CDH 08Cloudera Manager freeIPAKerberos安装配置(markdown新版)
文章目录
- 一、配置Kerberos
- 1、配置krb5.conf凭据缓存
- 2、配置kadm5.acl
- 3、freeIPA重启服务
- 4、验证freeIPA KDC
- 5、安装freeIPA客户端(除cdh-ipa-v01服务器)
- 6、其它节点修改krb5.conf配置文件
- 1)配置krb5.conf
- 2)分发其它节点
- 3)验证(cdh-ipa-v01服务器)
- 7、证书颁发存储
- 1)建根CA的目录结构
- 2)配置openssl.cnf文件
- 3)创建root钥匙
- 4)创建root证书
- 5)验证root 钥匙
- 8、Intermediate CA目录
- 1)创建一个intermediate目录存放CA
- 2)创建Intermediate CA目录
- 3)配置openssl.cnf文件
- 3)创建 intermediate钥匙
- 4)创建intermediate证书签名
- 5)创建intermediate证书
- 6)验证intermediate证书
- 7)验证intermediate证书,验证通过返回OK
- 8)创建证书链文件
一、配置Kerberos
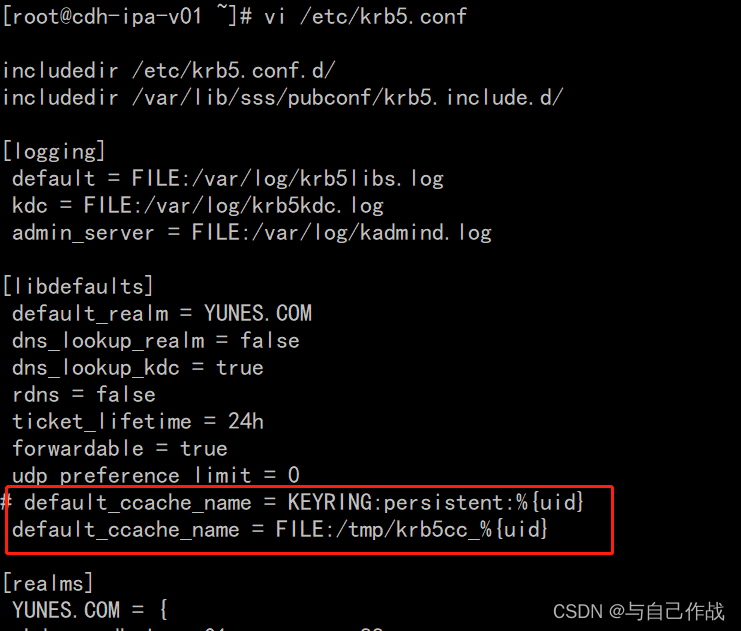
1、配置krb5.conf凭据缓存
vi /etc/krb5.conf
[root@cdh-ipa-v01 ~]# vi /etc/krb5.conf
includedir /etc/krb5.conf.d/
includedir /var/lib/sss/pubconf/krb5.include.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = YUNES.COM
dns_lookup_realm = false
dns_lookup_kdc = true
rdns = false
ticket_lifetime = 24h
forwardable = true
udp_preference_limit = 0
# default_ccache_name = KEYRING:persistent:%{uid}
default_ccache_name = FILE:/tmp/krb5cc_%{uid}
[realms]
YUNES.COM = {
kdc = cdh-ipa-v01.yunes.com:88
master_kdc = cdh-ipa-v01.yunes.com:88
admin_server = cdh-ipa-v01.yunes.com:749
default_domain = yunes.com
pkinit_anchors = FILE:/var/lib/ipa-client/pki/kdc-ca-bundle.pem
pkinit_pool = FILE:/var/lib/ipa-client/pki/ca-bundle.pem
}
[domain_realm]
.yunes.com = YUNES.COM
yunes.com = YUNES.COM
cdh-ipa-v01.yunes.com = YUNES.COM
[dbmodules]
YUNES.COM = {
db_library = ipadb.so
}
[plugins]
certauth = {
module = ipakdb:kdb/ipadb.so
enable_only = ipakdb
}
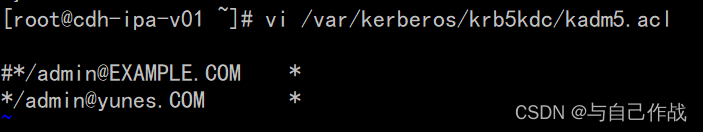
2、配置kadm5.acl
vi /var/kerberos/krb5kdc/kadm5.acl
[root@cdh-ipa-v01 ~]# vi /var/kerberos/krb5kdc/kadm5.acl
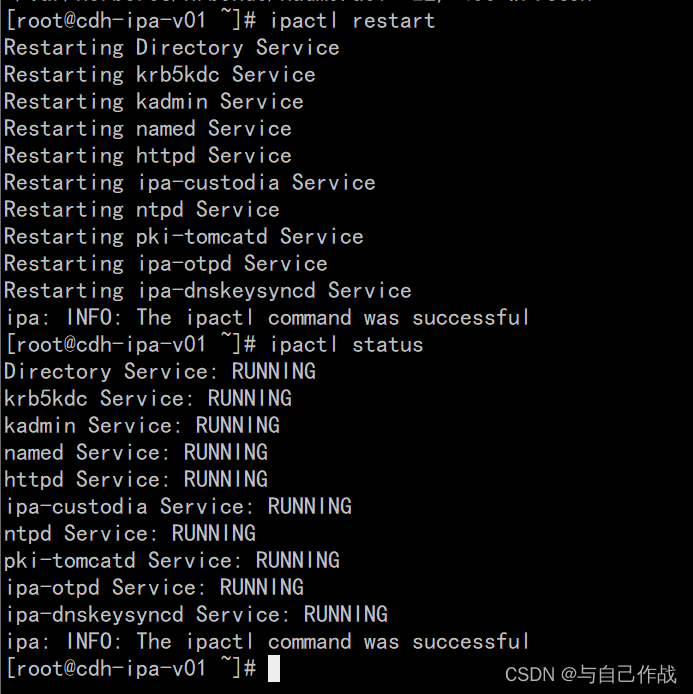
3、freeIPA重启服务
ipactl restart
[root@cdh-ipa-v01 ~]# ipactl restart
[root@cdh-ipa-v01 ~]# ipactl restart
Restarting Directory Service
Restarting krb5kdc Service
Restarting kadmin Service
Restarting named Service
Restarting httpd Service
Restarting ipa-custodia Service
Restarting ntpd Service
Restarting pki-tomcatd Service
Restarting ipa-otpd Service
Restarting ipa-dnskeysyncd Service
ipa: INFO: The ipactl command was successful
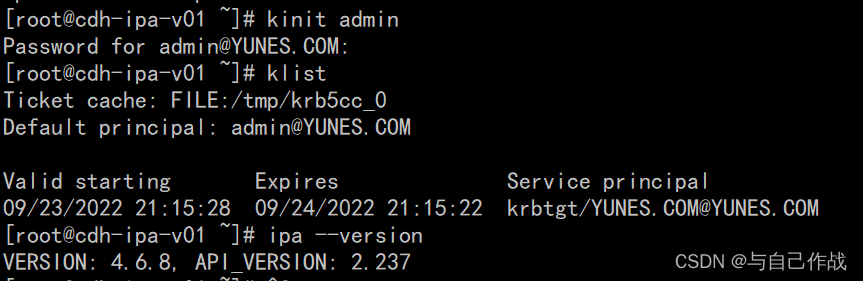
4、验证freeIPA KDC
kinit admin
[root@cdh-ipa-v01 ~]# kinit admin
[root@cdh-ipa-v01 ~]# klist
[root@cdh-ipa-v01 ~]# ipa --version
[root@cdh-ipa-v01 ~]# kinit admin
Password for admin@YUNES.COM: adminrootROOT@1234
[root@cdh-ipa-v01 ~]# klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: admin@YUNES.COM
Valid starting Expires Service principal
09/23/2022 21:15:28 09/24/2022 21:15:22 krbtgt/YUNES.COM@YUNES.COM
[root@cdh-ipa-v01 ~]# ipa --version
VERSION: 4.6.8, API_VERSION: 2.237
5、安装freeIPA客户端(除cdh-ipa-v01服务器)
ipa-client-install --domain=yunes.com
–server=cdh-ipa-v01.yunes.com
–realm=YUNES.COM
–principal=admin@YUNES.COM
–password=adminrootROOT@1234
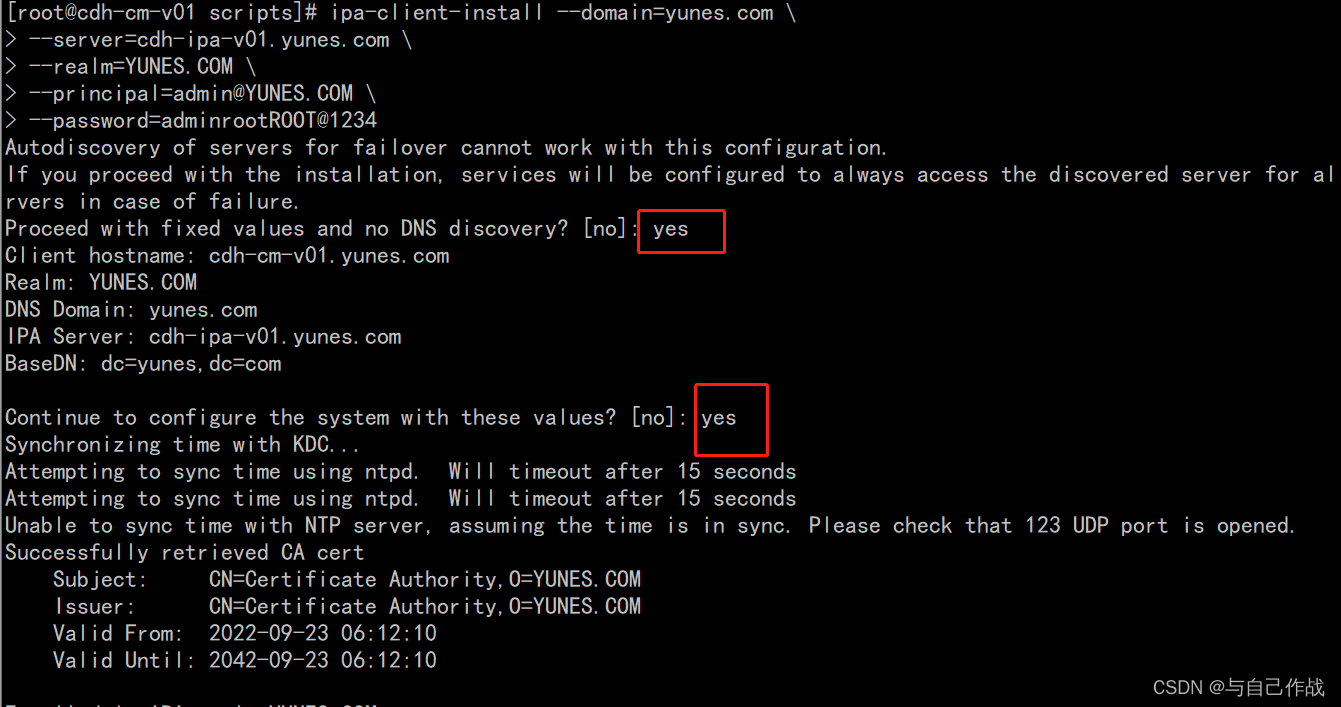
[root@cdh-cm-v01 scripts]# ipa-client-install --domain=yunes.com \
> --server=cdh-ipa-v01.yunes.com \
> --realm=YUNES.COM \
> --principal=admin@YUNES.COM \
> --password=adminrootROOT@1234
Autodiscovery of servers for failover cannot work with this configuration.
If you proceed with the installation, services will be configured to always access the discovered server for all operations and will not fail over to other servers in case of failure.
Proceed with fixed values and no DNS discovery? [no]: yes
Client hostname: cdh-cm-v01.yunes.com
