【北邮国院大三下】Cybersecurity Law 网络安全法 Week1【更新Topic4, 5】_cyber security la
他们通常不会给出具体的指导,说明这意味着什么或如何实现
Issues
The duty to keep information secure is not further specified in the statutes
保护信息安全的义务在法规中没有进一步规定
The GDPR indicates: ‘Having regard to the state of the art and the cost of their implementation, such measures shall ensure a level of security appropriate to the risks represented by the processing and the nature of the data to be protected.’
GDPR指出:“考虑到技术水平和实施成本,此类措施应确保与处理所代表的风险和被保护数据的性质相适应的安全水平。”
A cost/risk analysis qualifies an appropriate level of security
成本/风险分析确定了适当的安全级别
【上面这些东西确实没有一条主逻辑链,所以ppt很乱,我整理的也很乱,将就看吧,也没啥内容】
什么是cybersecurity中的cyber
It might potentially include any device that has the ability to communicate
它可能包括任何具有通信能力的设备
- Cybersecurity refers to the systems, contracts and policies we put in place to manage risk with regards to Cyberspace 网络安全是指我们为管理网络空间风险而制定的系统、合同和政策
网络安全的main risk areas
- Threats to corporate files 公司文件威胁
- Loss of files 文件丢失
- Email attacks and theft 电子邮件攻击和盗窃
- Threats to industrial control systems 对工业控制系统的威胁
- Threats to confidential information 对机密信息的威胁
- Other commercial risks
网络安全的main vulnerabilities
- Password and policy issues 密码和策略问题
- BYOD and shadow IT BYOD和影子IT
- Loss or theft of devices 设备丢失或被盗
- Technical flaws 技术的缺陷
- Out-of-date applications 过时的应用程序
- Insider threats 内部威胁
- Data storage issues 数据存储问题
- SQL injections, cryptographic flaws SQL注入,密码漏洞
- Cloud-based storage and systems 基于云的存储和系统
接下来要谈的是EU的information security相关问题
Conclusions of EU
【为什么把conclusion放前面,因为PPT的东西太乱了,conclusion给的应该都是重点,带着这些重点再往后看】
- No single source of Information Security obligations – no single definition 没有单一来源的信息安全义务-没有单一的定义
- Different types of information – different level of protection –different mechanisms 不同类型的信息——不同级别的保护——不同的机制
- EU approach is a principle-based regulation 欧盟的做法是基于原则的监管
Directives / Regulations 指示/规例
- Privacy
- EU General Data Protection Regulation (GDPR) 欧盟的通用数据保护条例
- Telecommunications networks/services
- ePrivacy Directive (regulates the use of electronic communications services) 电子资料私隐指引(规管电子通讯服务的使用)
- Critical Infrastructure 关键基础设施
- Network and Information Systems Directive (NIS Directive) 网络和信息系统指令(NIS指令)
GDPR
Introduction
Organisations that decide to collect and process personal data for their own purposes are known as controllers
决定为自己的目的收集和处理个人数据的组织被称为控制者
A controller may engage a service provider or processor to process personal data on behalf of the controller
控制者可以聘请服务提供者或处理者代表控制者处理个人数据
A processor is an individual or legal person or other body that processes personal data on behalf of the controller
处理者是指代表控制者处理个人数据的个人、法人或其他团体
Scope
The GDPR regulates the processing of personal data
GDPR规范了个人数据的处理
Personal data is any information relating to an identified or identifiable natural person (‘data subject’)
个人数据是指与已识别或可识别自然人(“数据主体”)有关的任何信息。
Identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person
可识别自然人是指可以直接或间接识别的自然人,特别是通过参考一个标识符,如姓名、识别号码、位置数据、在线标识符,或参考该自然人的身体、生理、遗传、心理、经济、文化或社会身份的一个或多个特定因素
Relates to living individuals only
只涉及活着的个人
Special categories of personal data is subject to a stricter regime
特殊类别的个人资料受到更严格的制度管制
- Racial or ethnic origin 种族或民族起源
- Political opinions 政治意见
- Religious or philosophical beliefs 宗教或哲学信仰
- Trade union membership 工会会员资格
- Genetic data 遗传学数据
- Biometric data for the purpose of uniquely identifying a natural person 用于唯一识别自然人的生物特征数据
- Data concerning health 关于健康的数据
- Data concerning a natural person’s sex life or sexual orientation 有关自然人性生活或性取向的资料
Principles
- Principles-based regulation 基于原则的监管
- The EU has adopted similar risk-based safeguarding and information obligations in respect of telecommunication networks and payment services, as well as under the NIS Directive and the e-Privacy Directive 欧盟在电信网络和支付服务方面,以及在NIS指令和电子隐私指令下,也采取了类似的基于风险的保障和信息义务
- Lawfulness, fairness and transparency 依法、公平、透明
- Purpose limitation 目的限制
- Data minimisation 数据最小化
- Accuracy 准确性
- Storage limitation 储存限量
- Integrity and Confidentiality 数据完整性和隐私保护
- ensures appropriate security of personal data, including protection against unauthorised or unlawful processing and against accidental loss, destruction or damage, using appropriate technical or organisational measures 使用适当的技术或组织措施,确保个人资料的适当安全,包括防止未经授权或非法处理,以及防止意外遗失、破坏或损坏
- Accountability 责任
Information Security Obligation 信息安全义务
- Safeguarding obligations, which require organisations to put in place ‘appropriate and proportionate’ security measures, and 保护义务,要求组织实施“适当和相称的”安全措施
- Information obligations, which require the sharing or disclosure of information 信息义务,即要求分享或披露信息
- Article 32 requires that the controller:
- Taking into account the state of the art, the costs of implementation and the nature, scope, context and purposes of processing as well as the risk of varying likelihood and severity for the rights and freedoms of natural persons, the controller and the processor shall implement appropriate technical and organisational measures to ensure a level of security appropriate to the risk 考虑到技术水平、实施成本、处理的性质、范围、背景和目的,以及对自然人的权利和自由具有不同可能性和严重程度的风险,控制者和处理者应实施适当的技术和组织措施,以确保与风险相适应的安全水平
- This includes, inter alia: 其中包括:
- the pseudonymisation and encryption of personal data; 个人资料的假名化和加密;
- the ability to ensure the ongoing confidentiality, integrity, availability and resilience of processing systems and services; 确保处理系统和服务的持续保密性、完整性、可用性和弹性的能力;
- the ability to restore the availability and access to personal data in a timely manner in the event of a physical or technical incident; 在发生物理或技术事件时,及时恢复个人数据的可用性和访问的能力;
- a process for regularly testing, assessing and evaluating the effectiveness of technical and organisational measures for ensuring the security of the processing 定期测试、评估和评价确保处理安全的技术和组织措施的有效性的过程
