httpd搭建虚拟主机、设置访问认证以及https相关的用法
场景:
分别使用httpd-2.2和httpd-2.4实现
1、建立httpd服务,要求:
(1) 提供两个基于名称的虚拟主机www1, www2;有单独的错误日志和访问日志;
(2) 通过www1的/server-status提供状态信息,且仅允许tom用户访问;
(3) www2不允许192.168.0.0/24网络中任意主机访问;
2、为上面的第2个虚拟主机提供https服务;
以下将会演示分别在CentOS 6和CentOS 7上搭建httpd,并实现对web的访问控制以及https,在CentOS 6上使用的是httpd2.2,CentOS 7上使用的是httpd2.4。
CentOS 6上搭建http和httpsf服务:
第一部分:搭建httpd服务
1、先配置好yum源,用于安装httpd2.2
]# yum install httpd -y
2、在/etc/httpd/conf.d/创建2个虚拟主机所用的文件名称分别为vhosts1.conf、vhosts2.conf
vhosts1.conf的内容为
<VirtualHost 172.16.6.6:80> ServerName www1 DocumentRoot /data/vhosts/www1 CustomLog logs/www1-access_log combined ErrorLog logs/www1-error_log </VirtualHost> vhosts2.conf的内容为 <VirtualHost 172.16.6.6:80> ServerName www2 DocumentRoot /data/vhosts/www2 CustomLog logs/www2-access_log combined ErrorLog logs/www2-error_log </VirtualHost> 3、需要将httpd的主配置文件/etc/httpd/conf/httpd.conf中的NameVirtualHost指定注释去掉,设置为 NameVirtualHost 172.16.6.6:80 否则,启动时会有警告 4、启动httpd服务 [root@localhost ~]# service httpd start Starting httpd: [ OK ]
5、由于需要在www1上能够查看httpd的状态,所以需要httpd支持status_module模块,查看当前是否有支持的模块:
[root@localhost ~]# httpd -M | grep status status_module (shared)
能出现以上提示就说明能支持查看httpd的运行状态信息
6、创建测试页并进行测试网页,即在/data/vhosts/www1和/data/vhosts/www2下创建测试页
[root@localhost ~]# echo www1 > /data/vhosts/www1/index.html [root@localhost ~]# echo www2 > /data/vhosts/www2/index.html 测试: [root@localhost ~]# curl http://www1 www1 [root@localhost ~]# curl http://www2 www2 出现显示www1和www2,则说明两个虚拟主机工作正常 7、设置基于basic的访问控制,在/etc/httpd/conf.d/vhosts1.conf中添加内容,添加后的显示如下: <VirtualHost 172.16.6.6:80> ServerName www1 DocumentRoot /data/vhosts/www1 CustomLog logs/www1-access_log combined ErrorLog logs/www1-error_log <Location /server-status> SetHandler server-status AuthType basic AuthUserFile "/etc/httpd/.htpasswd" AuthName "Dangerous,it's only administrator area." Require User tom </Location> </VirtualHost> 设置访问相关的文件,用以存储用户tom登录时用到的信息: [root@localhost ~]# htpasswd -c -m /etc/httpd/.htpasswd tom New password: Re-type new password: Adding password for user tom /etc/httpd/.htpasswd为稍后登录时用到的存储tom账号和密码的文件。 检查之前所添加的文件是否有语法错误:
[root@localhost ~]# httpd -t
Syntax OK 说明语法检查正常,没有出现错误
让httpd重载配置文件:
[root@localhost ~]# service httpd reload Reloading httpd:
分别测试http://www1和http://www1/server-status页面
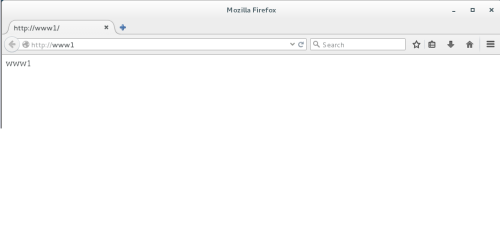
显示http://www1访问正常。
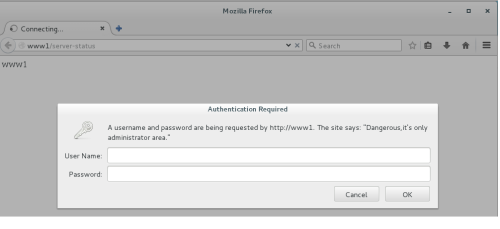