Realm: YUNES.COM
DNS Domain: yunes.com
IPA Server: cdh-ipa-v01.yunes.com
BaseDN: dc=yunes,dc=com
Continue to configure the system with these values? [no]: yes
Synchronizing time with KDC...
Attempting to sync time using ntpd. Will timeout after 15 seconds
Attempting to sync time using ntpd. Will timeout after 15 seconds
Unable to sync time with NTP server, assuming the time is in sync. Please check that 123 UDP port is opened.
Successfully retrieved CA cert
Subject: CN=Certificate Authority,O=YUNES.COM
Issuer: CN=Certificate Authority,O=YUNES.COM
Valid From: 2022-09-23 06:12:10
Valid Until: 2042-09-23 06:12:10
Enrolled in IPA realm YUNES.COM
Created /etc/ipa/default.conf
New SSSD config will be created
Configured sudoers in /etc/nsswitch.conf
Configured /etc/sssd/sssd.conf
Configured /etc/krb5.conf for IPA realm YUNES.COM
trying https://cdh-ipa-v01.yunes.com/ipa/json
[try 1]: Forwarding 'schema' to json server 'https://cdh-ipa-v01.yunes.com/ipa/json'
trying https://cdh-ipa-v01.yunes.com/ipa/session/json
[try 1]: Forwarding 'ping' to json server 'https://cdh-ipa-v01.yunes.com/ipa/session/json'
[try 1]: Forwarding 'ca_is_enabled' to json server 'https://cdh-ipa-v01.yunes.com/ipa/session/json'
Systemwide CA database updated.
Hostname (cdh-cm-v01.yunes.com) does not have A/AAAA record.
Adding SSH public key from /etc/ssh/ssh_host_rsa_key.pub
Adding SSH public key from /etc/ssh/ssh_host_ecdsa_key.pub
Adding SSH public key from /etc/ssh/ssh_host_ed25519_key.pub
[try 1]: Forwarding 'host_mod' to json server 'https://cdh-ipa-v01.yunes.com/ipa/session/json'
SSSD enabled
Configured /etc/openldap/ldap.conf
NTP enabled
Configured /etc/ssh/ssh_config
Configured /etc/ssh/sshd_config
Configuring yunes.com as NIS domain.
Client configuration complete.
The ipa-client-install command was successful
6、其它节点修改krb5.conf配置文件
1)配置krb5.conf
vi /etc/krb5.conf
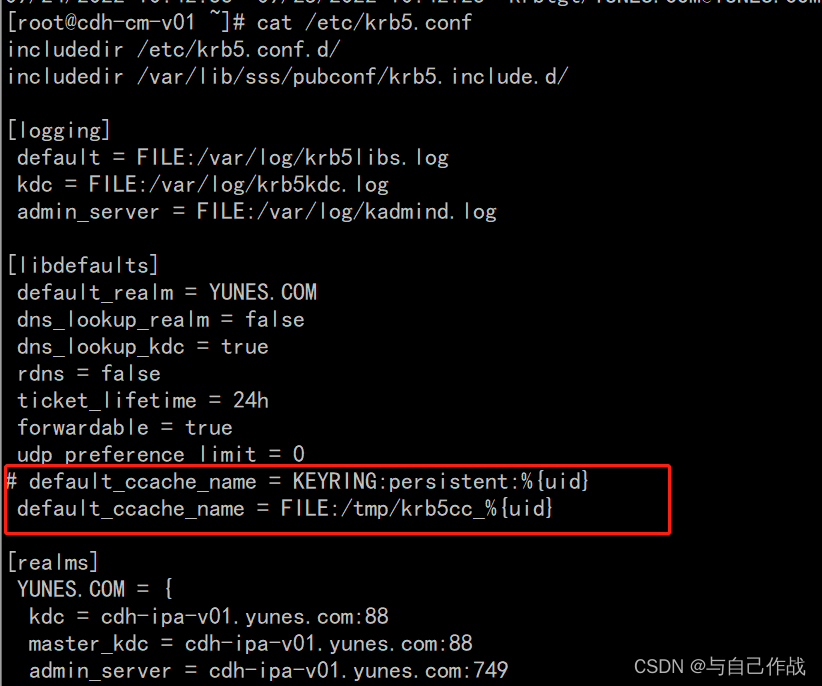
[root@cdh-cm-v01 .ssh]# vi /etc/krb5.conf
[root@cdh-cm-v01 .ssh]# vi /etc/krb5.conf
includedir /etc/krb5.conf.d/
includedir /var/lib/sss/pubconf/krb5.include.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = YUNES.COM
dns_lookup_realm = false
dns_lookup_kdc = true
rdns = false
ticket_lifetime = 24h
forwardable = true
udp_preference_limit = 0
# default_ccache_name = KEYRING:persistent:%{uid}
default_ccache_name = FILE:/tmp/krb5cc_%{uid}
[realms]
YUNES.COM = {
kdc = cdh-ipa-v01.yunes.com:88
master_kdc = cdh-ipa-v01.yunes.com:88
admin_server = cdh-ipa-v01.yunes.com:749
default_domain = yunes.com
pkinit_anchors = FILE:/var/lib/ipa-client/pki/kdc-ca-bundle.pem
pkinit_pool = FILE:/var/lib/ipa-client/pki/ca-bundle.pem
}
2)分发其它节点
cd ~/scripts/
./sync_to_all_node.sh /etc/krb5.conf /etc/
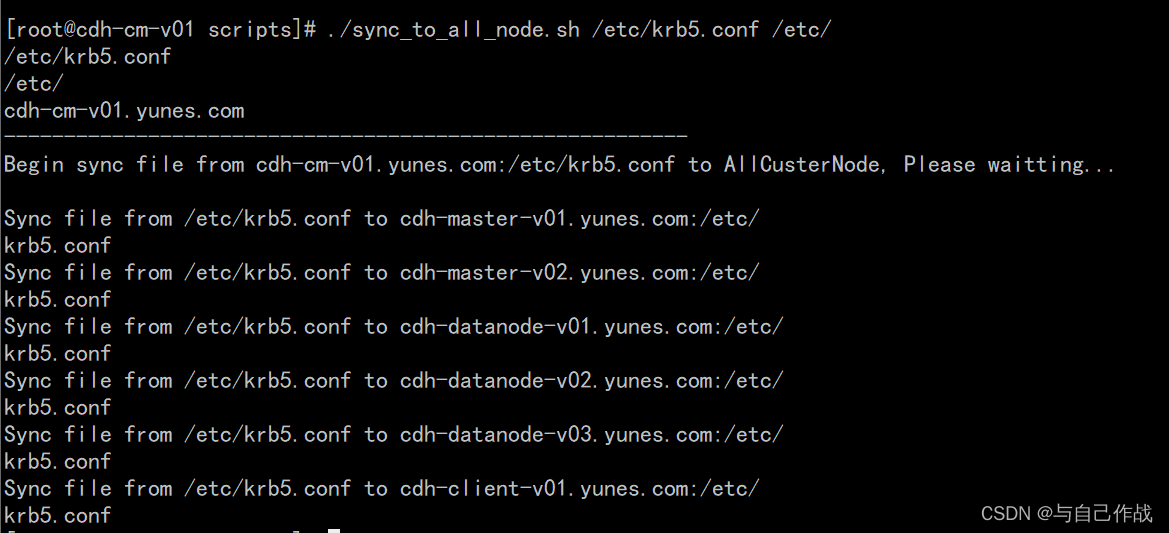
[root@cdh-cm-v01 ~]# cd ~/scripts/
[root@cdh-cm-v01 scripts]# ./sync_to_all_node.sh /etc/krb5.conf /etc/
3)验证(cdh-ipa-v01服务器)
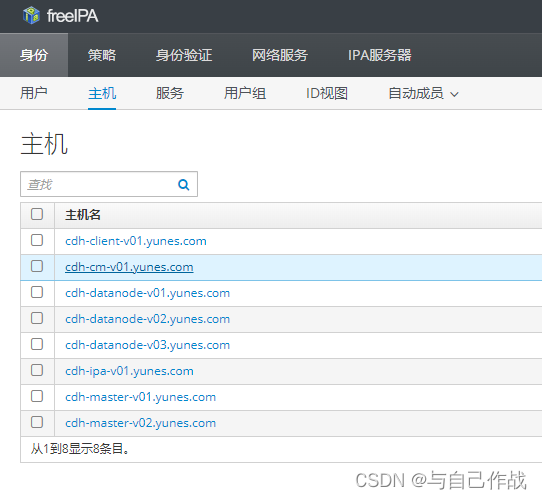
ipa host-find|grep -E “Host name|主机名”|grep “yunes.com”
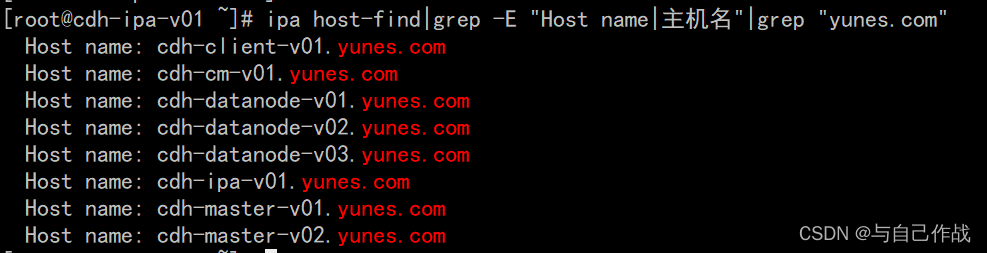
[root@cdh-ipa-v01 ~]# ipa host-find|grep -E "Host name|主机名"|grep "yunes.com"
Host name: cdh-client-v01.yunes.com
Host name: cdh-cm-v01.yunes.com
Host name: cdh-datanode-v01.yunes.com
Host name: cdh-datanode-v02.yunes.com
Host name: cdh-datanode-v03.yunes.com
Host name: cdh-ipa-v01.yunes.com
Host name: cdh-master-v01.yunes.com
Host name: cdh-master-v02.yunes.com
7、证书颁发存储
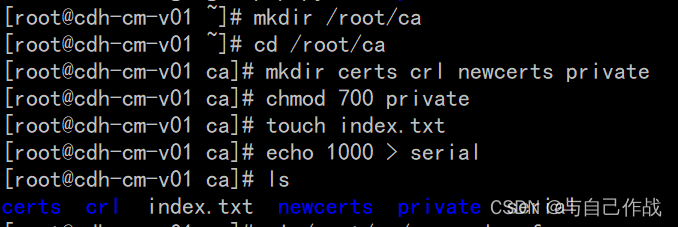