- 【关于inter alia,详情可以看interalia在法律文件中的使用及译法 (baidu.com),拉丁语,可以理解为“其中”的意思】
Information Obligation
- Article 33 creates a legal a duty on all organisations to report certain types of personal data breach to the relevant supervisory authority 第33条规定,所有组织都有法律义务向相关监管机构报告某些类型的个人数据泄露
- within 72 hours of becoming aware of the breach, where feasible 在可能的情况下,在72小时内发现该漏洞
- Article 34 requires the controller to notify data subjects affected or potentially affected by breach 第34条要求控制者通知受违约影响或可能受违约影响的数据主体
Data Breach 数据外泄
Data breach is a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data
数据泄露是指违反安全导致意外或非法破坏、丢失、更改、未经授权披露或访问个人数据
- This includes breaches that are the result of both accidental and deliberate causes 这包括意外和故意原因造成的违约
- A security incident that has affected the confidentiality, integrity or availability of personal data 影响个人资料的机密性、完整性或可用性的安全事件
When a personal data breach has occurred, organisations need to establish the likelihood and severity of the resulting risk to people’s rights and freedoms
当发生个人数据泄露时,组织需要确定由此对人们的权利和自由造成风险的可能性和严重程度
- Likelihood of risk –> need to report it 有风险的可能性- >需要报告
- No likelihood of risk –> no need to report it 风险的可能性- >需要报告
The adverse affect of a security incident on individuals may include emotional distress, and physical and material damage
安全事件对个人的不利影响可能包括情绪困扰、身体和物质损害
Contract Law相关
GDPR Article 28 states that controllers must include in contracts with processors
GDPR第28条规定,控制者必须在与处理者的合同中包括
- The processor shall not engage another processor without prior specific or general written authorisation of the controller 未经控制者事先明确或一般书面授权,处理者不得与其他处理者接触
- Processing by a processor shall be governed by a contract or other legal act 处理者的处理应受合同或其他法律行为的约束
- Sets out the subject-matter and duration of the processing, the nature and purpose of the processing, the type of personal data and categories of data subjects and the obligations and rights of the controller 列明处理的主题事项和持续时间、处理的性质和目的、个人数据的类型和数据主体的类别,以及控制者的义务和权利
NIS Directive 2
Introduction
NIS Directive 2 regulates the cybersecurity of critical national infrastructure, and updates the previous version
NIS指令2规范了关键国家基础设施的网络安全,并更新了之前的版本
- It covers more sectors and activities than before, streamlines reporting obligations and addresses supply chain security 它涵盖了比以前更多的部门和活动,简化了报告义务,并解决了供应链安全问题
It applies to providers of critical national infrastructure (CNI):
它适用于关键国家基础设施(CNI)的提供商:
- Operators of essential services (OES), which are directly responsible for CNI 直接负责CNI的基本服务(OES)运营商
- Digital service providers (DSPs), which provide services upon which others, including OES, are reliant 数字服务提供商(dsp),提供其他人(包括OES)依赖的服务
Scope
Operators of essential services (OES) provide a listed service in one of seven critical infrastructure sectors, and energy, transport, banking, financial markets, health, drinking water, and digital infrastructure
基本服务(OES)运营商在能源、交通、银行、金融市场、卫生、饮用水和数字基础设施等七个关键基础设施领域之一提供所列服务
they operate on such a scale that their service is “essential for the maintenance of critical societal and economic activities”
它们的运作规模如此之大,以至于它们的服务“对于维持关键的社会和经济活动至关重要”。
Digital service is a new subset of the category of service known as ‘information society services’ which is any service normally provided for remuneration, at a distance, by electronic means and at the individual request of a recipient of services
数字服务是被称为“信息社会服务”的服务类别的一个新子集,它是指通常通过电子手段并应服务接受者的个人要求提供的有偿服务
Digital service providers (DSPs) are: 数码服务供应商包括:
- an online marketplace; 在线市场
- an online search engine; or 在线搜索引擎
- a cloud computing service 云计算服务
Tort Law
A private law mechanism
私法机制
Data controllers can be held liable under the tort of negligence for damages caused by cybersecurity incidents that they should have reasonably foreseen and prevented or mitigated
根据过失侵权法,数据控制者可能对他们本应合理预见、预防或减轻的网络安全事件造成的损害承担责任
To hold data controllers liable, a court would have to find that (i) the operator had a duty of care to the person(s) who suffered harm which (ii) the operator failed to fulfil
为了让数据控制者承担责任,法院必须认定(i)运营者对遭受伤害的人负有注意义务,而(ii)运营者未能履行
Requirement
Duty – breach – causation – harm
义务-违约-因果-损害
A duty of care may arise from:
- common law principles governing negligence 管辖过失的普通法原则
- a special / contractual relationship between the defendant and the claimant 被告与索赔人之间的特殊/合同关系
- from a statute or regulation governing a specific activity 来自管理某一特定活动的法令或规章
There must be a proximity between the parties for a duty of care to exist
为了注意义务的存在,当事人之间必须有接近性
Foreseeability means that a person can be held liable only when they should reasonably have foreseen that their negligent act would imperil others
可预见性意味着只有当一个人合理地预见到自己的过失行为会危及他人时,他才能承担责任
Damage needs to be proven by claimants – economic loss or emotional harm
损害需要由索赔人证明——经济损失或精神伤害
接下来是US的内容
Privacy and data protection - 1. HIPAA - US Health Insurance Portability and Accountability Act (health information privacy)
Personal health information is considered very sensitive
个人健康信息被认为非常敏感
- Confidential medical records 保密医疗记录
- Public embarrassment, discrimination 公众尴尬、歧视
- Medical identity theft - 医疗卡盗用
HIPAA protects privacy and security of personal health information
HIPAA保护个人健康信息的隐私和安全
Scope
Privacy and Security rules apply to covered entities and determine how they may create, store, use or disclose protected health information (PHI)
隐私和安全规则适用于所涵盖的实体,并确定它们如何创建、存储、使用或披露受保护的健康信息(PHI)。
- Applies information security principles established in other industries 应用在其他行业建立的信息安全原则
Definitions
PHI is any individually identifiable information about the health of the person, including past, present or future mental or physical health information
PHI是关于个人健康的任何可识别信息,包括过去、现在或未来的精神或身体健康信息.
