8.6 11.25-11.27
11.25 配置防盗链
背景:
一个免费论坛,所有人可以在该论坛上申请免费的站点,用户运营网站不需要购买服务器或维护程序,只需要在免费的论坛平台上申请一个论坛,申请后用户自主运营网站;
问题:
从一段时间开始,服务器的流量剧烈增长
分析:
定位大流量的服务器,然后抓包分析,发现日志无异常但流量中存在大量图片信息,且对应的包中的referer信息固定(即用户从固定的某站点跳转到了本站点);
发现了一个可疑站点,该站点的服务器在台湾,属于×××网站,放在论坛站点的图片属于×××图片;
我们的论坛站点可以免费无限制的上传图片,对方将图片放在论坛站点,并在另一个网站引用,即对方将黄图放在了我们论坛的服务器上,服务器在国内,图片访问较快,而对方的网站主体放在了台湾,用户访问时获得的×××图片实际上是从在国内的我方论坛的服务器发出的;
对于我们没有意义,流量上升,但用户不会增加;
操作:
1 删除所有×××
2 配置防盗链(跳转访问本站点时若referer信息不是认识的referer则不允许访问)
图片访问地址为a域名,b域名引用了a域名的图片,这样不被允许;
指定图片只能在a域名,则图片可以被控制在我们的服务器上;
第三方站点无法引用;
配置防盗链:
[root@hyc-01-01 ~]# vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
…
<VirtualHost *:80>
DocumentRoot "/data/wwwroot/111.com"
ServerName 111.com
ServerAlias www.example.com
<Directory /data/wwwroot/111.com/*>
AllowOverride AuthConfig
AuthName "111.com user auth"
AuthType Basic
AuthUserFile /data/.htpasswd
require valid-user
</Directory>
<Directory /data/wwwroot/111.com>
SetEnvIfNoCase Referer "http://111.com" local_ref 设置该referer为白名单
SetEnvIfNoCase Referer "http://aaa.com" local_ref
#SetEnvIfNoCase Referer "^$" local_ref 将空referer设为白名单
<filesmatch "\.(txt|doc|mp3|zip|rar|jpg|gif|png)"> 将.txt/.doc等这样的访问设置为白名单,即针对此类访问设置防盗链
Order Allow,Deny 行为:先allow,后deny
Allow from env=local_ref 允许以上设置的三个站点即allow,其余deny
</filesmatch>
<Directory>
<IfModule mod_expires.c>
ExpiresActive on
ExpiresByType image/gif "access plus 1 days"
ExpiresByType text/css "now plus 2 hours"
…
测试:
[root@hyc-01-01 ~]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@hyc-01-01 ~]# /usr/local/apache2.4/bin/apachectl graceful
空referer(请求baidu.png时的信息中没有携带referer):
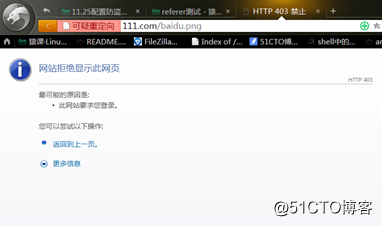
referer为http://ask.apelearn.com:

在curl测试时指定referer信息:
[root@hyc-01-01 111.com]# curl -e "http://ttt.com/tty" -x 192.168.31.129:80 111.com/baidu.png -I
HTTP/1.1 403 Forbidden
Date: Tue, 07 Aug 2018 11:30:50 GMT
Server: Apache/2.4.34 (Unix) PHP/7.1.6
Content-Type: text/html; charset=iso-8859-1
-e指定访问时携带的referer信息
[root@hyc-01-01 111.com]# curl -e "http://111.com/tty" -x 192.168.31.129:80 111.com/baidu.png -I
HTTP/1.1 200 OK
Date: Tue, 07 Aug 2018 11:32:08 GMT
Server: Apache/2.4.34 (Unix) PHP/7.1.6
Last-Modified: Wed, 06 Jun 2018 16:15:03 GMT
ETag: "105e0-56dfb781defc0"
Accept-Ranges: bytes
Content-Length: 67040
Cache-Control: max-age=86400
Expires: Wed, 08 Aug 2018 11:32:08 GMT
Content-Type: image/png
[root@hyc-01-01 111.com]# curl -e "http://aaa.com/tty" -x 192.168.31.129:80 111.com/baidu.png -I
HTTP/1.1 200 OK
Date: Tue, 07 Aug 2018 11:33:50 GMT
Server: Apache/2.4.34 (Unix) PHP/7.1.6
Last-Modified: Wed, 06 Jun 2018 16:15:03 GMT
ETag: "105e0-56dfb781defc0"
Accept-Ranges: bytes
Content-Length: 67040
Cache-Control: max-age=86400
Expires: Wed, 08 Aug 2018 11:33:50 GMT
Content-Type: image/png
curl命令中指定referer时一定要以http://开头
11.26 访问控制Directory
问题:
部分http的内容(网页、图片等)仅针对公司内部,对外不开放,做用户认证可能会泄露账号密码,存在安全隐患
解决方案:
限制ip访问指定的内容,只有白名单的ip才能访问
比如假设公司公网ip固定,则可以将公司的固定公网ip加入白名单,其他公网ip访问将受到限制
被限制的ip为源ip
配置:
[root@hyc-01-01 logs]# vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
…
<Directory /data/wwwroot/111.com/admin/>
Order deny,allow
执行规则时无论是否匹配到对应的ip都会从头到尾匹配完所有规则,再根据最后匹配的规则决定allow或deny;
Order后先写deny,后写allow,则执行规则时会先执行deny的规则,后执行allow,执行allow、deny的顺序与order有关,与deny、allow的排列顺序无关;
比如这里先执行deny,此时127.0.0.1被deny,后执行allow,127.0.0.1又被allow,则最终127.0.0.1被allow;
Deny from all
Allow from 127.0.0.1
</Directory>
…
[root@hyc-01-01 logs]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@hyc-01-01 logs]# /usr/local/apache2.4/bin/apachectl graceful
测试:
创建测试内容:
[root@hyc-01-01 admin]# vim index.php
[root@hyc-01-01 admin]# ls
index.php
[root@hyc-01-01 admin]# pwd
/data/wwwroot/111.com/admin
测试:
[root@hyc-01-01 admin]# curl -x 192.168.31.129:80 111.com/admin/index.php -I
HTTP/1.1 403 Forbidden
Date: Tue, 07 Aug 2018 13:15:25 GMT
Server: Apache/2.4.34 (Unix) PHP/7.1.6
Content-Type: text/html; charset=iso-8859-1
[root@hyc-01-01 admin]# curl -x 127.0.0.1:80 111.com/admin/index.php -I
HTTP/1.1 200 OK
Date: Tue, 07 Aug 2018 13:15:40 GMT
Server: Apache/2.4.34 (Unix) PHP/7.1.6
X-Powered-By: PHP/7.1.6
Cache-Control: max-age=0
Expires: Tue, 07 Aug 2018 13:15:40 GMT
Content-Type: text/html; charset=UTF-8
[root@hyc-01-01 logs]# tail 111.com-access_20180807.log
192.168.31.129 - - [07/Aug/2018:21:15:25 +0800] "HEAD HTTP://111.com/admin/index.php HTTP/1.1" 403 - "-" "curl/7.29.0"
127.0.0.1 - - [07/Aug/2018:21:15:40 +0800] "HEAD HTTP://111.com/admin/index.php HTTP/1.1" 200 - "-" "curl/7.29.0"
192.168.31.1 - - [07/Aug/2018:21:20:09 +0800] "GET /admin/index.php HTTP/1.1" 403 224 "-" "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET4.0C; .NET4.0E; InfoPath.3)" 192.168.31.129和127.0.0.1、192.168.31.1均为源ip
403为限制访问,404为找不到内容
11.27 访问控制FilesMatch
不匹配目录,匹配某个网页执行策略
操作:
[root@hyc-01-01 logs]# vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
…
<Directory /data/wwwroot/111.com/admin/>
<FilesMatch index.php(.*)>
Order deny,allow
Deny from all
Allow from 127.0.0.1
</FilesMatch>
</Directory>
…
测试:
[root@hyc-01-01 admin]# curl -x192.168.31.129:80 'http://111.com/admin/index.php'
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>403 Forbidden</title> 访问被拒绝
</head><body>
<h1>Forbidden</h1>
<p>You don't have permission to access /admin/index.php
on this server.<br />
</p>
</body></html>
[root@hyc-01-01 admin]# curl -x192.168.31.129:80 'http://111.com/admin/aaa.php'
12345qwert 访问正常
[root@hyc-01-01 admin]# curl -x127.0.0.1:80 'http://111.com/admin/index.php' -I
HTTP/1.1 200 OK 根据策略,127.0.0.1被允许访问http://111.com/admin/index.php
Date: Tue, 07 Aug 2018 14:15:22 GMT
Server: Apache/2.4.34 (Unix) PHP/7.1.6
X-Powered-By: PHP/7.1.6
Cache-Control: max-age=0
Expires: Tue, 07 Aug 2018 14:15:22 GMT
Content-Type: text/html; charset=UTF-8
转载于:https://blog.51cto.com/12216458/2155944