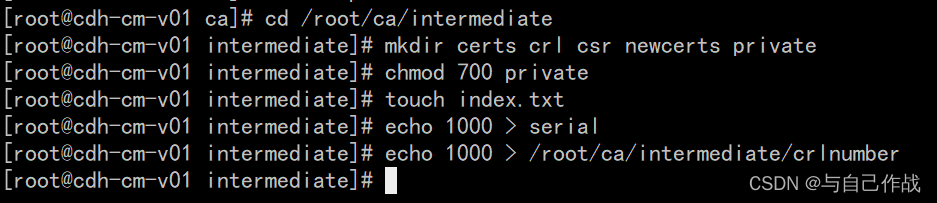
1)建根CA的目录结构
mkdir /root/ca
cd /root/ca
mkdir certs crl newcerts private
chmod 700 private
touch index.txt
echo 1000 > serial
[root@cdh-cm-v01 ~]# mkdir /root/ca
[root@cdh-cm-v01 ~]# cd /root/ca
[root@cdh-cm-v01 ca]# mkdir certs crl newcerts private
[root@cdh-cm-v01 ca]# chmod 700 private
[root@cdh-cm-v01 ca]# touch index.txt
[root@cdh-cm-v01 ca]# echo 1000 > serial
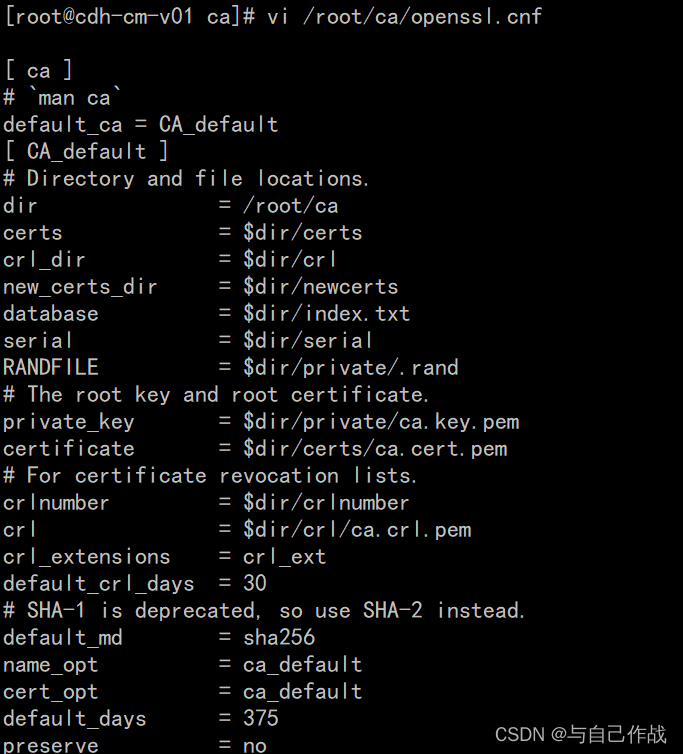
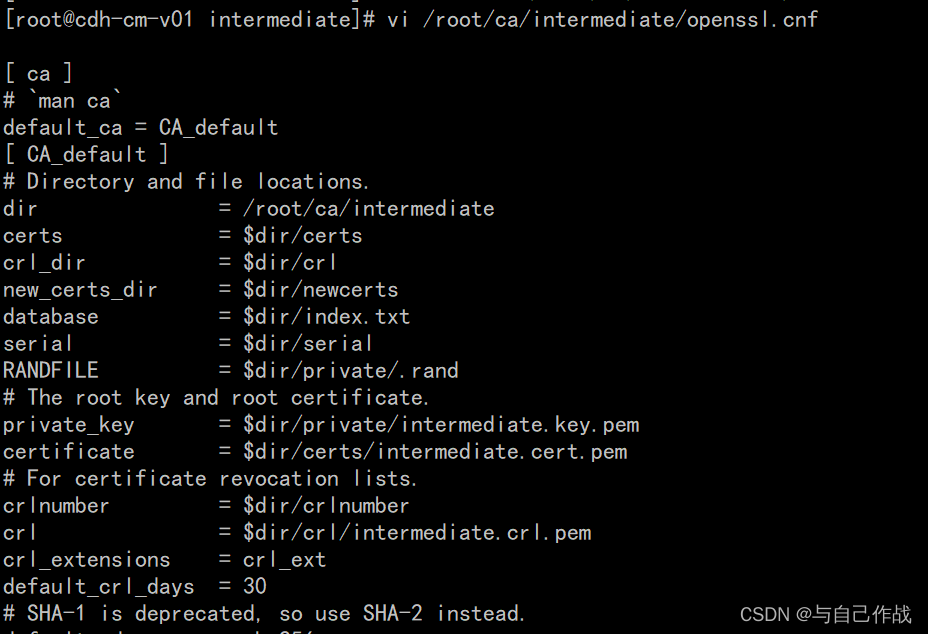
2)配置openssl.cnf文件
vi /root/ca/openssl.cnf
[root@cdh-cm-v01 ca]# vi /root/ca/openssl.cnf
[root@cdh-cm-v01 ca]# vi /root/ca/openssl.cnf
[ ca ]
# `man ca`
default_ca = CA_default
[ CA_default ]
# Directory and file locations.
dir = /root/ca
certs = $dir/certs
crl_dir = $dir/crl
new_certs_dir = $dir/newcerts
database = $dir/index.txt
serial = $dir/serial
RANDFILE = $dir/private/.rand
# The root key and root certificate.
private_key = $dir/private/ca.key.pem
certificate = $dir/certs/ca.cert.pem
# For certificate revocation lists.
crlnumber = $dir/crlnumber
crl = $dir/crl/ca.crl.pem
crl_extensions = crl_ext
default_crl_days = 30
# SHA-1 is deprecated, so use SHA-2 instead.
default_md = sha256
name_opt = ca_default
cert_opt = ca_default
default_days = 375
preserve = no
policy = policy_strict
[ policy_strict ]
# The root CA should only sign intermediate certificates that match.
# See the POLICY FORMAT section of `man ca`.
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ policy_loose ]
# Allow the intermediate CA to sign a more diverse range of certificates.
# See the POLICY FORMAT section of the `ca` man page.
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ req ]
# Options for the `req` tool (`man req`).
default_bits = 2048
distinguished_name = req_distinguished_name
string_mask = utf8only
# SHA-1 is deprecated, so use SHA-2 instead.
default_md = sha256
# Extension to add when the -x509 option is used.
x509_extensions = v3_ca
[ req_distinguished_name ]
# See <https://en.wikipedia.org/wiki/Certificate_signing_request>.
countryName = Country Name (2 letter code)
stateOrProvinceName = State or Province Name
localityName = Locality Name
0.organizationName = Organization Name
organizationalUnitName = Organizational Unit Name
commonName = Common Name
emailAddress = Email Address
# Optionally, specify some defaults.
countryName_default = GB
stateOrProvinceName_default = England
localityName_default =
0.organizationName_default = Alice Ltd
organizationalUnitName_default =
emailAddress_default =
[ v3_ca ]
# Extensions for a typical CA (`man x509v3_config`).
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer
basicConstraints = critical, CA:true
keyUsage = critical, digitalSignature, cRLSign, keyCertSign
[ v3_intermediate_ca ]
# Extensions for a typical intermediate CA (`man x509v3_config`).
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer
basicConstraints = critical, CA:true, pathlen:0
keyUsage = critical, digitalSignature, cRLSign, keyCertSign
[ usr_cert ]
# Extensions for client certificates (`man x509v3_config`).
basicConstraints = CA:FALSE
nsCertType = client, email
nsComment = "OpenSSL Generated Client Certificate"
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer
keyUsage = critical, nonRepudiation, digitalSignature, keyEncipherment
extendedKeyUsage = clientAuth, emailProtection
[ server_cert ]
# Extensions for server certificates (`man x509v3_config`).
basicConstraints = CA:FALSE
nsCertType = server,client