Covered entities are those that handle PHI in a certain way – health plans, health care providers, health insurance companies, etc.
涉及实体是那些以某种方式处理PHI的实体——健康计划、医疗保健提供者、健康保险公司等。
It also applies to business associates of covered entities
它也适用于所涵盖实体的业务伙伴
Security Rule
Covered Entity must “implement policies and procedures to prevent, detect, contain and correct security violations.”
涉及实体必须“实施策略和程序来防止、检测、包含和纠正安全违规行为”。
The Security rule requires covered entities to use security safeguards, which must protect the confidentiality, integrity and availability of electronic protected health information (EPHI) from reasonably anticipated threats
安全规则要求所涵盖的实体使用安全保障措施,这些措施必须保护受电子保护的健康信息(EPHI)的机密性、完整性和可用性,使其免受合理预期的威胁
Security Rule Standards
The Security Rule contains instructions how to use information security safeguards
安全规则包含如何使用信息安全保障措施的说明
Also contains standards, which are required to be met for each safeguard area
安全规则包含如何使用信息安全保障措施的说明
Detailed instructions for meeting the standards are implementation specifications (IS)
满足标准的详细说明见实施规范(IS)。
Implementation Specifications(IS)
Required specifications – compulsory
所需规范 - 强制性
Addressable specifications – covered entities decide whether it is reasonable and appropriate to the particular environment and the cost to implement these
可寻址规范-涉及 实体决定其是否合理和适合特定环境以及实现这些规范的成本
Covered entity can either 涉及实体可以
- Implement the IS as published 按照发布的IS实施
- Implement some alternative (and document why) 实现一些替代方案(并记录原因)
- Not implement the IS at all (and document why) 根本没有实现IS(并记录原因)
Types of Safeguards - 三种
Administrative Safeguards 管理保障措施
- Actions, policies and procedures to prevent, detect, contain and correct information security violations 防止、检测、控制和纠正信息安全违规行为的行动、政策和程序
- The largest part of the Rule is the management process 规则中最重要的部分是管理过程
Physical Safeguards 实体防护
- Controls to protect physical resources 控制保护实体资源
Technical Safeguards 技术保障措施
- Controls applied in the hardware and software on an information system 在信息系统的硬件和软件上应用的控制
2. COPPA - Children’s Online Privacy Protection Act
Scope
Sectoral approach, the law is derived partly from federal statute, but also from state law, case law and increasingly from the decisions and guidance of the Federal Trade Commission (FTC)
部门方法,法律部分来自联邦法规,但也来自州法、判例法,越来越多地来自联邦贸易委员会(FTC)的决定和指导。
**Children’s Online Privacy Protection Act **(COPPA) requires that operators of commercial websites and online services directed to children under the age of 13, or general audience websites and online services that knowingly collect personal information from children under 13, must obtain parental consent before collecting, using, or disclosing any personal information from children under the age of 13
儿童在线隐私保护法(COPPA)要求针对13岁以下儿童的商业网站和在线服务的运营商,或故意收集13岁以下儿童个人信息的一般受众网站和在线服务的运营商,在收集、使用或披露13岁以下儿童的任何个人信息之前,必须获得父母的同意
In 2011, the FTC and the games company Playdom agreed to a $3 million settlement over Playdom’s alleged breaches of the Children’s Online Privacy Act
2011年,美国联邦贸易委员会与游戏公司Playdom就Playdom涉嫌违反《儿童在线隐私法》达成300万美元的和解协议
In 2019, Google’s YouTube paid $170 million to settle allegations by the FTC and the New York attorney general for illegally collecting personal information from children without their parents’ consent; the highest settlement yet
2019年,谷歌旗下的YouTube支付了1.7亿美元,以了结美国联邦贸易委员会和纽约总检察长对其未经父母同意非法收集儿童个人信息的指控;迄今为止最高的和解金额
3. CCPA - California Consumer Privacy Act
**California Consumer Privacy Act **(CCPA) came into effect in January 2020 – the most comprehensive privacy legislation to-date
加州消费者隐私法案(CCPA)于2020年1月生效,这是迄今为止最全面的隐私立法
*Personally identifiable information *(PII) includes any information that identifies, relates to, describes, is capable of being associated with, or could reasonably be linked, directly or indirectly, with a particular consumer or household (under the CCPA)
个人身份信息(PII)包括识别、涉及、描述、能够与特定消费者或家庭直接或间接关联或可以合理关联的任何信息(根据CCPA)
Applies to any business that collects or processes PII from California residents, and
适用于从加州居民收集或处理个人身份信息的任何企业,以及
- has annual gross revenues of $25,000,000 or more; 年总收入在2500万美元或以上;
- buys, collects, sells, shares, or otherwise receives the PII of 50,000 or more California consumers per year, households or devices; OR 每年购买、收集、出售、共享或以其他方式接收50,000或更多加州消费者、家庭或设备的PII;或
- derives at least 50% of its revenue from selling consumers’ personal information This will most likely capture most apps or free-to-play games 至少有50%的收益来自于销售用户的个人信息,这很可能会吸引大多数应用或免费游戏
Breach Notification Laws 违约通知法
Legislation adopted in 47 US states requiring private or governmental entities to notify individuals of security breaches of information involving personally identifiable data
美国47个州通过立法,要求私人或政府实体在涉及个人身份数据的信息安全漏洞时通知个人