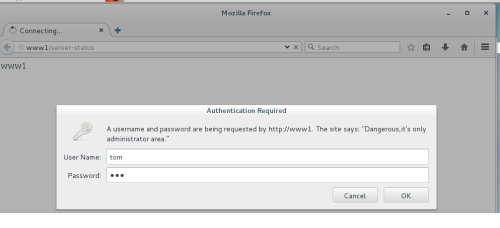
测试http://www1/server-status需要基于basic认证,需要输入用户tom的账号和密码才可以登录,输入之前设置tom的账号和密码后就可以显示内容了,登录后显示如下
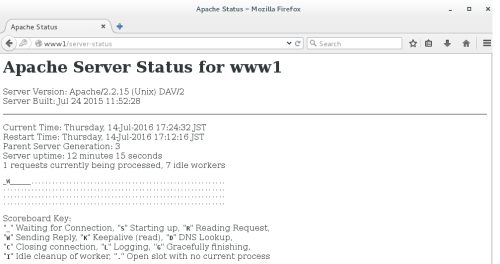
至此,基于basic认证的虚拟主机www1以完成,接下来将完成虚拟主机www2的设置
8、设置www2禁止某个ip段访问,比如192.168.0.0,也可以禁止某一ip访问
<VirtualHost 172.16.6.6:80> ServerName www2 DocumentRoot /data/vhosts/www2 CustomLog logs/www2-access_log combined ErrorLog logs/www2-error_log <Directory "/data/vhosts/www2"> Options None AllowOverride None Order deny,allow deny from 192.168.0 deny from 172.16.6.3 </Directory> </VirtualHost> 之后,检查下文件的语法,并重新加载配置文件: [root@localhost ~]# httpd -t Syntax OK [root@localhost ~]# service httpd reload Reloading httpd: 这边在172.16.6.3上测试对www2的访问,显示禁止: [root@centos7 ~]# curl -I http://www2 HTTP/1.1 403 Forbidden Date: Thu, 14 Jul 2016 08:44:22 GMT Server: Apache/2.2.15 (CentOS) Accept-Ranges: bytes Content-Length: 4961 Connection: close Content-Type: text/html; charset=UTF-8 第二部分:配置虚拟主机www2能提供https服务 1、https是调用ssl库进行,所以首先需要安装下ssl的模块 [root@localhost ~]# yum install mod_ssl 2、这边先用一台机器 172.16.6.1作为CA,并对提供https服务的机器提供证书签发 使用172.16.6.1创建为私有CA: [root@localhost ~]# (umask 077; openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048) Generating RSA private key, 2048 bit long modulus .............................+++ ...........+++ e is 65537 (0x10001) 生成自签证书: [root@localhost ~]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 3650 3、虚拟主机www2上生成私钥,然后生成证书申请,并发给私有CA 172.16.6.1 [root@localhost ~]# mkdir /etc/httpd/ssl [root@localhost ~]# (umask 077 ; openssl genrsa -out /etc/httpd/ssl/httpd.key 1024) 创建证书用到的数据库文件: [root@localhost CA]# touch index.txt [root@localhost CA]# echo 01 > serial 将证书申请发给CA: [root@localhost ~]# scp /etc/httpd/ssl/httpd.csr 172.16.6.1:/etc/pki/CA/newcerts/ root@172.16.6.1's password: httpd.csr CA签署证书: [root@localhost CA]# openssl ca -in /etc/pki/CA/newcerts/httpd.csr -out /etc/pki/CA/certs/httpd.crt -days 365 100% 676 0.7KB/s 00:00 签署截图如下:
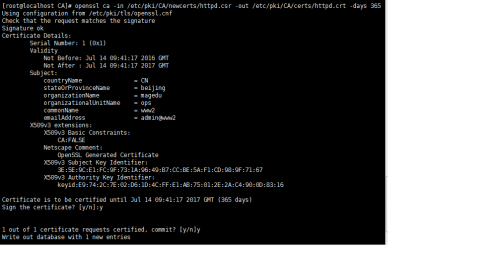
4、将此证书发给虚拟主机www2,并修改ssl的配置文件/etc/httpd/conf.d/ssl.conf
[root@localhost ~]# scp /etc/pki/CA/certs/httpd.crt 172.16.6.6:/etc/httpd/ssl/ 将修改以下几项: DocumentRoot "/data/vhosts/www2" ServerName www2:443 SSLCertificateFile /etc/httpd/ssl/httpd.crt SSLCertificateKeyFile /etc/httpd/ssl/httpd.key 验证修改的文件是否有语法错误,并重新加载配置: [root@localhost httpd]# httpd -t Syntax OK [root@localhost httpd]# service httpd reload Reloading httpd: 5、测试虚拟主机www2的https服务是否能正常访问