nsComment = "OpenSSL Generated Server Certificate"
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer:always
keyUsage = critical, digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth,clientAuth
[ crl_ext ]
# Extension for CRLs (`man x509v3_config`).
authorityKeyIdentifier=keyid:always
[ ocsp ]
# Extension for OCSP signing certificates (`man ocsp`).
basicConstraints = CA:FALSE
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer
keyUsage = critical, digitalSignature
extendedKeyUsage = critical, OCSPSigning
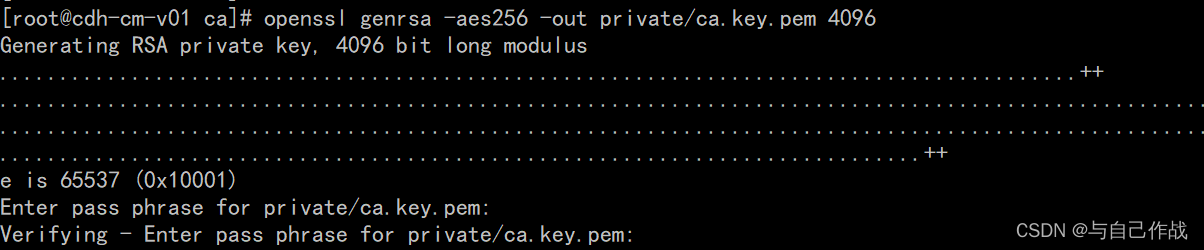
3)创建root钥匙
cd /root/ca
openssl genrsa -aes256 -out private/ca.key.pem 4096
chmod 400 private/ca.key.pem
[root@cdh-cm-v01 ca]# cd /root/ca
[root@cdh-cm-v01 ca]# openssl genrsa -aes256 -out private/ca.key.pem 4096
Generating RSA private key, 4096 bit long modulus
..........................................................................................++
.........................................................................................................................................................................................................................................................................................................................................................................................................++
e is 65537 (0x10001)
Enter pass phrase for private/ca.key.pem: tianlingqun
Verifying - Enter pass phrase for private/ca.key.pem: tianlingqun
[root@cdh-cm-v01 ca]# chmod 400 private/ca.key.pem
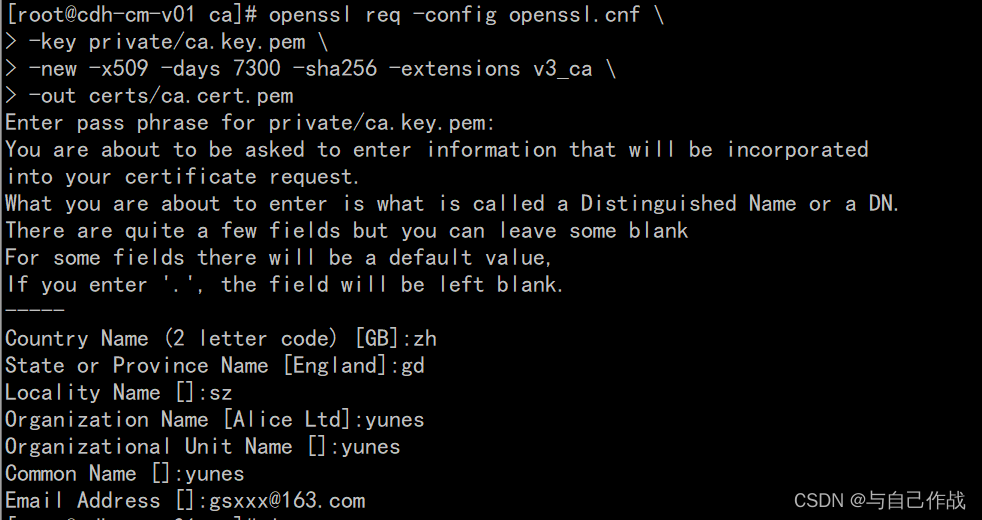
4)创建root证书
cd /root/ca
openssl req -config openssl.cnf
-key private/ca.key.pem
-new -x509 -days 7300 -sha256 -extensions v3_ca
-out certs/ca.cert.pem
chmod 400 certs/ca.cert.pem
[root@cdh-cm-v01 ca]# cd /root/ca
[root@cdh-cm-v01 ca]# openssl req -config openssl.cnf \
> -key private/ca.key.pem \
> -new -x509 -days 7300 -sha256 -extensions v3_ca \
> -out certs/ca.cert.pem
Enter pass phrase for private/ca.key.pem:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [GB]:zh
State or Province Name [England]:gd
Locality Name []:sz
Organization Name [Alice Ltd]:yunes
Organizational Unit Name []:yunes
Common Name []:yunes
Email Address []:gsxxx@163.com
[root@cdh-cm-v01 ca]# chmod 400 certs/ca.cert.pem
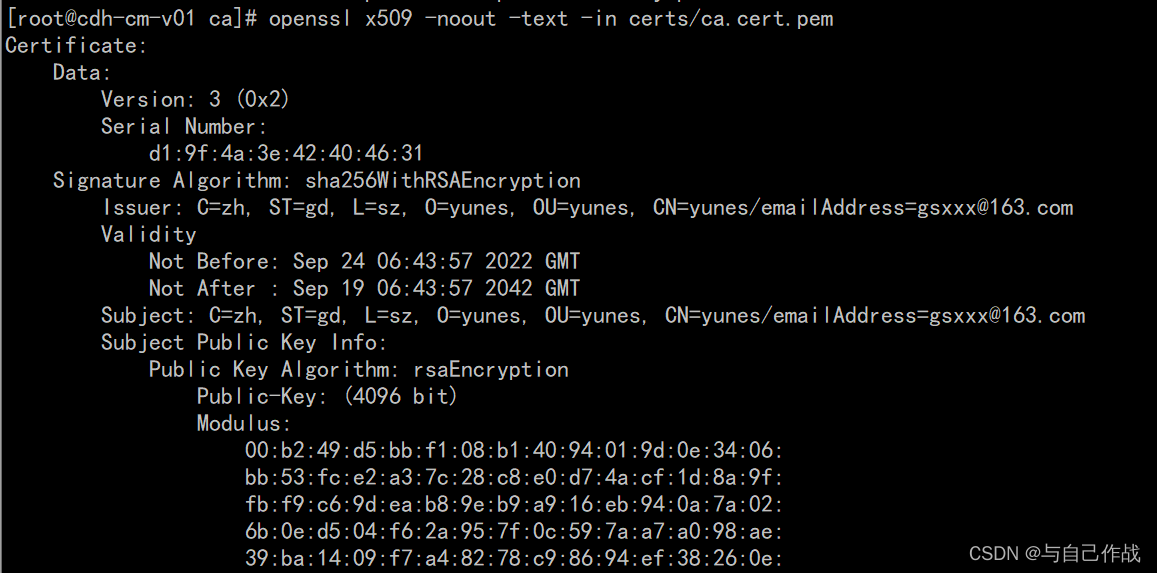
5)验证root 钥匙
openssl x509 -noout -text -in certs/ca.cert.pem
[root@cdh-cm-v01 ca]# openssl x509 -noout -text -in certs/ca.cert.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
d1:9f:4a:3e:42:40:46:31
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=zh, ST=gd, L=sz, O=yunes, OU=yunes, CN=yunes/emailAddress=gsxxx@163.com
Validity
Not Before: Sep 24 06:43:57 2022 GMT
Not After : Sep 19 06:43:57 2042 GMT
Subject: C=zh, ST=gd, L=sz, O=yunes, OU=yunes, CN=yunes/emailAddress=gsxxx@163.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
00:b2:49:d5:bb:f1:08:b1:40:94:01:9d:0e:34:06:
bb:53:fc:e2:a3:7c:28:c8:e0:d7:4a:cf:1d:8a:9f:
fb:f9:c6:9d:ea:b8:9e:b9:a9:16:eb:94:0a:7a:02:
6b:0e:d5:04:f6:2a:95:7f:0c:59:7a:a7:a0:98:ae:
39:ba:14:09:f7:a4:82:78:c9:86:94:ef:38:26:0e:
2f:b7:ea:fc:2a:f9:46:0e:15:46:26:5e:33:33:23:
b1:28:f1:f1:03:b7:52:a7:9c:fa:f2:7e:97:07:08:
2f:41:1a:d8:5c:0f:8b:ca:6c:84:1c:40:88:b0:57:
b3:1a:52:35:e3:62:91:c1:64:04:4a:77:ae:58:bb:
e5:28:9b:8e:9f:1d:31:c7:a1:26:60:c1:0d:ef:c3:
ee:5a:a7:dd:bd:96:c8:03:01:0c:be:c5:ef:7a:7a:
6b:3a:ca:5d:28:93:0c:fd:3c:ed:e6:7e:3a:69:5d:
96:15:fc:68:36:1d:55:ce:b0:cb:3a:4d:a2:04:57:
c8:4e:da:73:b7:80:f0:7d:40:53:42:ac:62:fa:5e:
4a:1e:d6:cd:2f:df:b5:36:5d:b1:b3:c6:a4:d6:c1:
e4:f2:00:86:09:4f:93:21:d8:de:0c:16:a6:c8:82:
35:dc:bc:d9:7a:ed:5e:40:bf:d1:a2:c5:25:aa:0b:
b7:f4:86:e7:70:70:95:00:aa:43:16:29:36:b4:1b:
3f:36:47:f9:d6:52:42:80:98:aa:7a:d3:25:82:55:
b3:e1:35:4b:d6:e4:fe:da:6e:c7:af:fe:f4:d5:0d:
9d:ca:a7:a3:93:59:00:2c:dd:90:a9:e6:a0:82:27:
35:76:a3:ca:d6:b2:7a:d7:a4:11:ba:a8:83:b0:78:
0c:4a:ec:24:c1:a7:8d:36:56:c6:17:33:8a:ef:51:
b0:6e:16:0a:0b:68:8f:75:aa:a7:a1:6c:e6:a1:17:
03:0a:65:64:8c:fa:39:cc:54:e8:9e:19:73:d0:a7:
3c:e3:a0:24:d4:43:45:a0:59:8b:f6:9f:d9:78:03:
2f:1c:82:9d:a4:cd:cb:59:6f:09:54:ac:93:91:42:
a8:94:34:37:29:87:0a:12:3c:b6:21:56:66:c5:f6:
e0:41:f9:a0:a4:20:55:5b:43:fd:b9:41:3b:8c:8b:
08:2f:ad:96:49:a4:eb:f6:e0:27:73:ce:6a:9d:85:
1b:ce:d4:81:81:04:3a:ca:99:37:f1:dd:68:85:82:
7c:7d:5e:e3:ea:1d:59:98:6f:c0:b7:de:18:aa:35:
2e:14:2f:4e:57:0c:59:35:93:ce:87:15:14:b6:d7:
27:d9:6b:fe:73:29:74:2d:59:66:b5:65:94:35:00:
11:b5:13
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
52:2D:7C:48:AE:04:3B:71:50:53:38:61:5B:11:04:39:63:CD:83:8A
X509v3 Authority Key Identifier:
keyid:52:2D:7C:48:AE:04:3B:71:50:53:38:61:5B:11:04:39:63:CD:83:8A
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Key Usage: critical
Digital Signature, Certificate Sign, CRL Sign
Signature Algorithm: sha256WithRSAEncryption
80:b1:c2:b4:6c:d8:0c:43:b6:5d:70:a9:c9:26:e9:22:05:08:
95:92:bc:9f:cb:f7:3c:d5:fb:98:b2:19:8a:6e:be:92:7b:f2:
b9:30:e3:9e:c6:de:27:ec:eb:c3:e8:3f:d8:00:63:49:87:df:
b1:d8:03:96:6d:c2:d5:95:18:06:ed:98:55:b2:33:ee:2e:2c:
05:3d:66:6e:67:6c:0e:24:e3:4a:a2:34:81:48:8f:74:51:24:
80:c9:56:20:38:fe:62:7d:e5:3d:62:47:5f:36:a6:0f:ed:e9:
b3:e3:65:15:16:8a:5b:2f:ae:19:1e:3f:96:53:fc:ac:4f:e3:
2d:61:1e:33:46:de:7d:51:05:f5:25:7b:58:63:ef:00:cc:b3:
51:62:c3:af:ae:7a:ea:3b:bb:5f:a4:e4:3e:4b:f5:3f:0f:a2:
f5:c0:23:27:d3:85:4c:25:a7:92:d5:f9:b0:09:06:22:51:1f:
71:8c:82:f9:a1:54:62:c8:51:53:18:f1:5d:dc:5d:d6:67:bd:
97:09:76:c1:ea:06:bb:04:25:da:a3:b0:6e:4d:88:77:89:8b:
23:12:0d:38:9c:33:ad:87:11:04:5b:05:b1:af:df:b3:d6:5f:
9a:b5:97:8b:be:3c:5a:1c:5e:4c:69:57:9f:56:16:1f:d7:78:
3e:59:64:93:ce:7a:22:55:c0:54:4b:dc:bf:35:c0:bb:9c:7e:
d3:2b:42:c1:75:52:2a:1c:9f:51:ad:c1:5d:45:c4:e4:9b:19:
88:7a:3e:12:16:e6:33:0b:ba:ba:12:6c:60:e3:8f:01:5f:e6:
2d:fd:2d:92:a4:58:4c:17:8c:db:05:28:c1:12:4e:43:3a:3f:
96:85:b5:5d:f0:00:ac:af:3a:cc:b1:da:d3:d1:18:77:f9:d9:
b8:35:66:43:42:8d:71:d7:1e:81:06:6b:89:4b:b8:0e:3a:43:
35:f5:ed:65:e6:1a:75:1a:39:47:61:d6:48:04:5c:54:9d:05:
8e:75:ce:ce:18:13:c3:2b:80:12:30:3f:ed:58:8e:4e:5e:e2:
08:3b:e6:93:60:46:0d:34:b0:f3:21:18:b8:ec:2c:32:f7:0a:
fc:13:c7:69:01:ef:46:33:2d:41:31:7e:62:47:bc:5a:61:c5:
3e:aa:69:c5:58:b4:19:d6:76:66:76:8f:af:97:0d:37:0f:e5:
d6:fe:9a:b5:7a:cd:bf:b5:42:fe:33:c1:26:4f:6a:3c:a5:f6:
8b:0a:c0:1a:83:9b:76:4c:1e:4a:35:56:fb:57:48:96:10:5a:
ab:ef:21:50:f4:f5:b6:ca:75:25:bb:6b:7a:58:33:e4:51:ee:
9f:8a:27:3d:4e:32:d5:15
8、Intermediate CA目录
1)创建一个intermediate目录存放CA
mkdir -p /root/ca/intermediate/
[root@cdh-cm-v01 ca]# mkdir -p /root/ca/intermediate/
2)创建Intermediate CA目录
cd /root/ca/intermediate
mkdir certs crl csr newcerts private
chmod 700 private
touch index.txt
echo 1000 > serial
echo 1000 > /root/ca/intermediate/crlnumber
[root@cdh-cm-v01 ca]# cd /root/ca/intermediate
[root@cdh-cm-v01 intermediate]# mkdir certs crl csr newcerts private
[root@cdh-cm-v01 intermediate]# chmod 700 private
[root@cdh-cm-v01 intermediate]# touch index.txt