Provisions include: 规定包括
- who must comply with the law (businesses, data/ information brokers, government entities); 谁必须遵守法律(企业、数据/信息经纪人、政府实体);
- definitions of ‘personal information’ (name combined with SSN, drivers license or state ID, account numbers); “个人信息”的定义(姓名与社会安全号码、驾驶执照或州身份证、账号的组合);
- what constitutes a breach (unauthorized acquisition of data); 什么构成违规(未经授权获取数据);
- requirements for notice (timing or method of notice, who must be notified) 通知要求(通知的时间或方法,必须通知谁)
FTC - Federal Trade Commission Act
Consumer Protection Regulations
消费者保障条例
FTC is an independent federal agency and the most important regulatory authority for consumer protection issues
联邦贸易委员会是一个独立的联邦机构,也是消费者保护问题最重要的监管机构
Section 5 forbids unfair and deceptive trade practices
第5条禁止不公平和欺骗性的贸易行为
The FTC has now brought over 50 information security cases
联邦贸易委员会目前已经提起了50多起信息安全案
Scope
Unfair 不公平
- Causes or likely to cause substantial harm/injury to consumer 对消费者造成或可能造成重大损害/伤害的
- Consumer cannot reasonably avoid the harm 消费者不能合理地避免伤害
- There is not a benefit to the practice that outweighs the harm 这种做法的利大于弊
Deceptive 欺骗性
- Representation or omission likely to mislead the consumer 可能误导消费者的陈述或遗漏
- Not reasonable from the perspective of the consumer 从消费者的角度来看是不合理的
- Affects consumer’s decision; harm as otherwise, likely another decision 影响消费者决策;伤害,否则,可能是另一个决定
Priorities 优先处理的事
Children Under 18: Harmful conduct directed at children under 18 has been a source of significant public concern, now, FTC staff will similarly be able to expeditiously investigate any allegations in this important area
** 18岁以下儿童**:针对18岁以下儿童的有害行为一直是公众关注的一个重要来源,现在,联邦贸易委员会的工作人员将同样能够迅速调查这一重要领域的任何指控
Algorithmic and Biometric Bias*: *Allows staff to investigate allegations of bias in algorithms and biometrics
算法和生物识别偏见*:*允许员工调查算法和生物识别偏见的指控
Deceptive and Manipulative Conduct on the Internet: This includes, but is not limited to, the “manipulation of user interfaces,” including but not limited to dark patterns, also the subject of a recent FTC workshop
互联网上的欺骗和操纵行为:这包括但不限于“用户界面的操纵”,包括但不限于黑暗模式,这也是最近FTC研讨会的主题
Limitations
In April 2021, the Supreme Court ruled in AMG Capital Mgmt., LLC v. FTC that the agency lacks power to seek monetary recovery under Section 13 of the FTC Act
2021年4月,最高法院对AMG资本管理公司一案做出了裁决。诉联邦贸易委员会,根据联邦贸易委员会法案第13条,该机构缺乏寻求金钱赔偿的权力
- To be rectified by the Congress? 要被国会纠正吗?
Lack of technical expertise and staff to regulate consumer cybersecurity
缺乏管理消费者网络安全的技术专长和人员
The ideal solution is for Congress to create a robust cybersecurity framework and an agency empowered to enforce it
理想的解决方案是国会建立一个健全的网络安全框架,并授权一个机构来执行它
For the time being, FTC fills a void in America’s cybersecurity ecosystem
目前,FTC填补了美国网络安全生态系统的空白
Tort Law
侵权法:一种民事法律制度,用于处理因他人的过失或不法行为而造成的损害赔偿问题。
Information security lawsuits include claims of negligence, **breach of fiduciary duty **or breach of contract, individually or together, are common
信息安全诉讼包括疏忽,违反信义义务或违反合同的索赔,单独或一起,是常见的
**Negligence **is generally defined as a breach of the duty not to impose an unreasonable risk on society
玩忽职守一般定义为违反不给社会带来不合理风险的义务
**Breach of fiduciary duty **is a failure to fulfil an obligation to act in the best interest of another party
违反信义义务是指未能履行为另一方的最佳利益行事的义务
Some recent cases have argued that data breaches are subject to strict liability
最近的一些案例认为,数据泄露需要承担严格的责任
**Strict liability **means that the manufacturer of a product is automatically responsible for any injuries caused by the product (typically product liability cases)
严格责任是指产品制造商自动对产品造成的任何伤害负责(通常是产品责任案件)。
Negligence 玩忽职守
To establish a claim, plaintiff has to prove:
要提出索赔,原告必须证明:
- the existence of a legal duty on the part of the defendant not to expose the plaintiff to unreasonable risks 被告负有不使原告面临不合理风险的法律义务
- a breach of the duty – a failure on the part of the defendant as act reasonably, 违反义务-被告一方未能“合理”行事
- a causal connection between defendant’s conduct and plaintiff’s harm and 被告的行为与原告的伤害之间存在因果关系
- actual damage to the plaintiff resulting from the defendant’s negligence 由于被告的过失而对原告造成的实际损害
Negligence – Foreseeability 可预见性
Central concept of the law of negligence
过失侵权法的核心概念
A person can be held liable only when they should reasonably have foreseen that their negligent act would imperil others
一个人只有在合理地预见到自己的过失行为会危及他人的时候才能被追究责任
A database owner fails to patch a security vulnerability, thereby paving the way for a cyber attacker to obtain unauthorized access to confidential information
数据库所有者未能修补安全漏洞,从而为网络攻击者未经授权访问机密信息铺平了道路
Negligence - Cases
In Anderson v. Hannaford Brothers Co., a third party stole a grocery store’s debit and credit card data, and the court used a negligence standard to assert a standard of care based on breach of implied contract