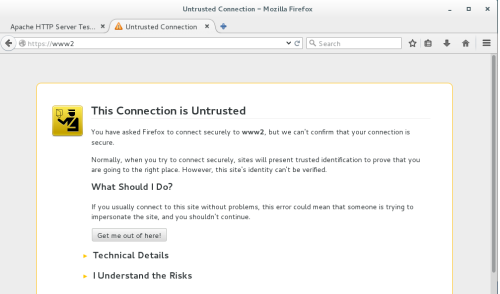
显示无法验证证书,由于CA的证书还未导入到浏览器
这边还提供一个测试办法:将CA证书发到测试的机器上,并用CA证书进行测试,如下
[root@centos7 ~]# curl --cacert /root/cacert.pem https://www2 www2
显示结果为虚拟主机www2的证书通过了验证。并得以显示
在CentOS 7上的httpd2.4的实现
第一部分:虚拟主机的构建及相关的访问策略
1、配置yum源,安装httpd
[root@centos7 ~]# yum install httpd -y
2、创建虚拟主机www1和虚拟主机www2,由于httpd2.4是默认拒绝访问的,所以需在配置文件中指定运行访问,否则访问一直都是拒绝的,在/etc/httpd/conf.d/的vhosts1.conf和vhosts2.conf的内容分别为:
<VirtualHost 172.16.6.3:80> ServerName www1 DocumentRoot /data/vhosts/www1 CustomLog logs/www1-access_log combined ErrorLog logs/www1-error_log <Directory "/data/vhosts/www1"> Options None AllowOverride None Require all granted </Directory> </VirtualHost> <VirtualHost 172.16.6.3:80> ServerName www2 DocumentRoot /data/vhosts/www2 CustomLog logs/www2-access_log combined ErrorLog logs/www2-error_log <Directory "/data/vhosts/www2"> Options None AllowOverride None Require all granted </Directory> </VirtualHost>
3、在虚拟主机www1的配置文件/etc/httpd/conf.d/vhosts1.conf中修改访问控制,仅允许tom访问查看虚拟主机的,内容如下:
<VirtualHost 172.16.6.3:80> ServerName www1 DocumentRoot /data/vhosts/www1 CustomLog logs/www1-access_log combined ErrorLog logs/www1-error_log <Directory "/data/vhosts/www1"> Options None AllowOverride None Require all granted </Directory> <Location /server-status> SetHandler server-status AuthType basic AuthUserFile "/etc/httpd/.htpasswd" AuthName "Dangerous,it's administrator's aread" Require user tom </Location> </VirtualHost>
这边测试Require user tom中的user不支持大写User,但CentOS 6可以支持
4、创建认证所用到的文件.htpasswd
[root@centos7 conf.d]# htpasswd -c -m /etc/httpd/.htpasswd tom
5、创建2个虚拟主机所用到的首要index.html文件
[root@centos7 conf.d]# echo www1 > /data/vhosts/www1/index.html [root@centos7 conf.d]# echo www2 > /data/vhosts/www2/index.html
6、测试之前修改的配置文件是否有语法错误,并启动httpd服务
[root@centos7 conf.d]# echo www1 > /data/vhosts/www1/index.html [root@centos7 conf.d]# echo www2 > /data/vhosts/www2/index.html [root@centos7 conf.d]# httpd -t Syntax OK [root@centos7 conf.d]# systemctl start httpd.service
7、测试虚拟主机www1的访问如下:
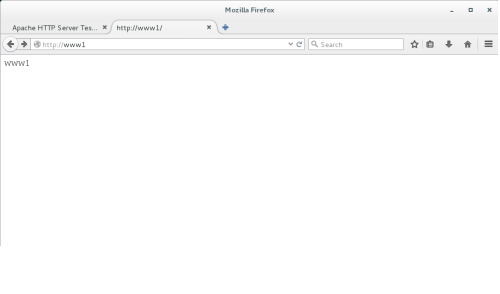
测试http://www1/server-status页面如下:
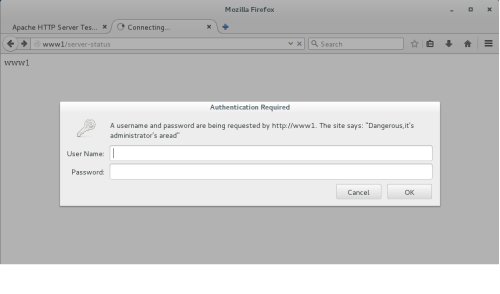
输入账号tom和密码后显示如下:
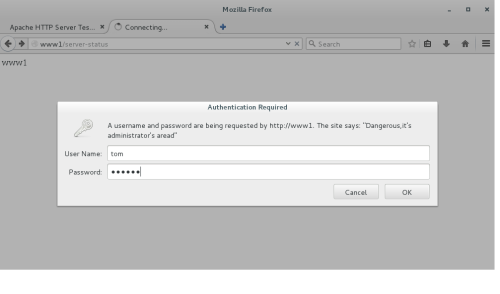
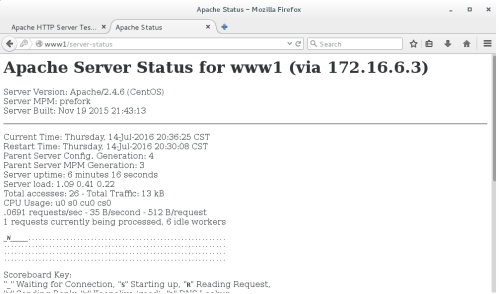
8、 下面将设置虚拟主机www2的限制某一个IP段的访问和某个ip的访问,虚拟主机www2的配置文件内容如下:
<VirtualHost 172.16.6.3:80> ServerName www2 DocumentRoot /data/vhosts/www2 CustomLog logs/www2-access_log combined ErrorLog logs/www2-error_log <Directory "/data/vhosts/www2"> <RequireALL> Require not ip 192.168.0 Require not ip 172.16.6.2 Require all granted </RequireAll> </Directory> </VirtualHost>
在172.16.6.2中测试如下:
[root@www ~]# curl -I http://www2 HTTP/1.1 403 Forbidden Date: Thu, 14 Jul 2016 13:04:10 GMT Server: Apache/2.4.6 (CentOS) Last-Modified: Thu, 16 Oct 2014 13:20:58 GMT ETag: "1321-5058a1e728280" Accept-Ranges: bytes Content-Length: 4897 Content-Type: text/html; charset=UTF-8
在本机172.16.6.3中测试如下:
[root@centos7 conf.d]# curl http://www2 www2 [root@centos7 conf.d]# curl -I http://www2 HTTP/1.1 200 OK Date: Thu, 14 Jul 2016 13:05:14 GMT Server: Apache/2.4.6 (CentOS) Last-Modified: Thu, 14 Jul 2016 11:56:38 GMT ETag: "5-5379731c96238" Accept-Ranges: bytes Content-Length: 5 Content-Type: text/html; charset=UTF-8
9、下面将为虚拟主机www2设置https服务,过程也是同CentOS 6,先生成私钥,然后生成证书请求并发给私有CA,这里的私有CA是172.16.6.1,让私有CA签发证书发回虚拟主机www2
[root@centos7 ~]# mkdir /etc/httpd/ssl [root@centos7 ~]# (umask 077 ; openssl genrsa -out /etc/httpd/ssl/httpd.key 1024) [root@centos7 ~]# openssl req -new -key /etc/httpd/ssl/httpd.key -out /etc/httpd/ssl/httpd.csr -days 365 [root@centos7 ~]# scp /etc/httpd/ssl/httpd.csr 172.16.6.1:/etc/pki/CA/newcerts/ 在CA上签署证书,并将签署过的证书发回: [root@localhost CA]# openssl ca -in /etc/pki/CA/newcerts/httpd.csr -out /etc/pki/CA/certs/httpd.crt -days 365 [root@localhost CA]# scp /etc/pki/CA/certs/httpd.crt 172.16.6.3:/etc/httpd/ssl/
10、在虚拟主机上安装ssl模块,并对ssl的配置文件进行配置
[root@centos7 httpd]# yum install mod_ssl -y
对ssl的配置文件/etc/httpd/conf.d/ssl.conf进行配置,httpd2.4默认deny的,所以需要在ssl的配置文件中显示的定义允许访问权限,如下:
DocumentRoot "/data/vhosts/www2" ServerName www2:443 SSLCertificateFile /etc/httpd/ssl/httpd.crt SSLCertificateKeyFile /etc/httpd/ssl/httpd.key <Directory "/data/vhosts/www2"> Require all granted </Directory>
11、对以上的配置文件进行语法检查并重新让httpd加载配置文件
[root@centos7 httpd]# httpd -t Syntax OK [root@centos7 httpd]# systemctl reload httpd.service
12、对https进行测试,浏览器还未导入CA的证书,就无法识别虚拟主机的证书,结果如下:
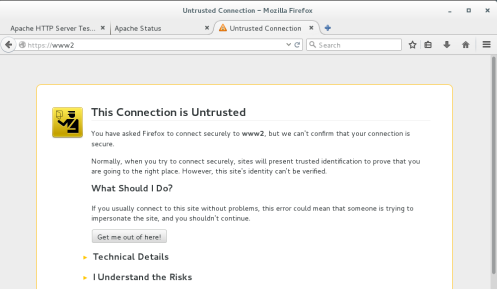
或可以用CA的证书对https进行测试,需将CA的证书发到需要测试的机器上,这边提前将CA的证书传到要测试的机器上了
[root@centos7 httpd]# curl --cacert /etc/httpd/cacert.pem https://www2 www2
到此处,在CentOS 6和CentOS 7上的httpd设置虚拟主机和web的访问认证,以及https的设置已测试完成。
转载于:https://blog.51cto.com/yy0430/1826472