[root@cdh-cm-v01 intermediate]# echo 1000 > serial
[root@cdh-cm-v01 intermediate]# echo 1000 > /root/ca/intermediate/crlnumber
3)配置openssl.cnf文件
vi /root/ca/intermediate/openssl.cnf
[root@cdh-cm-v01 intermediate]# vi /root/ca/intermediate/openssl.cnf
[ ca ]
# `man ca`
default_ca = CA_default
[ CA_default ]
# Directory and file locations.
dir = /root/ca/intermediate
certs = $dir/certs
crl_dir = $dir/crl
new_certs_dir = $dir/newcerts
database = $dir/index.txt
serial = $dir/serial
RANDFILE = $dir/private/.rand
# The root key and root certificate.
private_key = $dir/private/intermediate.key.pem
certificate = $dir/certs/intermediate.cert.pem
# For certificate revocation lists.
crlnumber = $dir/crlnumber
crl = $dir/crl/intermediate.crl.pem
crl_extensions = crl_ext
default_crl_days = 30
# SHA-1 is deprecated, so use SHA-2 instead.
default_md = sha256
name_opt = ca_default
cert_opt = ca_default
default_days = 375
preserve = no
policy = policy_loose
[ policy_strict ]
# The root CA should only sign intermediate certificates that match.
# See the POLICY FORMAT section of `man ca`.
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ policy_loose ]
# Allow the intermediate CA to sign a more diverse range of certificates.
# See the POLICY FORMAT section of the `ca` man page.
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ req ]
# Options for the `req` tool (`man req`).
default_bits = 2048
distinguished_name = req_distinguished_name
string_mask = utf8only
# SHA-1 is deprecated, so use SHA-2 instead.
default_md = sha256
# Extension to add when the -x509 option is used.
x509_extensions = v3_ca
[ req_distinguished_name ]
# See <https://en.wikipedia.org/wiki/Certificate_signing_request>.
countryName = Country Name (2 letter code)
stateOrProvinceName = State or Province Name
localityName = Locality Name
0.organizationName = Organization Name
organizationalUnitName = Organizational Unit Name
commonName = Common Name
emailAddress = Email Address
# Optionally, specify some defaults.
countryName_default = GB
stateOrProvinceName_default = England
localityName_default =
0.organizationName_default = Alice Ltd
organizationalUnitName_default =
emailAddress_default =
[ v3_ca ]
# Extensions for a typical CA (`man x509v3_config`).
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer
basicConstraints = critical, CA:true
keyUsage = critical, digitalSignature, cRLSign, keyCertSign
[ v3_intermediate_ca ]
# Extensions for a typical intermediate CA (`man x509v3_config`).
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer
basicConstraints = critical, CA:true, pathlen:0
keyUsage = critical, digitalSignature, cRLSign, keyCertSign
[ usr_cert ]
# Extensions for client certificates (`man x509v3_config`).
basicConstraints = CA:FALSE
nsCertType = client, email
nsComment = "OpenSSL Generated Client Certificate"
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer
keyUsage = critical, nonRepudiation, digitalSignature, keyEncipherment
extendedKeyUsage = clientAuth, emailProtection
[ server_cert ]
# Extensions for server certificates (`man x509v3_config`).
basicConstraints = CA:FALSE
nsCertType = server,client
nsComment = "OpenSSL Generated Server Certificate"
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer:always
keyUsage = critical, digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth, clientAuth
[ crl_ext ]
# Extension for CRLs (`man x509v3_config`).
authorityKeyIdentifier=keyid:always
[ ocsp ]