安德森诉汉纳福德兄弟公司案。在美国,第三方窃取了杂货店的借记卡和信用卡数据,法院使用过失标准来主张基于违反默示合同的注意标准
In Patco Construction Co. v. People’s United Bank, the bank had a state-of-the-art security program, but failed to set the fraud activity triggers at an appropriate level
在Patco Construction Co.诉People 's United Bank案中,该银行拥有最先进的安全程序,但未能将欺诈活动触发器设置在适当的级别
Fiduciary Duty
受托责任:一种法律义务,要求承担受托责任的人(如律师、银行家、公司董事等)在处理他人财产或事务时,必须诚实、忠实、谨慎地行事,以保护受益人的利益
Special relationships – between a provider and consumer, employer and employee, or fiduciary and beneficiary – is usually based on a contractual promise (explicit or implied)
特殊关系——提供者和消费者、雇主和雇员、受托人和受益人之间的关系——通常基于合同承诺(明示或暗示)。
Corporations owe fiduciary and good faith duties to shareholders to obey the scope of powers, be diligent and act for corporation’s interests
公司对股东负有信义和诚信义务,必须遵守职权范围,勤勉尽责,为公司利益而行动
To establish a claim, plaintiff has to prove:
要提出索赔,原告必须证明:
- the existence of a binding agreement; 有约束力的协议的存在
- the non-breaching party fulfilled its obligations, if it had any; 非违约方履行了自己的义务(如果有的话)
- the breaching party failed to fulfil obligations; 违约方未履行义务的;
- the lack of a legal excuse; and 缺乏合法的借口
- the existence of damages sustained due to the breach 由于违约而遭受损害的存在
Tort Law – Statutes II 章程
A statute may impose a duty of care for how entities use or limit access to personal information in the normal course of business
对于实体在正常业务过程中如何使用或限制对个人信息的访问,法规可能会规定注意义务
Statutes 法规
- Fair Credit Reporting Act 公平信赖报告法案
In *Equifax *data breach, the Fair Credit Reporting Act imposes a specific statutory duty to maintain reasonable procedure to ensure information security and failure to do so creates civil liability for non- compliance
在Equifax数据泄露事件中,《公平信用报告法》规定了维护合理程序以确保信息安全的具体法定义务,否则将因不遵守规定而承担民事责任
Tort Law – Harm
Actual harm is the most straightforward
实际的伤害是最直接的
Concrete and particularized injury that is actual or imminent, not conjectural or hypothetical
实际的或即将发生的具体的和特殊的伤害,而不是推测的或假设的
Problematic for cases of data breaches
在数据泄露的情况下是有问题的
Theory of ‘future harm’ establishing a threat of future identity theft
“未来伤害”理论建立了未来身份盗窃的威胁
Harm的cases
In these cases, the hackers intentionally targeted the personal information compromised in the data breaches – evidence of harm
在这些情况下,黑客故意针对数据泄露中受损的个人信息-伤害的证据
- In *Galaria (hackers broke into Nationwide’s computer network and stole the personal information of 1.1 million customers), 在Galaria *(黑客侵入了全国保险公司的计算机网络,窃取了110万客户的个人信息),
- In *Remijas (why else would hackers break into a store’s database and steal consumers’ private information?) 在Remijas *(否则为什么黑客会闯入商店的数据库并窃取消费者的私人信息?)
- In *Pisciotta (scope and manner of intrusion into banking website’s hosting facility was sophisticated, intentional and malicious), 在Pisciotta *中(入侵银行网站托管设施的范围和方式是复杂的、故意的和恶意的),
On the other hand, in *Katz *and *Beck *the claims were too speculative, there was no evidence that the stolen information has been accessed or misused or that they have suffered identity theft
另一方面,在*Katz 和Beck *中,这种说法过于推测,没有证据表明被盗信息已被访问或滥用,也没有证据表明他们遭受了身份盗窃
Contract Law
Breach of contract is the failure to fulfil a condition of a contract
违反合同是指没有履行合同的条件
Data breach claims – written agreement or privacy policy or that state consumer protection laws create an implied contract
数据泄露索赔-书面协议或隐私政策或州消费者保护法创建的隐含合同
COPPA, HIPAA, and others require contracts with processors, other third parties with obligations to ensure that information is kept secure
COPPA、HIPAA和其他要求与处理者、其他有义务确保信息安全的第三方签订合同
The Massachusetts Data Security Regulations addresses the selection of third-party vendors, requiring companies to take *reasonable *steps to select and retain vendors that have the capacity to maintain appropriate security measures for personal information
《马萨诸塞州数据安全条例》涉及第三方供应商的选择,要求公司采取“合理”步骤选择并保留有能力为个人信息维护适当安全措施的供应商
Vendors also must be contractually required to maintain safeguards
供应商还必须按照合同要求维护保障措施
The Payment Card Industry Data Security Standard (PCI DSS) is a proprietary information security standard for organizations that handle branded credit cards from the major card schemes including Visa, MasterCard, American Express, Discover, and JCB
支付卡行业数据安全标准(PCI DSS)是一个专有的信息安全标准,适用于处理来自主要信用卡方案(包括Visa、MasterCard、American Express、Discover和JCB)的品牌信用卡的组织
Control objectives: 控制目标
- Build and maintain a secure network and systems 建立和维护一个安全的网络和系统
- Protect cardholder data 保护持卡人资料
- Maintain a vulnerability management program 维护一个漏洞管理程序
- Implement strong access control measures 实施强有力的访问控制措施
- Regularly monitor and test networks 定期监控和测试网络
- Maintain an information security policy 维护信息安全策略
接下来是China的内容
PRC Cybersecurity Law
