming MSV(Model Specific Value) and TI dummy key sets, but not turn device into HS-SE
$ ./gen_keywr_cert.sh -t tifek/ti_fek_public.pem --msv 0xC0FFE -b keys_devel/bmpk.pem --bmek keys_devel/bmek.key -s keys_devel/smpk.pem --smek keys_devel/smek.key --keycnt 2
## Generates certificate for setting the program key revision to 1
./gen_keywr_cert.sh -t tifek/ti_fek_public.pem --keyrev 1
### Option-2, one-shot
## programming MSV, key sets, and turn device into HS-SE in one shot command
$ ./gen_keywr_cert.sh -t tifek/ti_fek_public.pem --msv 0xC0FFE -b keys_devel/bmpk.pem --bmek keys_devel/bmek.key -s keys_devel/smpk.pem --smek keys_devel/smek.key --keycnt 2 --keyrev 1
### Convert certificate binary to .h format ###
$ cd <MCU_PLUS_SDK_INSTALL_DIR>/mcu_plus_sdk_am62x_10_00_00_14/source/security/sbl_keywriter/scripts/x509cert
$ python3 ../../../../../tools/bin2c/bin2c.py final_certificate.bin keycert.h KEYCERT 2024
--------------------------------
./ 生成 keywriter binary - tiboot3.bin
--------------------------------
### create compiler soft link ###
$ cd <MCU_PLUS_SDK_INSTALL_DIR>
$ ln -s ccs1271/ccs/tools/compiler/ti-cgt-armllvm_3.2.2.LTS ti-cgt-armllvm_3.2.2.LTS
### Generate binary ###
$ cd <MCU_PLUS_SDK_INSTALL_DIR>/mcu_plus_sdk_am62x_10_00_00_14/source/security/sbl_keywriter/am62x-sk/r5fss0-0_nortos/ti-arm-clang
$ make -sj clean PROFILE=debug
$ make -sj PROFILE=debug
--------------------------------
./ 将 tiboot3.bin 通过 USB DFU 模式加载运行起来,具体的命令可以参考这里,只是需要注意的是由于烧写 eFuse 的过程中还需要 AM62X SoC VPP 管脚上拉到 1.8V 同时具备至少 400mA 瞬态电流负载能力,因此需要在载板上面部署相应的硬件设计,以保证仅在烧写 eFuse 的时候拉高 VPP 管脚同时提供足够的瞬变电流,而在其他任何时候 VPP 管脚都是拉低的状态。参考如下 TI AM62 SK 开发板设计,如图一布置了一个单独的 LDO 电源芯片(TLV75518PDQNR) 来给 VPP 管脚提供 400mA/1.8V 供电,正式由于极高的瞬变电流负载需求,load switch 或者 DC/DC 电源是不建议使用的;而 LDO 的开关则通过 VPP_LDO_EN 信号来控制。如图二,则是 AM62X SoC 通过 I2C 总线连接了一个 GPIO Expander 芯片来扩展 GPIO 管脚提供 VPP_LDO_EN 信号控制。
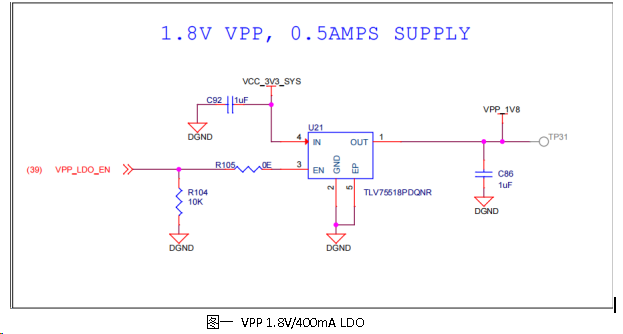
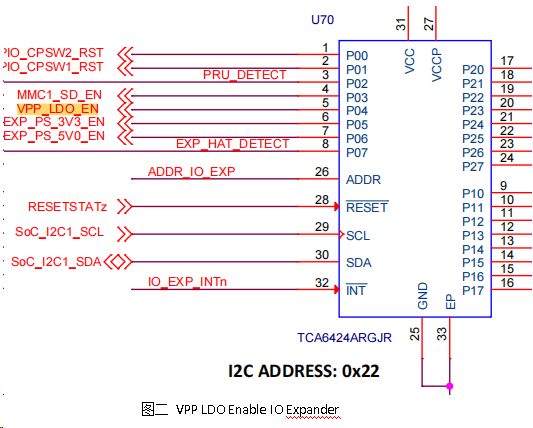
// 对于 IO Expander VPP_LDO_EN GPIO 管脚的控制软件代码请参考 MCU+ SDK 如下文件,你也可以根据你的实际载板设计来相应修改适配。
<MCU_PLUS_SDK_INSTALL_DIR>/mcu_plus_sdk_am62x_10_00_00_14/source/security/sbl_keywriter/am62x-sk/r5fss0-0_nortos/board.c
8). 总结
本文基于 TI AM62X 处理器简单演示了 Secure Boot 流程,涉及 Boot Images 和 Linux Kernel/DTB ,至于 Rootfs 的加密,则需要配置类似 Squashfs 只读文件系统配合 Initramfs RAM Disk 镜像进行加解密挂载启动,可以结合参考如下两篇文章和相关 meta-toradex-security layer 数据参考,本文不做具体测试。
./ 嵌入式 ARM 平台使用dm-crypt加密磁盘分区
./ 使用Squashfs和Overlayfs提高嵌入式Linux文件系统可靠性
./ GitHub - toradex/meta-toradex-security