# Extension for OCSP signing certificates (`man ocsp`).
basicConstraints = CA:FALSE
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer
keyUsage = critical, digitalSignature
extendedKeyUsage = critical, OCSPSigning
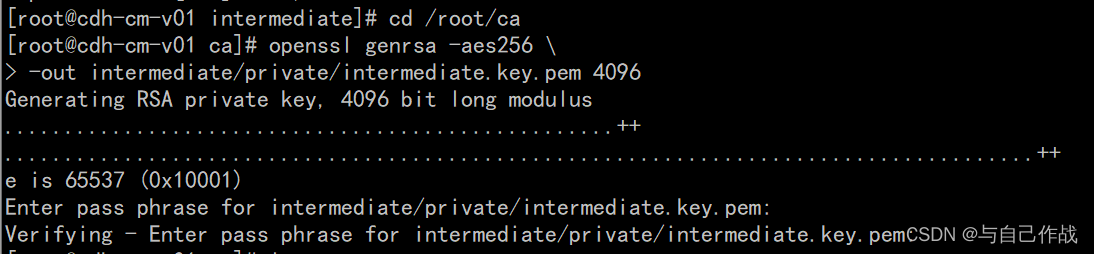
3)创建 intermediate钥匙
cd /root/ca
openssl genrsa -aes256
-out intermediate/private/intermediate.key.pem 4096
[root@cdh-cm-v01 ca]# openssl genrsa -aes256 \
> -out intermediate/private/intermediate.key.pem 4096
Generating RSA private key, 4096 bit long modulus
.....chmod 400 intermediate/private/intermediate.key.pem................++
.........................................................................................................................++
e is 65537 (0x10001)
Enter pass phrase for intermediate/private/intermediate.key.pem: tianlingqun
Verifying - Enter pass phrase for intermediate/private/intermediate.key.pem: tianlingqun
Verify failure
User interface error
140692343179152:error:0906906F:PEM routines:PEM_ASN1_write_bio:read key:pem_lib.c:385:
4)创建intermediate证书签名
cd /root/ca
openssl req -config intermediate/openssl.cnf -new -sha256
-key intermediate/private/intermediate.key.pem
-out intermediate/csr/intermediate.csr.pem
chmod 400 intermediate/private/intermediate.key.pem
[root@cdh-cm-v01 ca]# cd /root/ca
[root@cdh-cm-v01 ca]# openssl req -config intermediate/openssl.cnf -new -sha256 \
> -key intermediate/private/intermediate.key.pem \
> -out intermediate/csr/intermediate.csr.pem
Enter pass phrase for intermediate/private/intermediate.key.pem:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [GB]:zh
State or Province Name [England]:gd
Locality Name []:sz
Organization Name [Alice Ltd]:yunes
Organizational Unit Name []:yunes
Common Name []:yunes
Email Address []:gsxxx@163.com
[root@cdh-cm-v01 ca]# chmod 400 intermediate/private/intermediate.key.pem

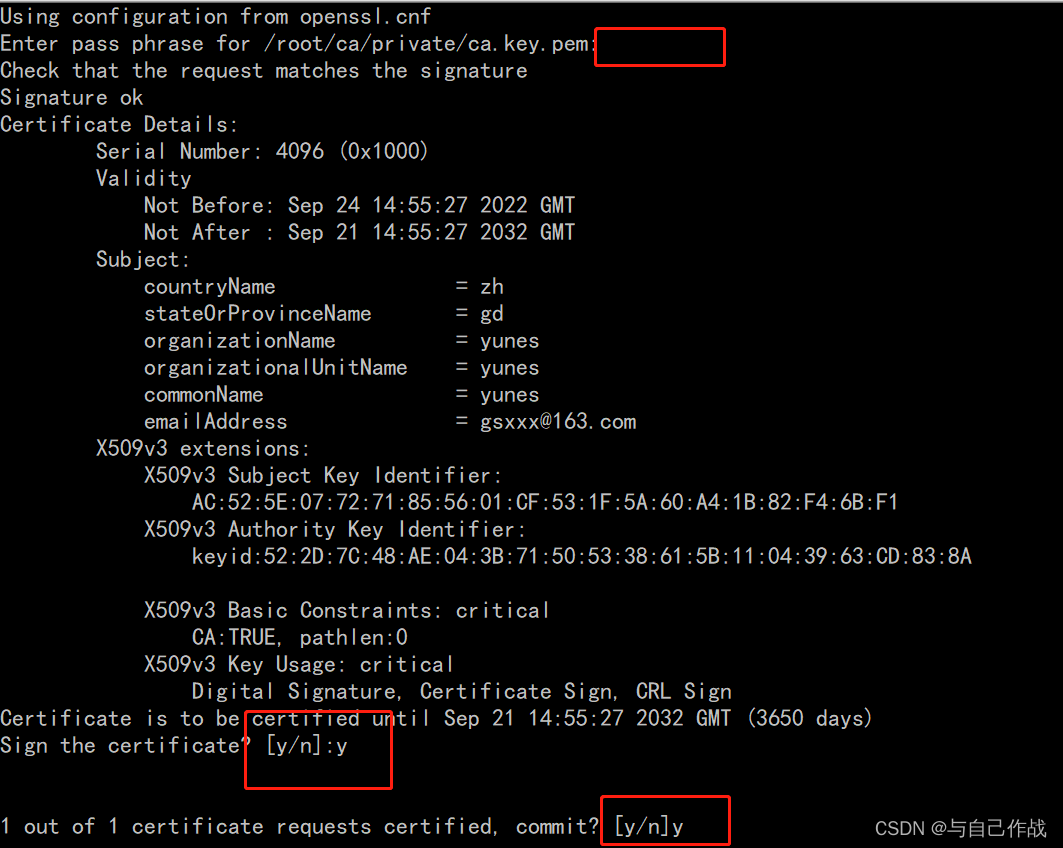
5)创建intermediate证书
cd /root/ca
openssl ca -config openssl.cnf -extensions v3_intermediate_ca
-days 3650 -notext -md sha256
-in intermediate/csr/intermediate.csr.pem
-out intermediate/certs/intermediate.cert.pem
[root@cdh-cm-v01 ca]# cd /root/ca
[root@cdh-cm-v01 ca]# openssl ca -config openssl.cnf -extensions v3_intermediate_ca \
> -days 3650 -notext -md sha256 \
> -in intermediate/csr/intermediate.csr.pem \
> -out intermediate/certs/intermediate.cert.pem
Using configuration from openssl.cnf
Enter pass phrase for /root/ca/private/ca.key.pem: tianlingqun
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4096 (0x1000)
Validity
Not Before: Sep 24 14:55:27 2022 GMT
Not After : Sep 21 14:55:27 2032 GMT
Subject:
countryName = zh
stateOrProvinceName = gd
organizationName = yunes
organizationalUnitName = yunes
commonName = yunes
emailAddress = gsxxx@163.com
X509v3 extensions:
X509v3 Subject Key Identifier:
AC:52:5E:07:72:71:85:56:01:CF:53:1F:5A:60:A4:1B:82:F4:6B:F1
X509v3 Authority Key Identifier:
keyid:52:2D:7C:48:AE:04:3B:71:50:53:38:61:5B:11:04:39:63:CD:83:8A
X509v3 Basic Constraints: critical
CA:TRUE, pathlen:0
X509v3 Key Usage: critical
Digital Signature, Certificate Sign, CRL Sign
Certificate is to be certified until Sep 21 14:55:27 2032 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
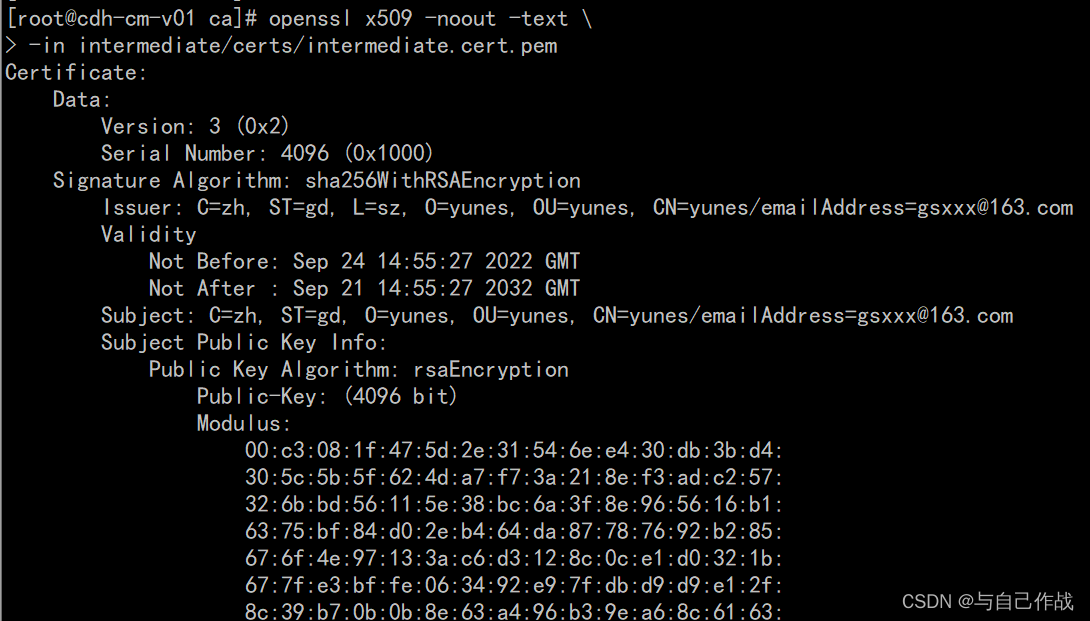
6)验证intermediate证书
openssl x509 -noout -text
-in intermediate/certs/intermediate.cert.pem
[root@cdh-cm-v01 ca]# openssl x509 -noout -text \
> -in intermediate/certs/intermediate.cert.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 4096 (0x1000)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=zh, ST=gd, L=sz, O=yunes, OU=yunes, CN=yunes/emailAddress=gsxxx@163.com
Validity
Not Before: Sep 24 14:55:27 2022 GMT
Not After : Sep 21 14:55:27 2032 GMT
Subject: C=zh, ST=gd, O=yunes, OU=yunes, CN=yunes/emailAddress=gsxxx@163.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