Provides for supervisory jurisdiction over cyberspace, defines security obligations for network operators and enhances the protection over personal information
明确网络空间监管权限,明确网络运营者的安全义务,加强对个人信息的保护
It also establishes a regulatory regime in respect of critical information infrastructure and imposes data localization requirements for certain industries
条例亦就关键资讯基建设立规管制度,并规定某些行业的数据本地化规定
Network operators must adopt technological measures and other necessary measures to ensure the security of personal information they gather, and prevent personal information from being leaked, destroyed or lost
网络运营者必须采取技术措施和其他必要措施,确保所收集的个人信息安全,防止个人信息泄露、破坏或者丢失
Network operators are subject to the following requirements when collecting and using personal information:
网络运营者在收集和使用个人信息时,应当遵守以下要求:
- Collection and use of personal information must be legal, proper and necessary. 收集和使用个人信息必须合法、适当和必要。
- Network operators must clearly state the purpose, method, and scope of collection and use, and obtain consent from the person whose personal information is to be collected; personal information irrelevant to the service provided shall not be collected. 网络运营者必须明确收集、使用个人信息的目的、方法和范围,并征得被收集人的同意;不收集与所提供服务无关的个人信息。
- Network operators shall not disclose, alter, or destroy collected personal information; without the consent of the person from whom the information was gathered, such information shall not be provided to others. 网络运营者不得泄露、篡改、销毁收集到的个人信息;未经被收集人同意,不得向他人提供该信息。
- In the event of a data breach or a likely data breach, network operators must take remedial actions, promptly inform users, and report to the competent government agencies according to relevant regulations. 在发生数据泄露或者可能发生数据泄露的情况下,网络运营商必须采取补救措施,及时通知用户,并按照有关规定向政府主管部门报告。
- In case of an illegal or unauthorized collection and use of personal information, a person is entitled to ask a network operator to delete such personal information; when information collected is wrong, an individual can request correction. 非法或者未经授权收集、使用个人信息的,有权要求网络运营者删除个人信息;当收集到的信息有误时,个人可以要求更正。
Operators of Critical Information Infrastructure 关键信息基础设施运营商
Regulators and law enforcement have wide discretionary powers to review and inspect the IT systems of companies
监管机构和执法部门拥有广泛的自由裁量权,可以审查和检查企业的IT系统
CSL requires critical information infrastructure operators in important sectors to fulfil certain security protection obligations
《信息安全法》要求重要行业的关键信息基础设施运营者履行一定的安全保护义务
There is no definition yet of which organisations qualify as operators of critical information infrastructure
目前还没有关于哪些组织有资格成为关键信息基础设施运营商的定义
The Civil Code
‘Personal information’ is defined as all kinds of information recorded by electronic or otherwise that can be used to independently identify or be combined with other information to identify specific natural persons, including the natural persons’ names, dates of birth, ID numbers, biometric information, addresses, telephone numbers, email addresses, health information, whereabouts, etc.
“个人信息”是指以电子或其他方式记录的可用于独立识别或与其他信息结合识别特定自然人的各种信息,包括自然人的姓名、出生日期、身份证号码、生物特征信息、地址、电话号码、电子邮件地址、健康信息、行踪等。
The Specification makes minor wording changes to the definition of ‘personal information’ under the CSL and the Civil Code
该规范对《个人信息法》和《民法典》中“个人信息”的定义进行了细微的措辞修改
It also defines the ‘personal sensitive information’ as personal information that may cause harm to personal or property security, or is very likely to result in damage to an individual’s personal reputation or physical or mental health or give rise to discriminatory treatment, once it is leaked, unlawfully provided or abused
它还将"个人敏感信息"定义为一旦泄露、非法提供或滥用,可能对人身或财产安全造成损害,或极有可能对个人声誉或身心健康造成损害,或造成歧视待遇的个人信息
Data Localization
**Personal Information Protection Law (PIPL) **sets out a stricter data localization requirement, requiring that personal information processed by state organs, critical information infrastructure operators (not yet defined), and data processors that have reached or exceeded the personal information processing threshold, shall be stored inside China or undergo risk assessment by the National Cyberspace Administration or related departments when cross-border data transfer is required
**《个人信息保护法》**提出了更严格的数据本地化要求,要求国家机关、关键信息基础设施运营者(未明确定义)、数据处理者处理的个人信息,达到或超过个人信息处理阈值的,在需要跨境数据传输时,应当存储在中国境内,或者由国家网信办或相关部门进行风险评估
To comply with this law, many US and EU companies have been taking compliance measures, such as segregating local Chinese data from other data. Various companies have also started offering cloud services (including Microsoft and Amazon Web Services) in China to meet the business needs of multinational companies doing business in China
为了遵守这一法律,许多美国和欧盟公司一直在采取合规措施,例如将中国本地数据与其他数据隔离开来。许多公司也开始在中国提供云服务(包括微软和亚马逊网络服务),以满足在中国开展业务的跨国公司的业务需求
Who owns personal information?
China has not had a specific stipulation on the ownership of personal information, and it has been disputed whether personal information belongs to the relevant personal information subjects
中国对个人信息的所有权没有具体规定,个人信息是否属于相关个人信息主体一直存在争议
The Civil Code stipulates the protection of personal information in the 'Personality Rights’ Chapter, indicating that the rights pertaining to personal information are personality rights of the personal information subjects
《民法典》在“人格权”一章中对个人信息的保护进行了规定,表明与个人信息有关的权利是个人信息主体的人格权
Telecommunications / ISP Law
**The Provisions on Telecommunication and Internet User Personal Information Protection, **effective from September 1, 2013
**《电信和互联网用户个人信息保护规定》**自2013年9月1日起施行
It is applicable to telecommunications and Internet service providers
适用于电信和互联网服务提供商
Duty to keep information in proper custody, mitigate harms from actual or suspected disclosure, breach (actual or suspected) notification obligation
有责任妥善保管信息,减轻因实际或疑似披露、违反(实际或疑似)通知义务而造成的损害
Article 13 imposes the following information security requirements on telecommunications operators and Internet service providers:
第十三条对电信经营者和互联网服务提供者规定了下列信息安全要求:
- Specify the responsibilities of each department / role in terms of security of personal information; 订明各部门/角色在个人资料保安方面的责任;
- Establish the authority of different staff members and agents, review the export, duplication and destruction of information, and take measure to prevent the leak of confidential information; 建立不同工作人员和代理人的权限,审查信息的输出、复制和销毁,并采取措施防止机密信息泄露;
- Properly retain the carriers that record users’ personal information, such as hard-copy media, optical media and magnetic media, and take appropriate secure storage measures; 妥善保管记录用户个人信息的硬拷贝介质、光介质、磁介质等载体,并采取相应的安全存储措施;
- Conduct access inspections of the information systems that store users’ personal information, and put in place intrusion prevention, anti-virus and other measures; 对存储用户个人信息的信息系统进行访问检查,并实施入侵防御、防病毒等措施;
- Record operations performed with users’ personal information, including the staff members who perform such operations, the time and place of such operations and the matters involved; 记录使用用户个人信息进行的操作,包括执行操作的人员、操作的时间、地点和涉及的事项;
- Undertake communications network security protection work as required by the relevant telecommunications authority 依电信主管机关之要求,承担通讯网络之安全保护工作
Breach Notification Law
The *PRC Cybersecurity Law *introduced a general requirement for the reporting and notification of actual or suspected personal information breaches
《中华人民共和国网络安全法》引入了报告和通知实际或疑似个人信息泄露的一般要求
Where personal information is leaked, lost or distorted (or if there is a potential for such incidents), organizations must promptly take relevant measures to mitigate any damage and notify relevant data subjects and report to relevant government agencies in a timely manner in accordance with relevant provisions