00:c3:08:1f:47:5d:2e:31:54:6e:e4:30:db:3b:d4:
30:5c:5b:5f:62:4d:a7:f7:3a:21:8e:f3:ad:c2:57:
32:6b:bd:56:11:5e:38:bc:6a:3f:8e:96:56:16:b1:
63:75:bf:84:d0:2e:b4:64:da:87:78:76:92:b2:85:
67:6f:4e:97:13:3a:c6:d3:12:8c:0c:e1:d0:32:1b:
67:7f:e3:bf:fe:06:34:92:e9:7f:db:d9:d9:e1:2f:
8c:39:b7:0b:0b:8e:63:a4:96:b3:9e:a6:8c:61:63:
71:ed:be:bd:bb:ee:bf:e4:4b:18:ab:22:61:64:42:
2d:35:b5:b8:25:64:51:5e:8e:66:fd:4e:a1:04:92:
4f:d0:ae:db:14:17:fe:96:4c:08:61:77:68:66:ae:
9b:30:c1:c6:4b:c7:0f:c7:0a:e3:99:3e:a2:76:a2:
b7:c4:4e:fd:67:c3:96:21:69:ae:84:da:4d:10:4b:
bc:82:fb:cc:ba:a5:9f:83:00:36:0e:2c:4a:8a:3d:
58:d4:b6:e4:a4:a4:01:d7:8b:ff:bc:10:39:27:9f:
55:ed:2b:69:5b:a9:2e:55:f1:7d:4d:9c:de:af:76:
6c:c3:87:f5:55:c2:ff:2c:a5:9b:fa:e8:75:cd:5a:
b9:5b:00:7d:fe:b9:6a:ef:16:22:15:10:f1:8e:4f:
be:83:9f:d9:1f:99:2f:27:34:de:a6:97:3c:b1:5a:
08:6d:91:85:70:53:ae:9b:31:56:17:e5:50:3c:e2:
3f:e6:22:6a:7e:6c:34:e2:3f:cf:40:50:d6:27:56:
32:f8:c9:33:cd:c5:8c:06:db:14:0e:04:13:d7:03:
9d:0f:95:c2:d2:a5:80:4d:dc:67:fc:a5:ba:f5:09:
b2:f2:e9:f1:40:27:74:f7:05:ca:51:82:03:3b:90:
41:86:d9:3f:c3:51:d7:ef:14:bd:f1:90:d9:42:d5:
0b:76:6e:67:b8:a2:32:fa:95:e3:9d:4a:45:60:c6:
86:f6:1a:a4:7f:36:91:13:b4:15:bf:d3:a0:4b:3b:
ca:8a:08:e4:29:0d:b6:1d:eb:08:71:d2:0a:9a:42:
0f:af:24:f2:da:fb:52:ad:fe:3c:55:db:0e:22:c7:
3f:53:cb:3d:89:48:43:40:06:2d:26:8a:53:0f:b4:
70:fa:dd:4d:78:f3:25:36:47:41:ed:97:9d:2b:29:
78:ca:02:f3:5c:2c:f8:b4:92:e4:dd:8f:c0:46:0f:
1e:d4:b4:48:eb:8f:67:1b:99:7f:5b:3f:8f:34:e3:
51:96:f4:bd:b4:6a:41:b7:7c:1c:3d:f9:6d:05:15:
fb:c6:f3:21:de:fd:74:c4:a4:50:a7:9e:2c:94:cc:
2f:50:db
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
AC:52:5E:07:72:71:85:56:01:CF:53:1F:5A:60:A4:1B:82:F4:6B:F1
X509v3 Authority Key Identifier:
keyid:52:2D:7C:48:AE:04:3B:71:50:53:38:61:5B:11:04:39:63:CD:83:8A
X509v3 Basic Constraints: critical
CA:TRUE, pathlen:0
X509v3 Key Usage: critical
Digital Signature, Certificate Sign, CRL Sign
Signature Algorithm: sha256WithRSAEncryption
72:53:fb:4e:44:38:37:15:10:d2:25:1c:a9:7b:53:4c:7d:20:
72:28:f2:86:7c:5c:36:90:62:12:60:ec:b8:44:dc:27:57:08:
cd:a5:68:6d:0f:0e:e6:6d:33:11:ee:8b:0a:b0:d1:b2:ed:56:
10:49:eb:88:62:1d:ee:38:e0:e5:35:c2:37:d5:7e:ca:73:b8:
8b:59:7f:af:c6:1c:96:5e:b8:bb:b8:93:70:3f:2c:65:3d:55:
0d:6f:e0:e4:1f:70:8b:91:31:07:43:aa:45:0c:39:20:f0:32:
f1:d8:93:67:2b:82:e0:51:8a:1c:9c:49:e9:db:d6:b6:4a:ee:
8d:a4:8c:48:52:15:f9:85:a7:1c:63:55:f3:23:64:a2:27:7e:
67:af:2b:a4:a8:ba:a5:70:8d:b1:6a:19:17:75:71:f0:fe:37:
59:ab:53:9a:93:1d:cd:94:65:c7:84:0b:bd:d6:96:88:16:e2:
b5:71:c8:46:7d:4e:69:7d:c9:a4:99:d3:61:98:24:2f:cc:c0:
30:da:98:9e:49:c7:e1:88:9a:1c:cb:58:04:21:8d:8e:a0:dc:
ea:fd:e2:7e:ab:58:cd:d8:52:37:c6:12:5c:ad:e6:d4:28:39:
60:91:7b:66:9c:22:f2:1c:1b:56:a1:56:d5:84:a6:c5:53:58:
ea:37:51:f1:ee:2c:3f:f7:4f:55:ba:63:4f:6a:ec:6b:45:36:
a2:30:95:4a:d9:82:91:b9:02:e2:a0:20:fc:73:28:d8:c0:98:
b9:45:a3:c0:11:cf:b7:9c:ff:ec:27:d5:b3:7d:2c:ce:ae:78:
b9:f9:3e:69:34:66:4a:df:e1:1f:da:73:17:66:3e:96:3a:2f:
05:10:aa:45:77:bb:72:8c:17:23:2b:d9:67:36:33:22:3b:10:
be:a5:fd:55:4d:a9:7a:bc:f1:fa:50:e5:9b:d1:1e:fa:f6:bb:
c9:9d:3f:63:60:36:d8:9f:d0:3c:d4:a0:ba:02:ed:08:a0:f1:
e2:d9:d3:77:99:3d:eb:7c:48:f7:60:9a:22:e6:b6:fb:7e:30:
8d:b5:5b:f3:ff:4a:83:db:69:fc:c4:e0:33:04:ff:be:af:2c:
c9:c4:a7:84:86:be:f7:f1:64:13:4c:e5:2b:75:ea:90:e2:08:
28:a6:7a:f4:22:ef:54:3b:d6:89:7d:5e:1a:6b:d8:6c:b0:9b:
91:f0:27:de:78:d7:fd:f9:28:b4:7d:27:33:71:48:4b:1a:09:
c5:f3:19:20:bd:35:03:35:d7:ac:a3:e7:3e:4f:93:df:e8:af:
cb:03:e2:a7:1e:58:f3:f4:c7:a7:d0:f7:17:6a:3f:dd:de:65:
d7:28:a0:89:f5:2a:e2:8d
7)验证intermediate证书,验证通过返回OK
openssl verify -CAfile certs/ca.cert.pem
intermediate/certs/intermediate.cert.pem
[root@cdh-cm-v01 ca]# openssl verify -CAfile certs/ca.cert.pem \
> intermediate/certs/intermediate.cert.pem
intermediate/certs/intermediate.cert.pem: OK