当个人信息被泄露、丢失或扭曲(或有可能发生此类事件)时,组织必须立即采取相关措施减轻损害,并根据相关规定及时通知相关数据主体并向相关政府机构报告
The *PIS Specification *provide detailed guidance on reporting and notification of personal data breaches or security incidents
个人资料保安服务规范就报告及通知个人资料外泄或保安事件提供详细指引
Consumer Protection Law
The PRC Consumer Rights Protection Law, effective from March 15, 2014, contains data protection obligations which are applicable to all types of businesses that deals with consumers:
**自2014年3月15日起生效的《中华人民共和国消费者权益保护法》**包含了适用于与消费者打交道的各类企业的数据保护义务:
- State the purpose, method, scope, and rules of collection of personal information of consumers; 规定收集消费者个人信息的目的、方法、范围和规则;
- Keep personal information of consumers confidential and not disclose, sell, or illegally provide this to others; 对消费者的个人信息保密,不得泄露、出售或者非法提供给他人;
- Have mechanisms in place to ensure the security of information collected; and 设立机制确保所收集资料的安全
- Not send unsolicited communications to consumers 不向消费者发送未经请求的通信
自我介绍一下,小编13年上海交大毕业,曾经在小公司待过,也去过华为、OPPO等大厂,18年进入阿里一直到现在。
深知大多数网络安全工程师,想要提升技能,往往是自己摸索成长,但自己不成体系的自学效果低效又漫长,而且极易碰到天花板技术停滞不前!
因此收集整理了一份《2024年网络安全全套学习资料》,初衷也很简单,就是希望能够帮助到想自学提升又不知道该从何学起的朋友。
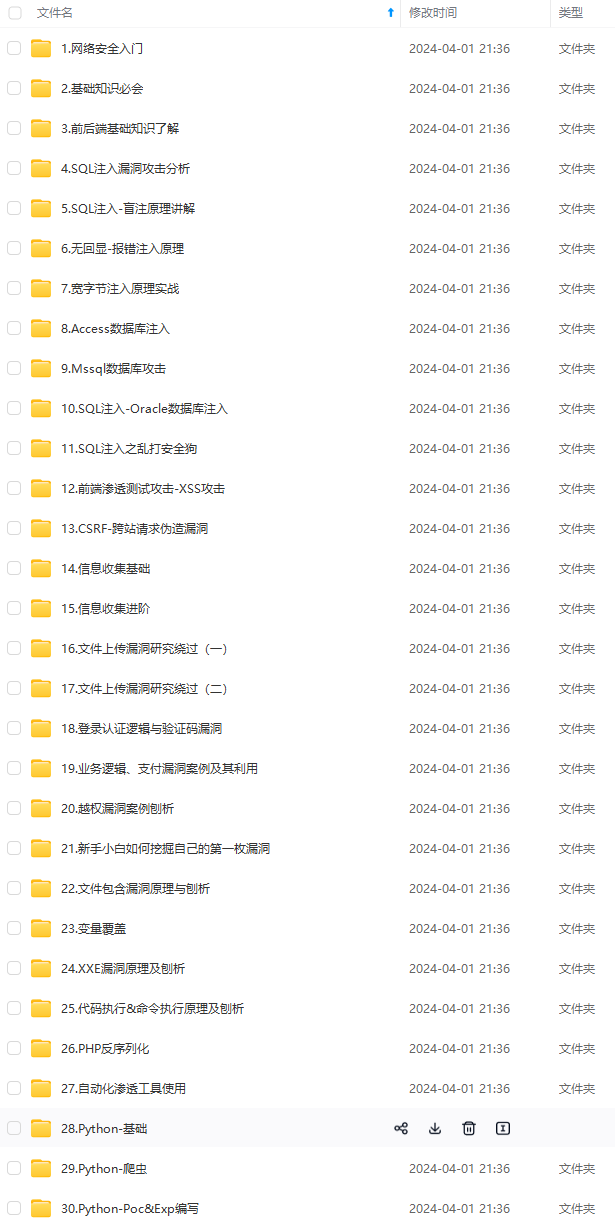
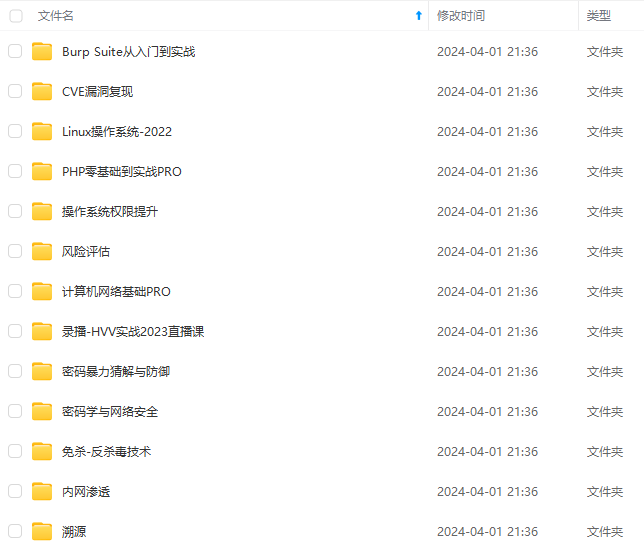
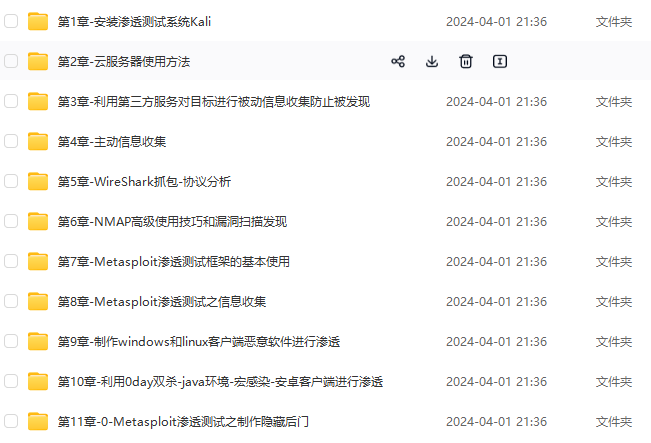
既有适合小白学习的零基础资料,也有适合3年以上经验的小伙伴深入学习提升的进阶课程,基本涵盖了95%以上网络安全知识点,真正体系化!
由于文件比较大,这里只是将部分目录大纲截图出来,每个节点里面都包含大厂面经、学习笔记、源码讲义、实战项目、讲解视频,并且后续会持续更新
如果你觉得这些内容对你有帮助,可以添加VX:vip204888 (备注网络安全获取)

学习路线:
这个方向初期比较容易入门一些,掌握一些基本技术,拿起各种现成的工具就可以开黑了。不过,要想从脚本小子变成黑客大神,这个方向越往后,需要学习和掌握的东西就会越来越多以下是网络渗透需要学习的内容:
一个人可以走的很快,但一群人才能走的更远。如果你从事以下工作或对以下感兴趣,欢迎戳这里加入程序员的圈子,让我们一起学习成长!
AI人工智能、Android移动开发、AIGC大模型、C C#、Go语言、Java、Linux运维、云计算、MySQL、PMP、网络安全、Python爬虫、UE5、UI设计、Unity3D、Web前端开发、产品经理、车载开发、大数据、鸿蒙、计算机网络、嵌入式物联网、软件测试、数据结构与算法、音视频开发、Flutter、IOS开发、PHP开发、.NET、安卓逆向、云计算
因此收集整理了一份《2024年网络安全全套学习资料》,初衷也很简单,就是希望能够帮助到想自学提升又不知道该从何学起的朋友。
[外链图片转存中…(img-lr3D66lp-1712383871022)]
[外链图片转存中…(img-qTxNT0Rl-1712383871023)]
[外链图片转存中…(img-bKGsHgll-1712383871023)]
[外链图片转存中…(img-TopzbsnQ-1712383871023)]
[外链图片转存中…(img-HjrBOZOd-1712383871024)]
[外链图片转存中…(img-2JPn4Hcw-1712383871024)]
既有适合小白学习的零基础资料,也有适合3年以上经验的小伙伴深入学习提升的进阶课程,基本涵盖了95%以上网络安全知识点,真正体系化!
由于文件比较大,这里只是将部分目录大纲截图出来,每个节点里面都包含大厂面经、学习笔记、源码讲义、实战项目、讲解视频,并且后续会持续更新
如果你觉得这些内容对你有帮助,可以添加VX:vip204888 (备注网络安全获取)
[外链图片转存中…(img-Viy3GdUR-1712383871024)]
学习路线:
这个方向初期比较容易入门一些,掌握一些基本技术,拿起各种现成的工具就可以开黑了。不过,要想从脚本小子变成黑客大神,这个方向越往后,需要学习和掌握的东西就会越来越多以下是网络渗透需要学习的内容:

一个人可以走的很快,但一群人才能走的更远。如果你从事以下工作或对以下感兴趣,欢迎戳这里加入程序员的圈子,让我们一起学习成长!
AI人工智能、Android移动开发、AIGC大模型、C C#、Go语言、Java、Linux运维、云计算、MySQL、PMP、网络安全、Python爬虫、UE5、UI设计、Unity3D、Web前端开发、产品经理、车载开发、大数据、鸿蒙、计算机网络、嵌入式物联网、软件测试、数据结构与算法、音视频开发、Flutter、IOS开发、PHP开发、.NET、安卓逆向、云计算
